How can we help you today?
Azure Load Balancer Setup with MyWorkDrive Virtual Machines
How to setup Azure Load Balancer with MyWorkDrive Virtual Machines
Overview
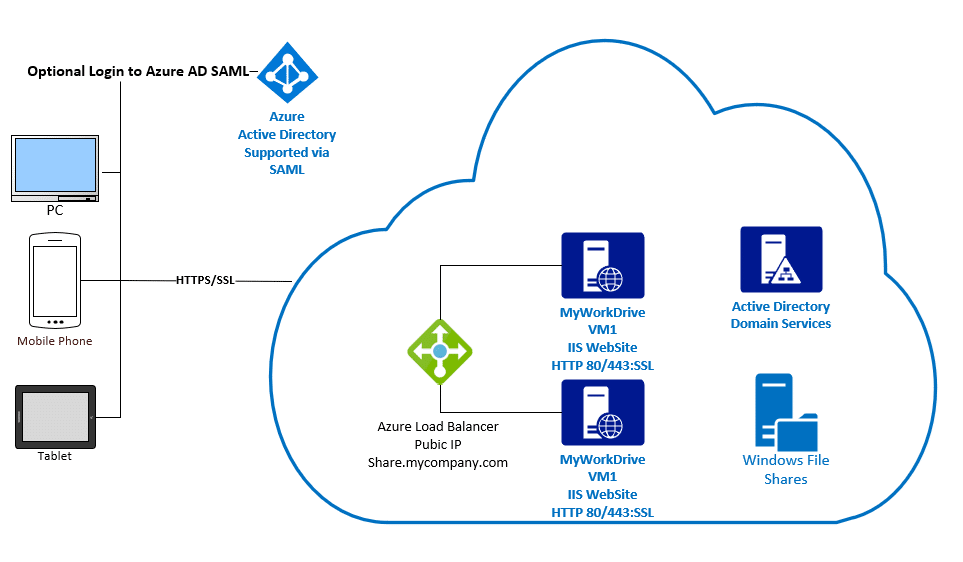
Azure Load Balancers work very well with MyWorkDrive Virtual Machines hosted in Azure. With Azure Load Balancers, Client Source IP is used as part of the session affinity to ensure users are returned to the same MyWorkDrive Server after login. This article assumes you have already setup your MyWorkDrive servers for clustering using our support article here. 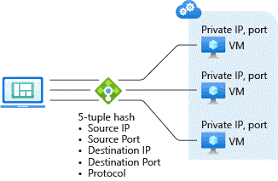
Prerequisites:
Load Balancer and Virtual Machines are located in the same Azure Resource Group and Virtual Network Load Balancer SKU is set to Standard Virtual Machines Public IP set to Standard SKU (Static), located in same availability set.
Virtual Machine Setup Steps:
Begin by creating an Azure Virtual Network with DNS and Subnet IP’s that will resolve and host Active Directory DC’s, Host Azure Virtual Machines and Load Balancer Components. Setup virtual machines using our MyWorkDrive Azure Image in the Azure Store with a public IP using the standard SKU that is part of your already created Subnet in the same availability set. When setting up the virtual machines, join an existing Active Directory. Complete setup as normal and verify availability of the Web Client site using http://127.0.0.1:8357 by logging onto the Virtual Machine via RDP. Ensure that port 80 is bound to the Wanpath.WebClient site and is accessible to the load balancer as well.
Load Balancer Setup Steps:
Create Load Balancer:
Create Load Balancer with Standard SKU in the same resource group as your existing VM’s. For Availability zone select Zone-redundant to create a resilient load balancer. 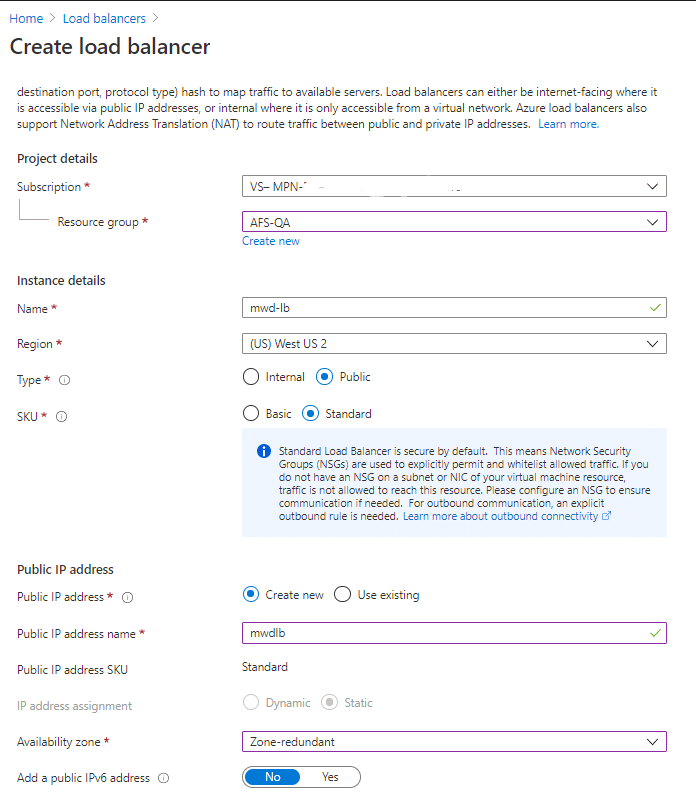
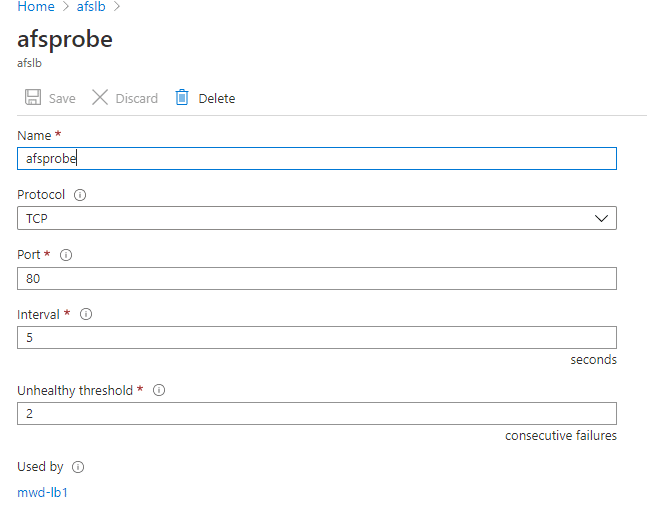
Add Health Probe:
Add a health probe using port 80 that will confirm availability of both VM’s for the load balancer:
This Microsoft Article includes details on Health Probe configuration
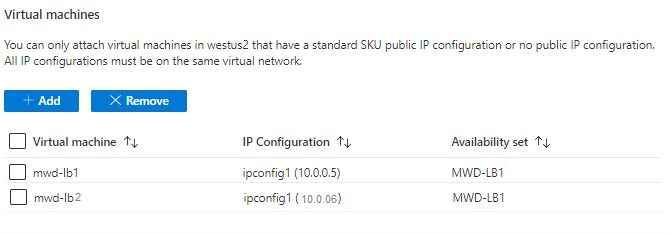
Add Backend Pool:
Add a Backend Pool, adding the VM’s as part of the pool.
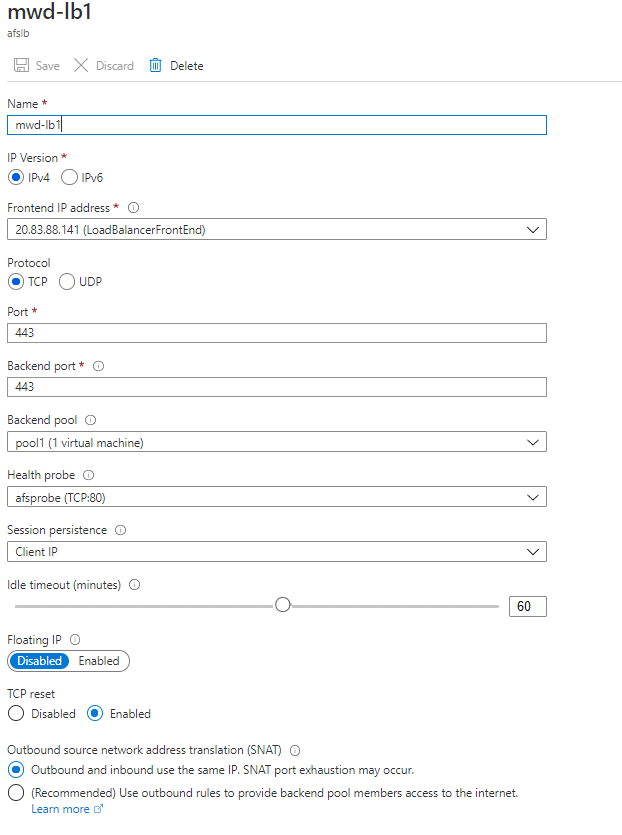
Add Load Balancing Rule:
Add Load Balancing Rule – note that session persistence is set to Client IP and port 443 are used (this assumes you have already setup matching SSL certificate bindings on each MyWorkDrive Server).
Testing:
Test access to server e.g. https://hostname.domain-name.com to ensure forwarding is connecting to each backend server. Temporarily disable access to each server via port 80 to test failover. Adjust failover health probe settings as desired.
Optional:
Enable Azure AD SAML Single Sign-On. Note that Azure AD SAML expects the host name to match the original request in the reply URL. For example: Share.mydomain.com should be set to use the load balance front end public IP. For testing as needed additional reply URL’s may be added to the Azure AD SAML as allowed Reply URL’s during initial setup and testing. Additionally we recommend testing is completed using only the hostname over https prior to enabling Azure AD SAML to simplify testing.