How can we help you today?
External B2B File Sharing of Windows file shares with MyWorkDrive and Azure Active Directory Guest Accounts
MyWorkDrive External B2B File Folder Sharing Overview
Contents
- Setup MyWorkDrive server to use Azure AD SAML with Delegation or Kerberos Constrained Delegation to the file shares
- Create a group in Azure AD for guest users that will be used to track or permit access to the MyWorkDrive SAML app
- Create an OU in Active Directory to Store external users
- Create Active Directory Guest Users Group
- Create Azure AD Enterprise App Registration
- Enable Guest User Sharing
- Enable and invite guest users to a share
- Complete Setup
- Manage Guest Users
- Permitting users to invite guests to shares
Enterprise+ Licensed Customers who utilize MyWorkDrive Azure AD integration for authentication can now easily invite external guest users to collaborate on Windows File Shares.
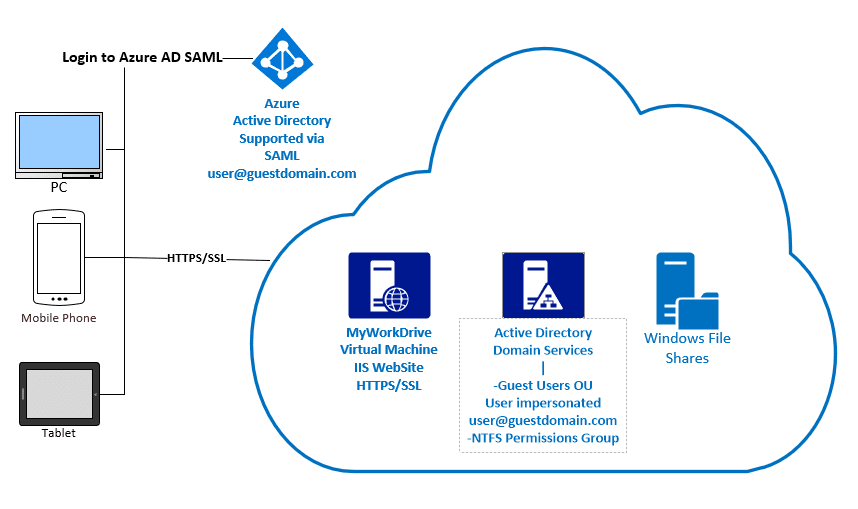
With this feature, external users are invited to Azure AD as Guest Users. They’re emailed an invitation to join. Once redeemed and logged in, they are then impersonated by MyWorkDrive to show them their allowed folders. By inviting external users to Azure AD, the administrator will not need to manage guest user logins, passwords or authentication while still allowing the guest user to fully collaborate with internal users on files and folders within the MyWorkDrive File Share.
More details on how this works are detailed in this Microsoft Support Article: https://docs.microsoft.com/en-us/azure/active-directory/b2b/hybrid-cloud-to-on-premises and in our B2B File Sharing Video.
To implement Guest user sharing in MyWorkDrive, a user account is created for the invited guest in Active Directory which we can impersonate, and set such that the invited guest user can’t login interactively – only via AzureAD. Once logged in to Azure AD, the user is impersonating that user to show them their Windows File Shares.
Unlike external link sharing using OneDrive or Sync & Share systems, the guest user can fully collaborate on files and folders with internal users. From a security and support standpoint there are no password resets to manage and security can be enabled on Azure AD Guest Accounts to require Multi-Factor Authentication to verify user identities.
Conversely, to enable Windows file shares to provide anonymous access external via links would require compromising security by storing password hashes in a database or granting the server computer account full write access to all Windows file shares. We have seen competing products that store password hashes to shares in a database that have rights to all shares at the root level.
We chose to avoid such an extreme security risk; avoiding integrations which require storing password hashes or permitting unrestricted access to file shares. Our choosen method also avoids issues like shared folders being renamed and breaking share links or storing files in databases which defeats the purpose of accessing files on Windows File Shares without migrating them.
Prerequisites
- Setup MyWorkDrive server to use Azure AD SAML
- MyWorkDrive Server 6.0 or higher with Enterprise Plus license
- Create an OU in Active Directory to Store external users
- Create an Active Directory Group for Guest Users & grant it NTFS permission on the file share(s)
- Add the Active Directory Group to the share in MyWorkDrive
- Enterprise Plus MyWorkDrive Subscription License
Detailed Guest User Folder Sharing Setup Steps
It is necessary to integrate MyWorkDrive with Azure AD using our SAML integration. The Azure Directory will be used to authenticate and store guest users. It does not need to be the same Azure Active Directory used by the company, nor does the company need to use Azure AD for internal user MyWorkDrive authentication. Follow our support article here to setup Azure AD SAML authentication in MyWorkDrive.
Create a group in Azure AD for guest users that will be used to track or permit access to the MyWorkDrive SAML app
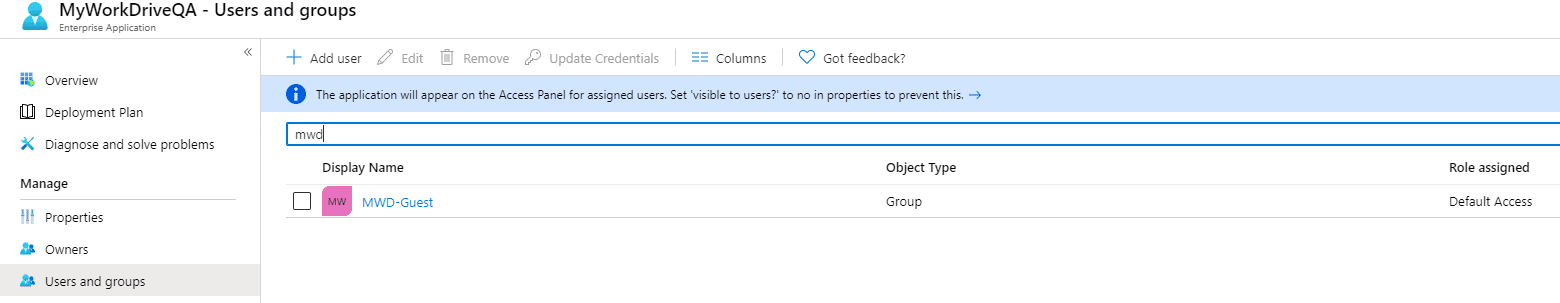
In azure AD create a cloud based group for external guest users who will be allowed to use the MyWorkDrive Enterprise SAML app and add this group to allow those users to login.
Group created in Azure AD – for example “MWD-Guest”: 
If you require users to be assigned to the app to login (The SAML App properties “User Assignment Required” is set to Yes), Add the AAD Group to your MyWorkDrive SAML App to permit login by Guest Users:
Create an OU in Active Directory to Store external users
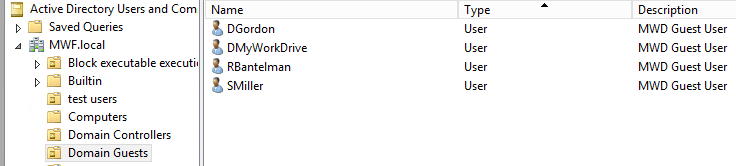
In Active Directory, create an OU to store all external guest users. This will make it much easier to manage, remove or edit external guest users later. The guest users will be created and stored here. They will be set to SmartCardLogonRequired to prevent login using username/password since we will impersonate them instead using delegation. These users will also be removed from domain users to prevent access to any internal resources. If your company is syncing your Active Directory to Azure AD using AD Sync, be sure to exclude this OU from automatic syncing.
Create Active Directory Guest Users Group
In Active Directory, create a guest user group. External guest users will be added to this group as their primary Active Directory group and removed from the default domain users group. This Active Directory Group can also be used to grant NTFS permissions to the shares you wish to make available to eternal users in MyWorkDrive.
Create Azure AD Enterprise App Registration
To allow the MWD Server to automatically create and manage guest users in Azure AD it is necessary to create an Azure AD Enterprise App. The AAD App can be created manually or using our PowerShell script.
Automatic Powershell Registration
Download and run our PowerShell Azure AD App Creation Script as administrator from the MWD Server. The script will prompt you for Azure AD Domain name, Application Name and prompt for login to Azure AD several times to authorize your AAD App.
The script will automatically create your enterprise app registration and save the resulting Application id and Tenant id into the MWD admin panel under Enterprise settings.
To complete the connection to AzureAD, copy and paste the Application Secret manual into the MWD Admin panel under Enterprise settings, Guest User settings.
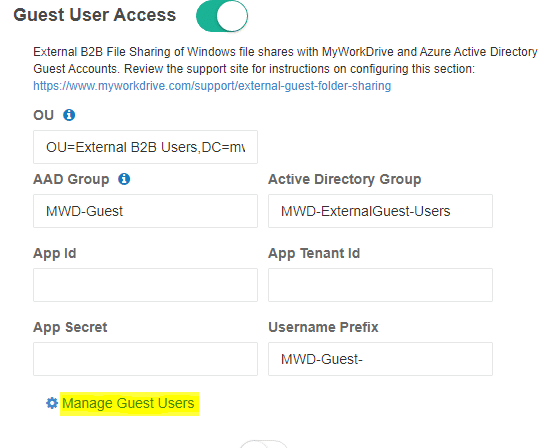
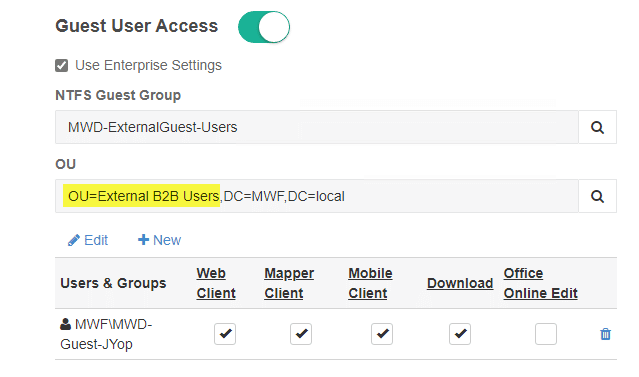
Complete the setup by enabling guest user sharing under Enterprise settings – Azure AD SAML: Guest Users: Input your guest users OU, Azure AD created user group and Active Directory Group. Click Save.
Manual Registration:
Register MWD admin panel application in your Azure account.
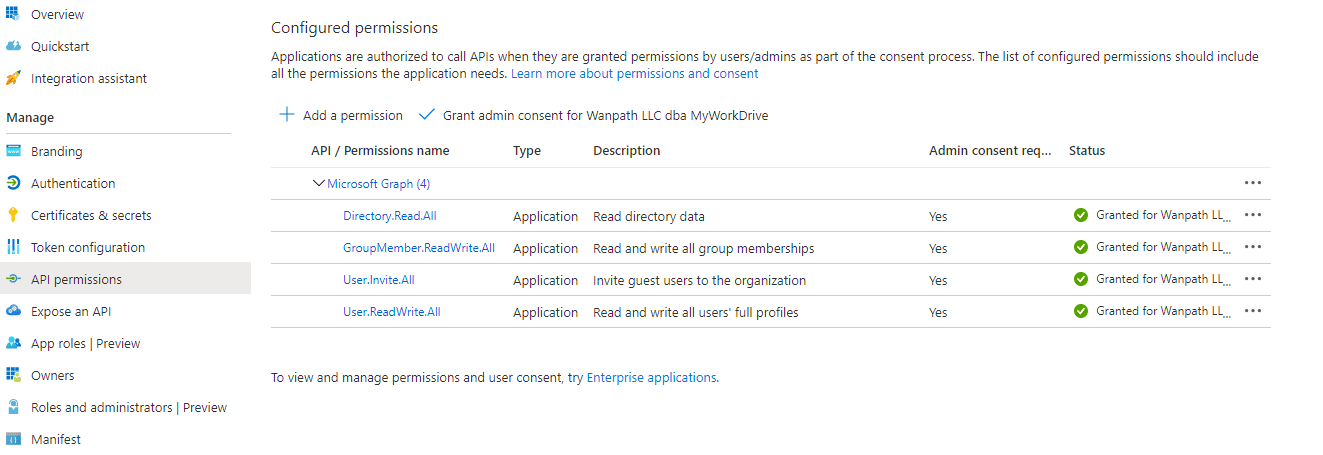
MWD admin panel needs the following permissions:
Directory.Read.All
User.Invite.All
User.ReadWrite.All.
GroupMember.ReadWrite.All
Save the resulting application/client id, directory/tenant id and client secret for pasting into the MyWorkDrive Guest User setup under enterprise settings.
Create the Application Secret and paste it into the MyWorkDrive.
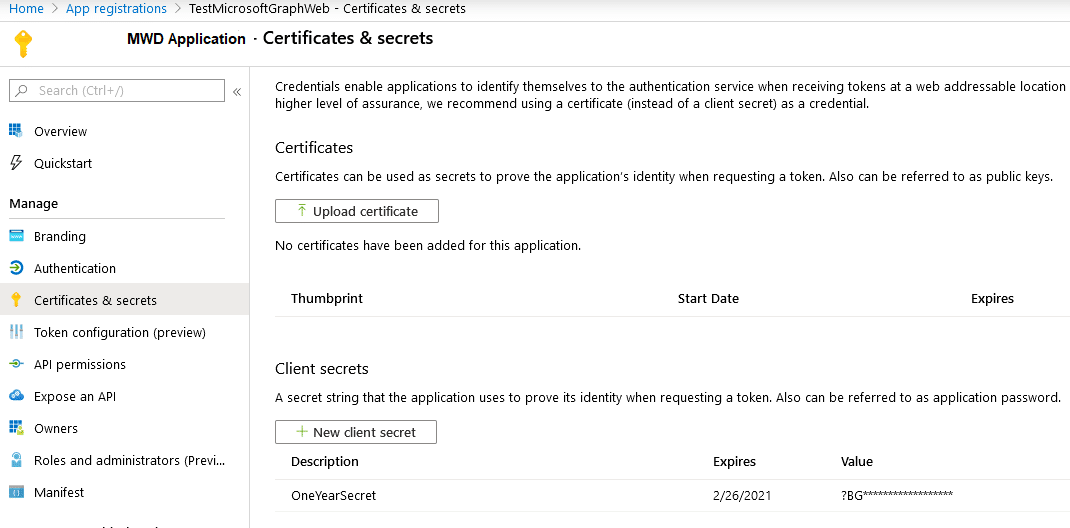
Enable Guest User Sharing
Complete the setup by enabling guest user sharing under Enterprise settings – Azure AD SAML – Guest Users: Input your guest users OU, Azure AD created user group and Active Directory Group.
If you used our automated Powershell script the App ID, App Tenant Id and App Secret will already be pre-filled. If not, manually paste in these settings.
Accept or modify the Username Prefix as desired to add a prefix to all guest user usernames to assist in differentiating or finding guest users in Active Directory as desired.
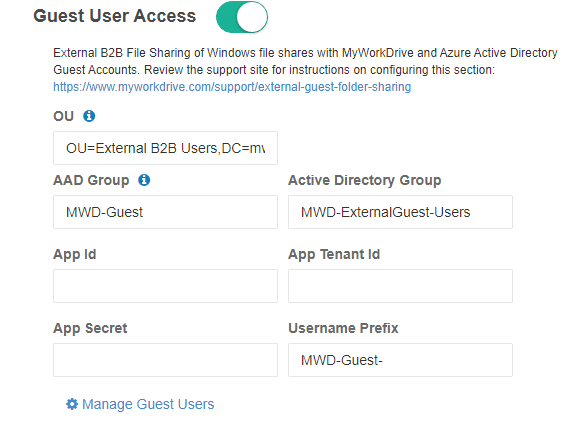
Before enabling Guest sharing access on a MyWorkDrive share, either create a new unique Active Directory Group that will be used for assigning NTFS permission on each file share or use an existing Group (this can be the same group that was used in used as the default domain group applied to guest users when enabling guest user access in enterprise settings).
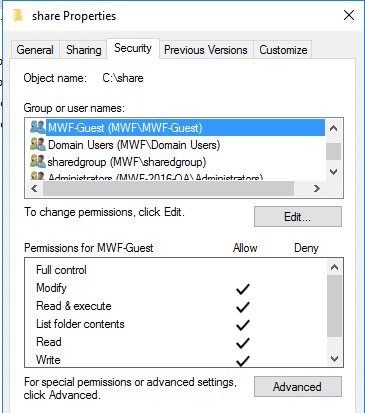
Click the slider and enable Guest User Access. Search for and select the desired NTFS permission group that guest users will be added to to.
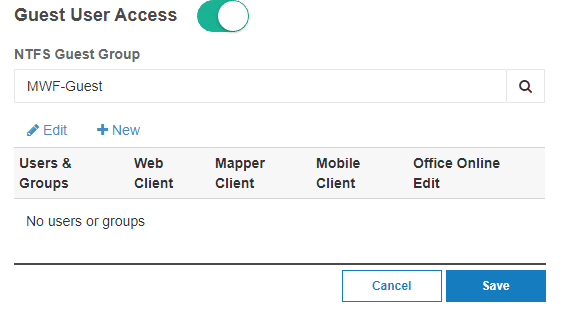
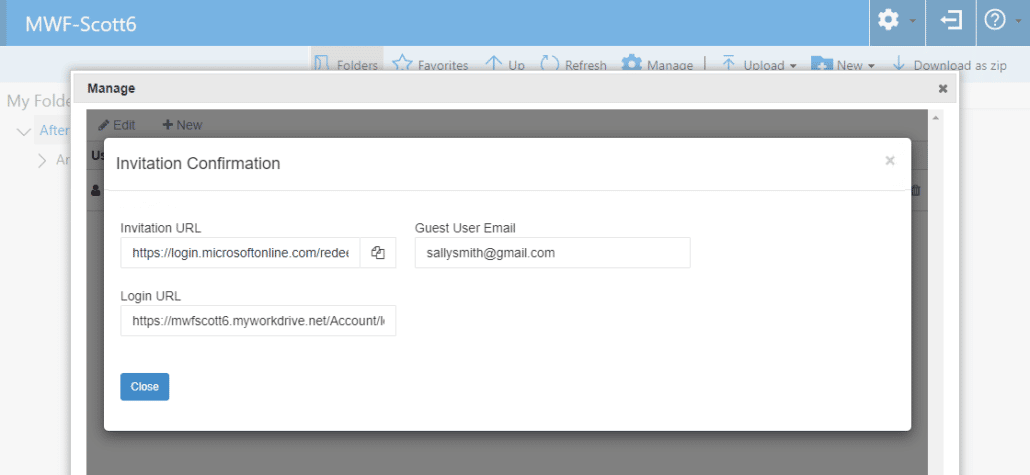
Click “New” to Invite the external guest user
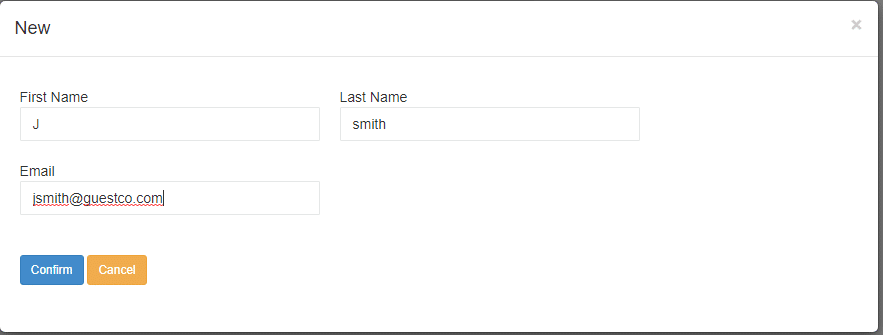
Click to confirm the invitation.
When the shares page reloads showing the guest has been invited, save the shares page.
It is critical you save the shares page after making user changes (such as inviting a guest or changing granular permissions.)
Scroll to the top or bottom of the shares page and click the save button before proceeding.
Complete Setup
After inviting the guest user, the External Guest User is created internally and externally in Azure AD and sent an email invitation.
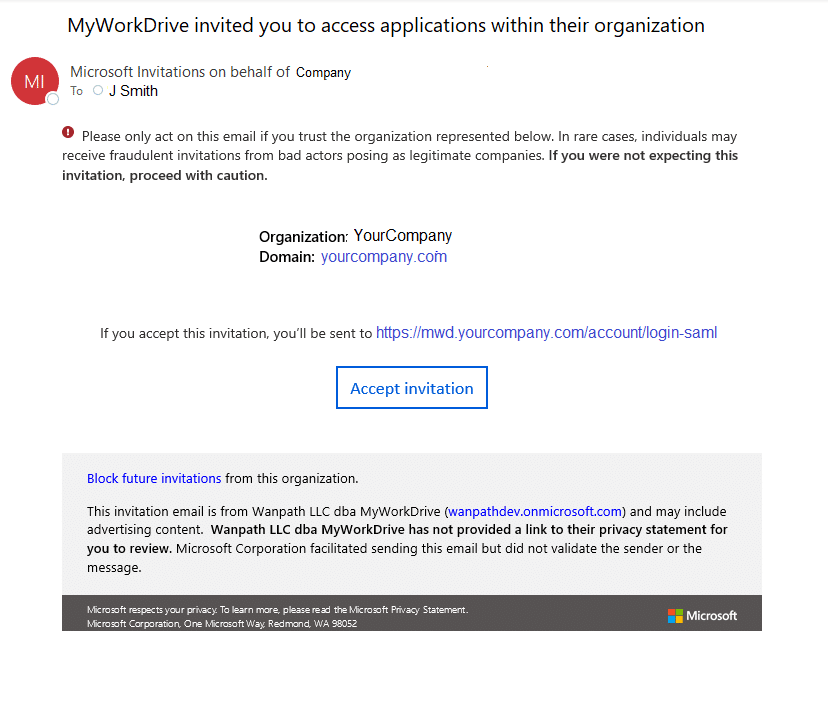
When they click Accept Invitation they will be prompted to Login to or Create a Microsoft Account, along with any MFA or validation you required. Once authenticated, they will be logged in to MyWorkDrive and see the shares they are provisioned for at your MyWorkDrive server web address.
Note, due to propogation, it may take as long as 15 minutes after creation for the new user to be sync’d across all segements of AD and a successful login to be completed.
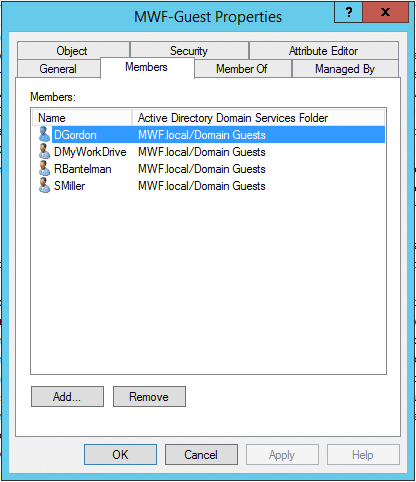
Manage Guest Users
Guest users can be easily disabled or removed in Active Directory and Azure AD at any time. Invited users can be re-sent email invitations or removed in Azure AD. External Guest Users may also be accessed on the enterprise page:
Once clicked, select the user to resend email invitations or remove them from Active Directory and Azure AD as guest users. Delete will remove them from AzureAD as well as LocalAD.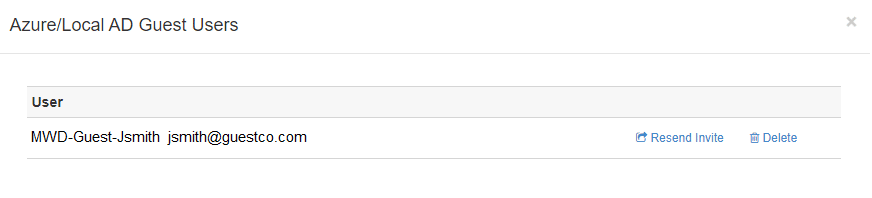
New! As of MyWorkDrive server 6.3, you are able to assign users who have access to MyWorkDrive shares the ability to invite guest users to the share using the “Manager” option.
With this new feature, designated users can invite guests to configured shares via the MyWorkDrive Web Client with their regular user login, no admin access to the MyWorkDrive server is required.
Prerequisites
- Guest User Access being enabled (described above)
- The share having guest user access configured (described above)
- You will also need to grant the users who have permission to invite users delegated OU permissions in active directory (described below)
Note that the Prerequisites are required to be completed by an administrator in MyWorkDrive administration.
Enabling Managers
Step 1, Enable on Shares
This step is completed in MyWorkDrive Admin.
When Guest User Access is correctly configured, and the share is enabled for guest user sharing, an additional column is enabled in the granular permissions section of file share management titled “Manager”. You will want to manually add individuals you are granting the Manager permission to to the share list using the edit feature.
- Add the user in question from Active Directory to the share.
This may be redundant with an existing group configured on the share, but is appropriate as you are granting manager permissions to a specific user. - Enable appropriate permissions for the user for Client Access and DLP
Some columns may not appear depending on enabled clients, drive letter configuration, whether Office Online is enabled, and whether you have DLP enabled or not - Enable the Manage feature for the user.
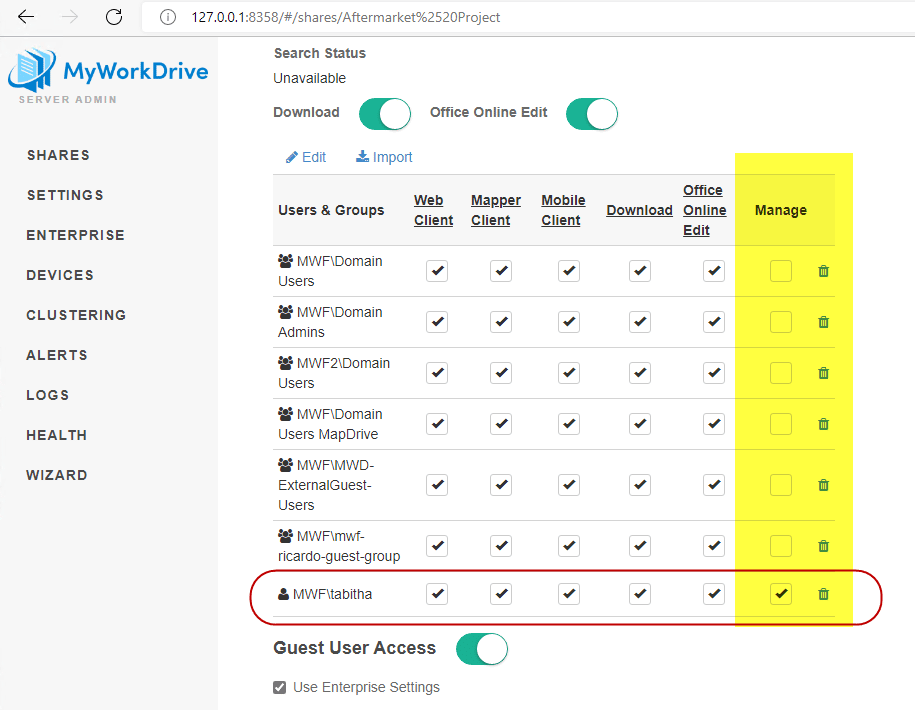
Step 2, Enable in Active Directory
The Manager user(s) must be granted permission to create users in Active Directory. This should be exclusively granted to the OU where the guest accounts are created, and the least priviliged access should be granted.
In Active Directory Users and Computers, find the OU where your guest users are being stored. (this can be found in the Guest User Access configuration on the share)
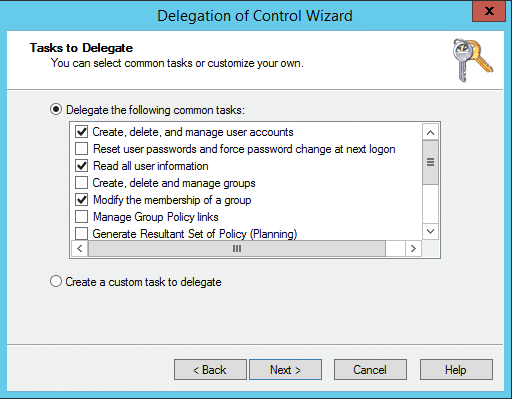
Right click on the OU in ADUC and select Delegate Control.
Add the appropriate user(s) who should be permitted to invite users.
When selecting permissions, select only
- Create, delete, and manage user accounts
- Read all user information
- Modify the membership of a group
No other permissions are required nor recommended.
Note that changes to Active Directory require time to propagate across all servers in the domain, so users may not be able to immediately use the feature. Most AD Sync processes complete within 15 minutes, though on larger or more distributed domains the process may take up to 1 hour.
Managing Guest Users from the MyWorkDrive Web client.
When users with the Manager role enabled sign in to the MyWorkDrive Web client, those shares that are so configured will have an additional button in the menu titled “Manage”
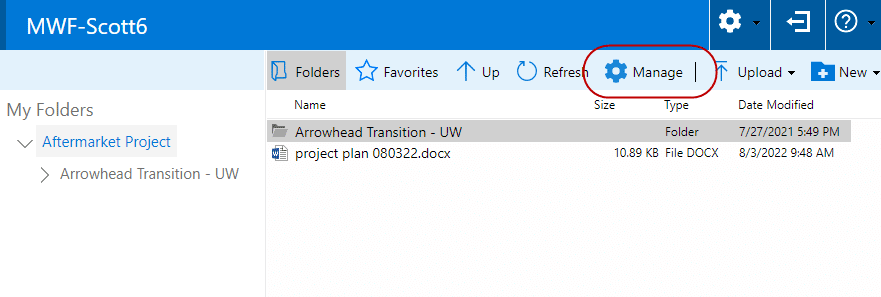
Note that the Manage feature for users is only available in the MyWorkDrive Web client.
Clicking on Manage will launch a new window, where the user may be prompted for a secondary login for security purposes.
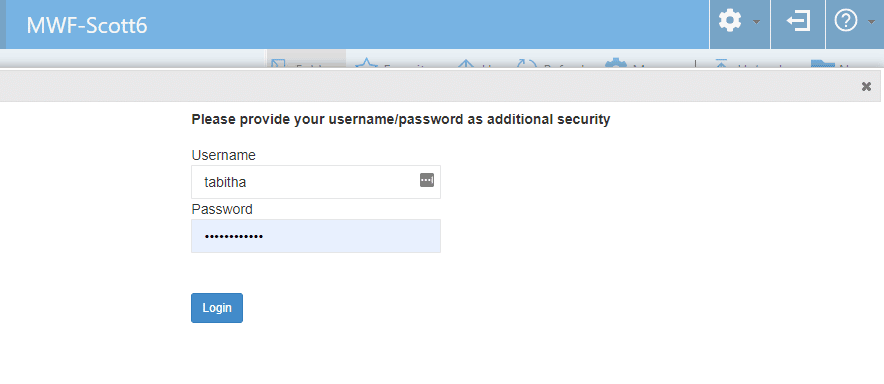
After completing any secondary login (when necessary), a similar interface to managing Guest Users as is shown in Admin is presented to the user.
Existing guests who have been invited to the share will be shown that can be changed/deleted, and links to add an existing guest to a new share or invite a new guest are included.
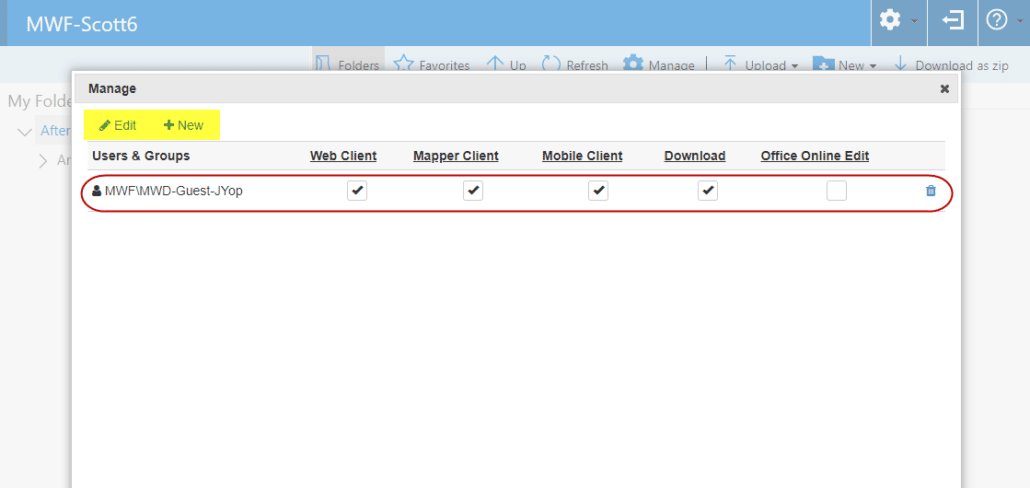
Using the Edit button will show a list of existing guests on the domain who were previously invited to shares on the MyWorkDrive server and can be additionally granted access to this share.
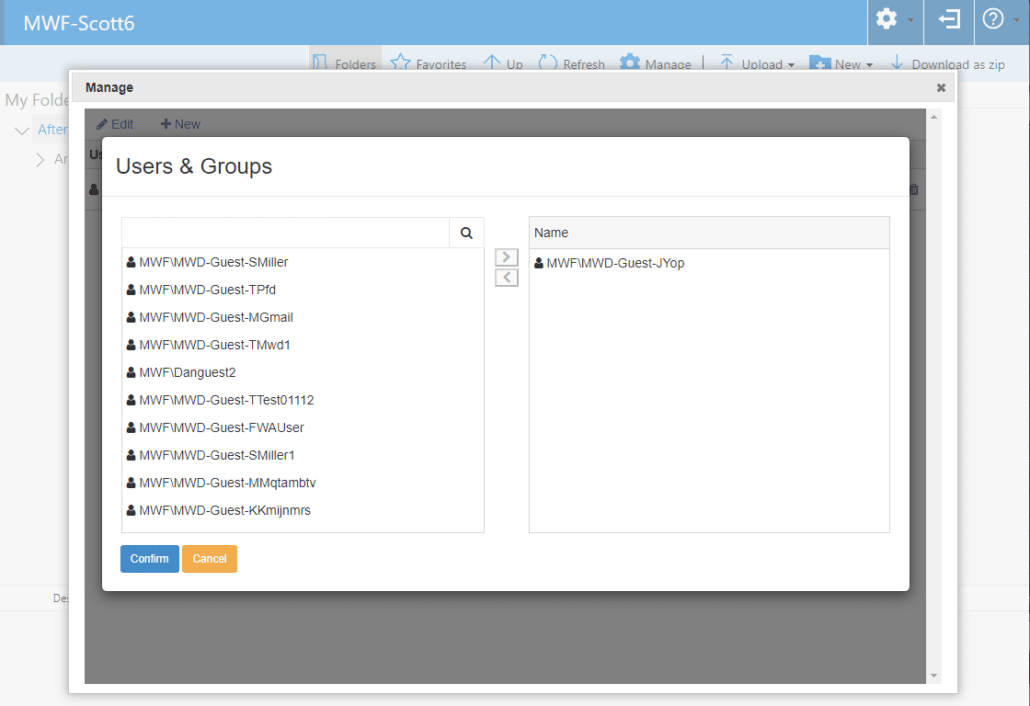
Using the Add button will permit the Manager to add a user’s name and email to invite them to the share. This follows the same process as inviting a user from the Admin panel and will add the user to Azure AD and Local AD, assign them to the appropriate group, and send them an email with links to accept the invitation and to access the share.
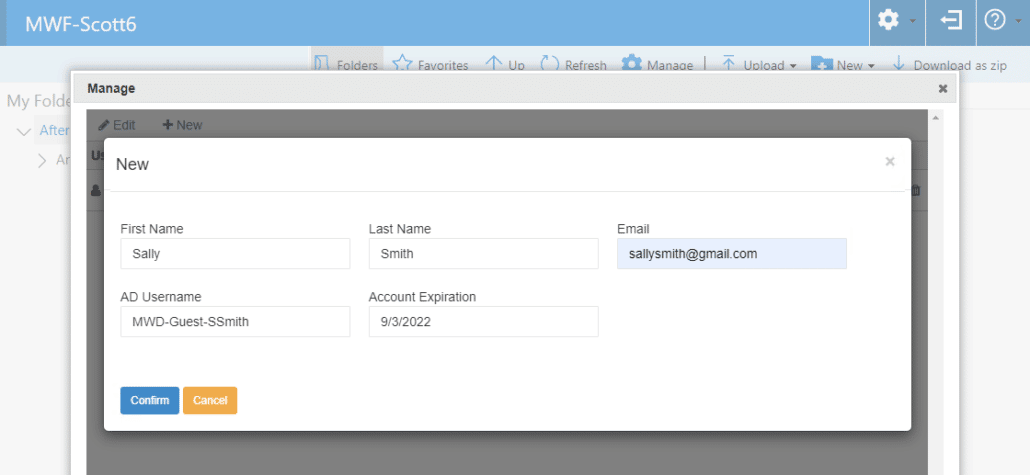
Like inviting through Admin, a confirmation page is shown after the user is added with a link to the Invitation URL and Login URL, in case the manager wishes to manually inform the invited guest user of their access information.