How can we help you today?
Granular Permission settings on Shares
Contents
SMB with Active Directory Identity
MyWorkDrive Server Version 6 introduced granular permissions on shares, to provide additional flexibility to administrators to manage how users access shared files and documents. It provides settings for Clients, Files/Documents (via DLP), and Invited Guest Users.
When a box is not checked on the permissions matrix, the users or groups who do not have the checkmark will not be able to use that function – login via that client, download files, etc.
Not all permissions will always appear on share details. For example, the Download and Office Online Edit options require DLP to be enabled in Enterprise Settings, and the master settings set at the top of share details to be enabled.
The option to enable/disable users/groups for the MyWorkDrive Clients and Guest User Access will not be displayed if the corresponding features are disabled or not configured.
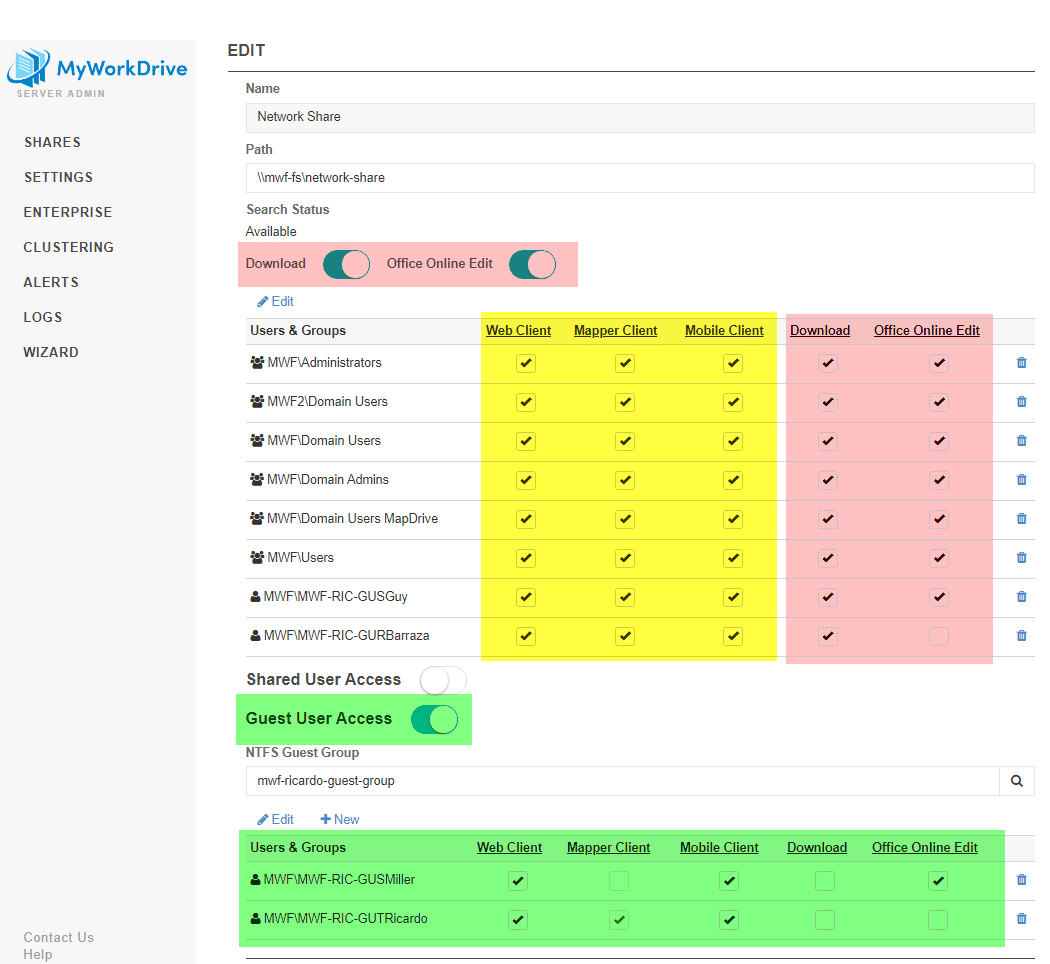
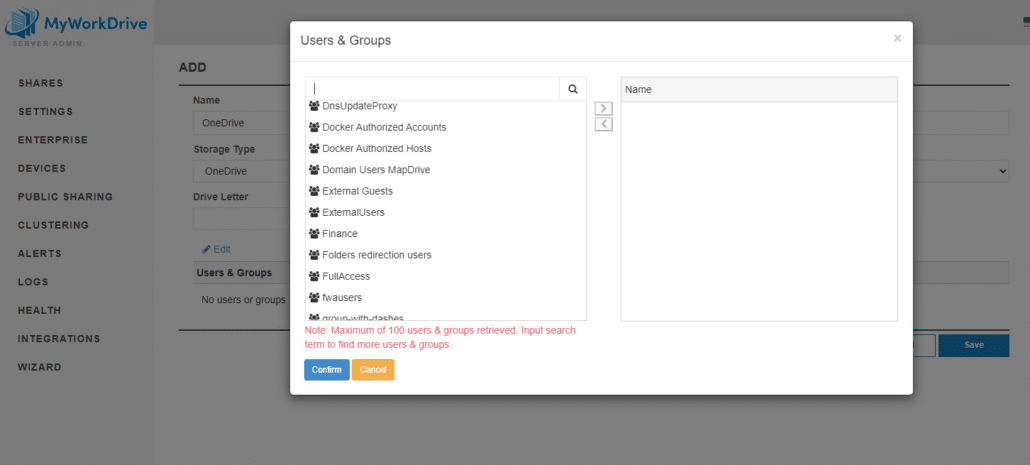
Granular Permissions are shown when editing a share in share details, and share details have been revised to improve usability.
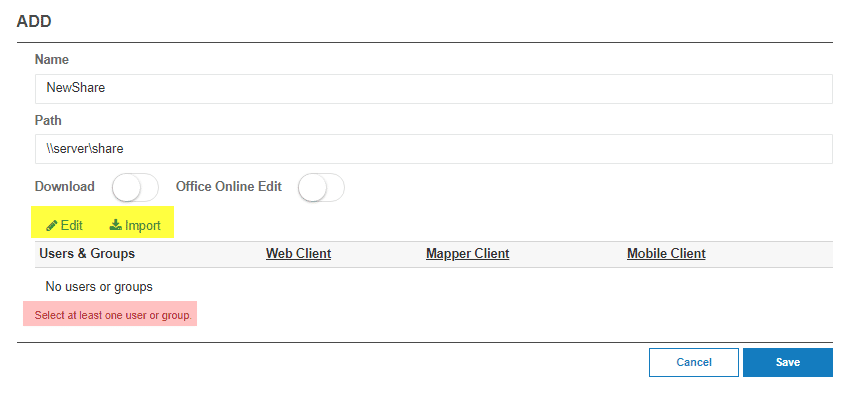
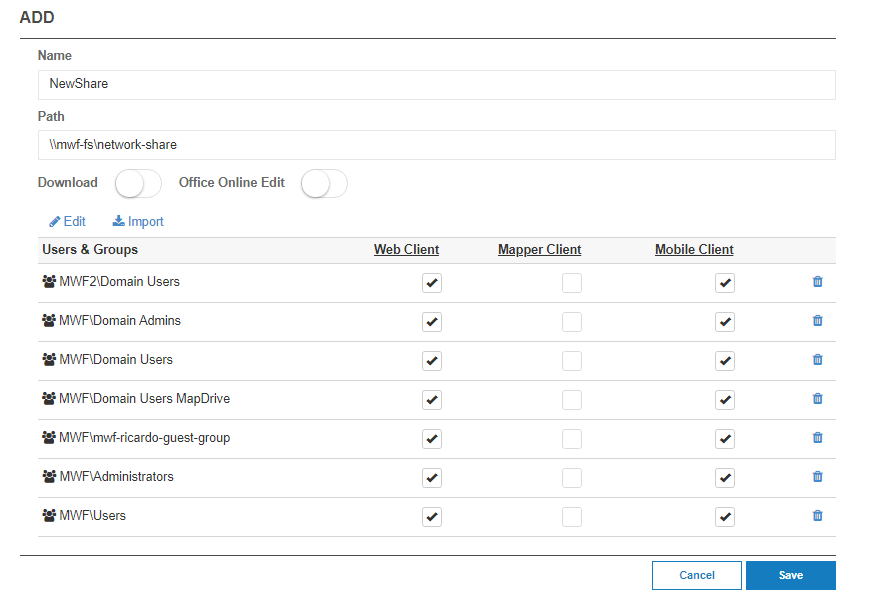
When creating a share, the NTFS permissions are now nested under the Edit and Import. You’re required to edit or import them and a warning message will prevent you from saving if you do not complete that step.
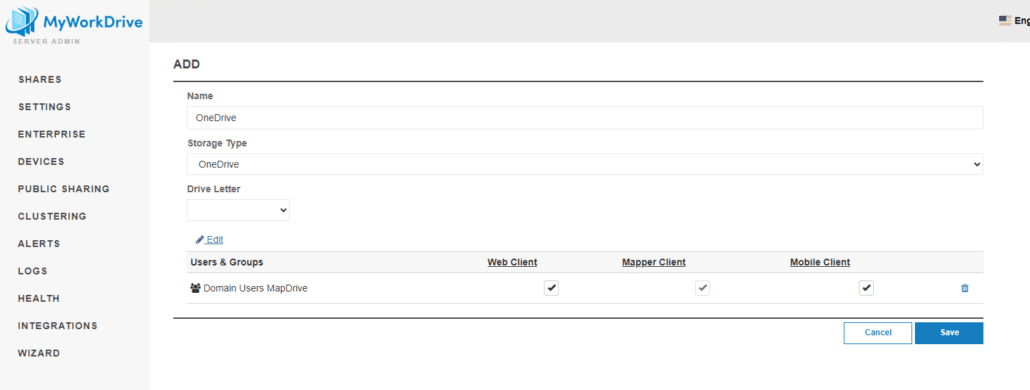
Once you complete that step, the share will load with default settings. In this case, note that the Mapper Client is not enabled nor available and Download is not displayed as an option. That’s because this server has DLP enabled, and Download is not enabled at the top of the share settings. To provide select users access to the Map Drive client – use the new Granular Permissions! Download must be enabled for a user/group to have Mapper Client privileges.
For ease of use, you can click the column header to select and deselect the entire row. Once Download is enabled, click Download in the header row above the check boxes to enable all of the users & groups listed.
Remember, MyWorkDrive cannot add permissions to NTFS which do not already exist, we only provide you the ability to add/edit users/groups to limit permissions down from what the user would have via SMB or VPN. If you require users/groups which do not exist in NTFS, add them to NTFS first!
If a user attempts to use a client they are not approved for, those shares will not be displayed – and if no shares are available, the user will receive the standard message that no shares have been provisioned.
Common Questions
Download and Office Online Edit do not display for me as options, how do I enable those
Download and Office Online Edit are part of our Data Leak Prevention features. Click here to read about enabling DLP on your server. Note that DLP requires an Enterprise license if you are not on an enterprise license Contact Sales about an upgrade.
I’ve enabled DLP, but only Download shows as an option. Office Online Edit is not available.
Verify that Office Online 365 edit is enabled in settings. You can read more about that here.
Guest User access does not appear as an option for me, how do I enable that?
Guest User Access is enabled in Enterprise settings and requires an integration with AzureAD. Read the complete setup guide and watch the video here for further details
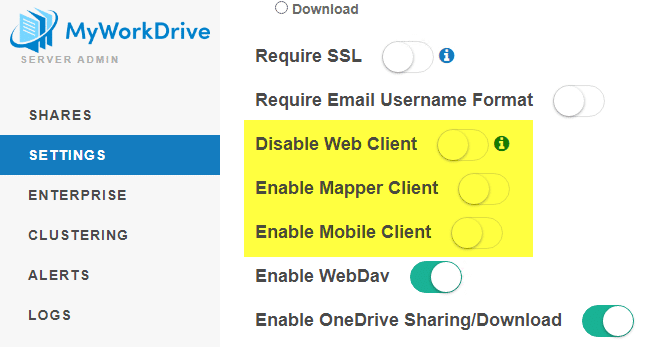
One of the Client options is not available on my Shares
All three clients – Web, Mapper and Mobile – can be disabled on the Settings page. When disabled, they will not appear as an option on Granular permissions. Double check settings and enable them for users to access.
MyWorkDrive version 6.4 introduced using SharePoint and OneDrive storage, in addition to SMB with NTFS Permissions.
Granular permissions operate slightly differently with OneDrive and SharePoint shares, in that there are no NTFS permissions and nothing to import.
When you edit the share and add Users/Groups from AD, you’re defining what users/groups should see the share in the MyWorkDrive client.
Granular Permissions with OneDrive and SharePoint allow you the same ability to control clients and features by user and group, the same as SMB shares. You can disable shares for different users/groups or in different clients.
When the user clicks to view the share in the client, they will be authenticated to OneDrive or SharePoint via their Entra ID credentials. Users may not see this prompt is they are already signed in to Azure (SSO)
Whether they are granted permission to see the content of the OneDrive account or SharePoint site sill depend on their permissions in Azure. Like SMB Shares, the user must have underlying permissions in Azure to view the shares.
With Entra ID Auth and Azure Storage
MyWorkDrive version 7 introduces Entra ID for identity, Local Shares via system account and SMB Shares Service Account, and Azure Storage options via Managed Identity, Entra ID Auth, Connection String and SAS token.
With Entra ID and Azure Storage, Granular Permissions no longer leverage the NTFS permissions on the file system, since there are no NTFS permissions with these share types and Entra ID Identity. Like OneDrive/SharePoint, the Granular Permissions on the shares in MyWorkDrive are used to define who can see and mount the root of the share. Whether the user will actually have permission to use the share depends on the underlying permissions on the share or in Azure.
The chart comparing storage options on the Storage Options article displays the permissioning system and underlying credentials for the different storage types.
Granular Permissions with Entra ID and Azure Storage allow you the same ability to control clients and features by user and group, the same as SMB shares. You can disable shares for different users/groups or in different clients.
“All Users” Groups
To ease configuration in cases where a share should be available to “everyone”; MyWorkDrive shows two groups we generate to ease deploying shares to “everyone”
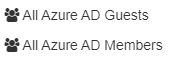
When assigning Users and Groups to a share, you will see at the top of the list “All Entra ID Guests’ and “All Entra ID Members”
When using these groups,
All Entra ID Members are all member users who have an active account in your Entra ID (not guest or other user types
All Entra ID Guests are all invited B2B guest users who have an active (non expired) account. Learn more about B2B guest users in this Microsoft article.
These simulated groups are intended to emulate the functionality found in other features in Azure/Teams/Office Online like “All Company”, which does not exist in Entra ID.
As with all Users/Groups permissions when using Entra ID and Azure Storage, the users must be assigned roles, permissions on the shares, or accessing via an account which has permission in order to actually gain access to files and folders. Simply assigning “All Entra ID Members” does not grant any underlying permissions to the storage.