How can we help you today?
Publishing MyWorkDrive with Nginx Proxy/Reverse proxy
Contents
Installation
Windows
A Windows installation of nginx has limitations that we were not comfortable supporting. Here is a list of those limitations:
Known issues
- Although several workers can be started, only one of them actually does any work.
- The UDP proxy functionality is not supported.
Possible future enhancements
- Running as a service.
- Using the I/O completion ports as a connection processing method.
- Using multiple worker threads inside a single worker process.
Linux
We’ll be installing nginx on Linux. Here is a link for the instructions to do a base install of nginx depending on your flavor of Linux: https://docs.nginx.com/nginx/admin-guide/installing-nginx/installing-nginx-open-source/
Configuration
Reverse Proxy
Instead of using our Cloud Web Connector for a reverse proxy, an Nginx server in your environment could be leveraged. Here is an example Nginx conf that could be used:
server
#Configures server to listen to 443/SSL on both ipv6 and ipv4
listen [::]:443 ssl ipv6only=on;
listen 443 ssl;
#Configures the location of the SSL certificate. This example uses an existing certificate instead of leveraging Let’s Encrypt.
ssl_certificate /etc/nginx/certificates/cert.cer;
ssl_certificate_key /etc/nginx/certificates/key.key;
root /var/www/html;
server_name _;
#Configures your nginx DNS address to point to your cluster name (configured at the top) and pass traffic to those along with the associated headers.
location / {
proxy_pass https://MWD-Server1.domain.tld:443;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection 'upgrade';
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
}
}
#The following block forwards all http traffic to https
server {
listen 80;
listen [::]:80;
server_name _;
return 301 https://$host$request_uri;
}
Load Balancer
If leveraging an Nginx for a reverse proxy, configuring MyWorkDrive to be in an active-active cluster with the following Nginx conf would allow you to load balance between the two:
#Configures the name of your cluster (in this example “cluster”), sets the method for identifying unique sessions (in this example hashing the remote ip to binary), sets the server addresses and ports in your cluster
upstream cluster {
hash $binary_remote_addr;
server MWD-Server1.domain.tld:443;
server MWD-Server2.domain.tld:443;
}
server {
#Configures server to listen to 443/SSL on ipv6 and ipv4
listen [::]:443 ssl ipv6only=on;
listen 443 ssl;
#Configures the location of the SSL certificate. This example uses an existing certificate instead of leveraging Let’s Encrypt.
ssl_certificate /etc/nginx/certificates/cert.cer;
ssl_certificate_key /etc/nginx/certificates/key.key;
root /var/www/html;
server_name _;
#Configures your nginx DNS address to point to your cluster name (configured at the top) and pass traffic to those along with the associated headers.
location / {
proxy_pass https://cluster;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection 'upgrade';
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
}
}
#The following block forwards all http traffic to https
server {
listen 80;
listen [::]:80;
return 301 https://$host$request_uri;
}
SSL
Public Cert
Nginx has instructions on how to install your own certificate. The instructions are available here: https://nginx.org/en/docs/http/configuring_https_servers.html
Let’s Encrypt Cert
Nginx has instructions on how to install the Let’s Encrypt Client to get a free SAN cert for your domain. The instructions are available here: https://www.nginx.com/blog/using-free-ssltls-certificates-from-lets-encrypt-with-nginx/
MyWorkDrive Self-Signed Cert
Using a Let’s Encrypt Cert or your own public cert for your reverse proxy allows the MyWorkDrive Administrator to use a self-signed certificate and leverage end-to-end encryption between nginx and MyWorkDrive. To enable a self-signed certificate in MyWorkDrive:
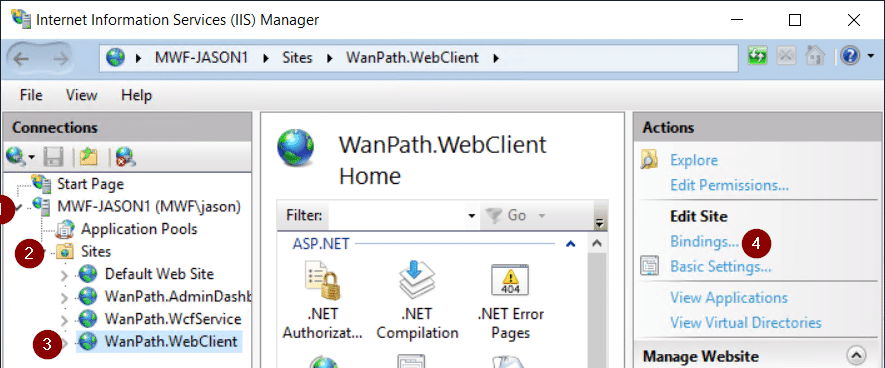
- Open IIS and expand your server’s sites
- Expand Sites
- Select WanPath.WebClient
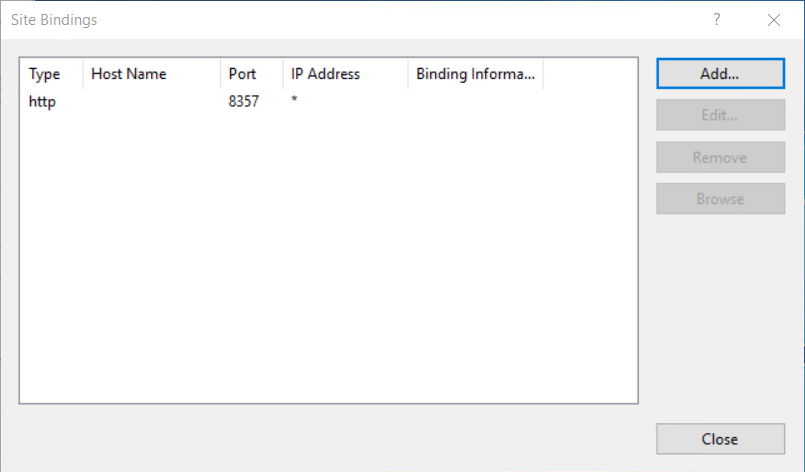
- Click Bindings in the right panel
5. Under the bindings page click Add…
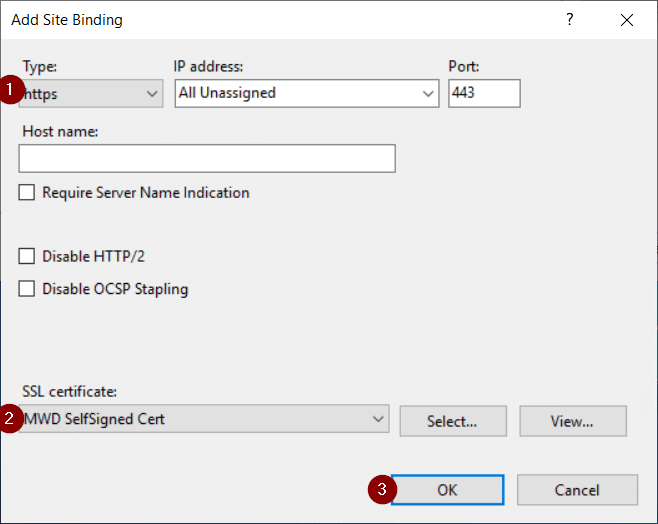
6. In the Add Site Binding page, change Type to https. Leave IP address and Port as default.
7. Under SSL certificate, select MWD SelfSigned Cert
8. Select OK.
9. Edit your Nginx conf to point to your MyWorkDrive server and manually specify port 443.
For reference, see
https://docs.nginx.com/nginx/admin-guide/web-server/reverse-proxy/