How can we help you today?
Azure File Storage Options
Overview
MyWorkDrive Server 7 or higher supports connecting to Azure File Shares and Azure Blob storage over Rest API with Azure AD (Entra ID) authentication. Azure Storage is typically deployed alongside a MyWorkDrive virtual machine deployed in Azure.
With Azure Storage, Only the storage space used is charged for standard file shares, rather than the allocated limit. Pricing for premium files shares is based on provisioned GiB and includes all transaction costs. You can configure your Azure storage based on your storage size, IOPS, and throughput requirements.
Contents
- Overview
- Comparison Grid
- Azure File Shares /Rest API – Entra ID/Managed Identity (Recommended)
- Azure File Shares /Rest API – Entra ID
- Azure File Shares /Rest API – Connection String
- Azure Blob Storage /Rest API – Entra ID w/Datalake
- Azure Blob Storage /Rest API – Connection String
- Azure File Shares /SMB
Comparison Grid
A comparison grid of the supported Azure Storage options is located below. For maximum security, functionality and performance, we recommend deploying an Azure Virtual Machine with managed identity granted permissions to Azure File Shares for fileshare level permissions or Azure Blob Storage with DataLake V2/Hierarchical name space enabled for NTFS style ACL file and folder level permissions integrated with Entra ID.
Azure file shares storage accessed under the context of the MyWorkDrive Server Virtual Machine Managed Identity in Azure provides the greatest level of security (no authentication information is stored in the MyWorkDrive Server configuration when managed identity is used) and enables full functionality including external file sharing. This option requires the MyWorkDrive Server be located in Azure with system managed identity enabled. In addition, the managed identity of the Azure virtual machine must be granted “Storage File Data Privileged Contributor” Rights.
Begin by creating an Azure Storage Account and Azure File Share in Azure, then grant the MyWorkDrive Azure Based Virtual Machine “Storage File Data Privileged Contributor” Rights.
Once these prerequisites are set, simply add the azure storage account and file share to the MyWorkDrive Server admin panel under Integrations – Azure File Shares:
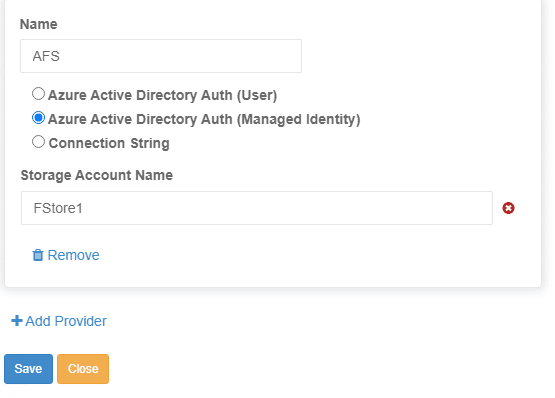
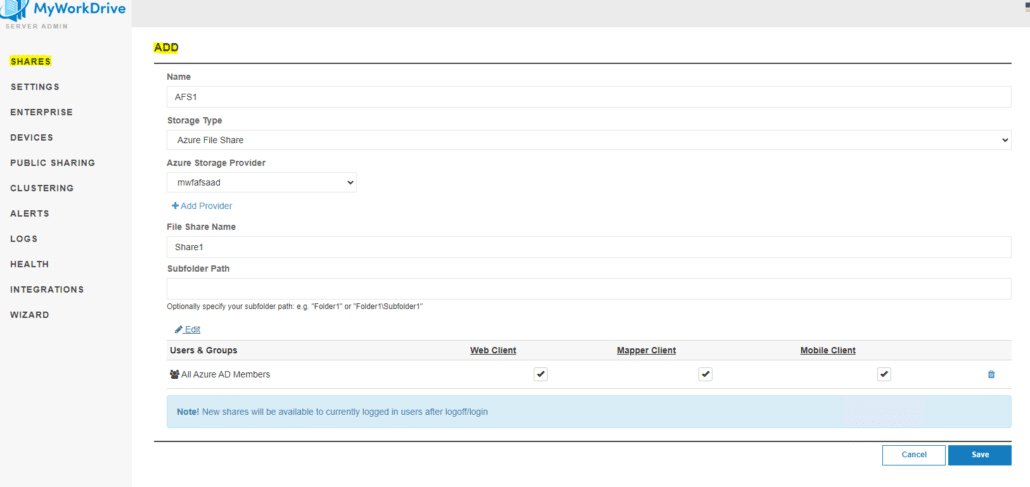
Finally, once the Azure Storage is added to integrations, add a share using that storage and grant Entra ID users permissions to access it (if you prefer to grant all Entra ID users or All Azure AD/Entra Guests permissions to the share, you may use our default groups “All Azure AD Guests” or “All Azure AD Members” instead of assigning individual users or custom groups).
Azure file shares storage accessed under the context of the user’s Entra ID Azure provides an easy way to access Azure File Shares without requiring that the MyWorkDrive Server be located in Azure as a virtual machine. With this option, External File Sharing is not available since the MyWorkDrive server does not store any user credentials or have managed identity access. With this option the Entra ID users/Groups must be granted “Storage File Data Privileged Contributor” Rights to be able to have Modify (add, change, delete) rights on the share.
Begin by creating an Azure Storage Account and Azure File Share in Azure, then grant Entra ID users and groups “Storage File Data Privileged Contributor” Rights at the Azure File Share.
Once these prerequisites are set, simply add the azure storage account and file share to the MyWorkDrive Server admin panel under Integrations – Azure File Shares:

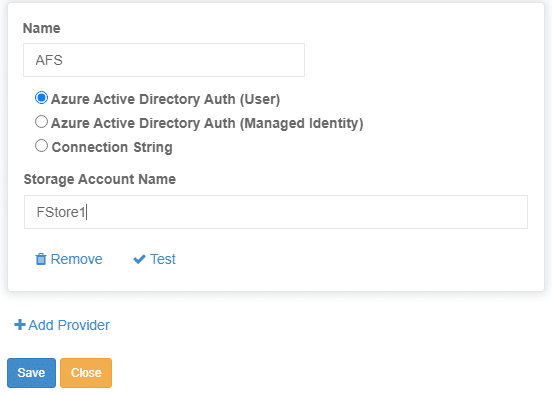
Finally, once the Azure Storage is added to integrations, add a share using that storage and grant Entra ID users permissions to access it (if you prefer to grant all Entra ID users or All Azure AD/Entra Guests permissions to the share, you may use our default groups “All Azure AD Guests” or “All Azure AD Members” instead of assigning individual users or custom groups.

Azure file shares storage accessed using the storage connection string provides a simpler way to add connectivity to a MyWorkDrive server to Azure File Shares over Rest API. When using the Azure Storage Connection String, the MyWorkDrive server is not required to be located in Azure (however performance will be impacted based on the network connectivity between Azure and the MyWorkDrive server). Additionally, an encrypted copy of the Azure Storage Account connection string is stored on the MyWorkDrive server unlike the managed identity option where nothing is stored on the MyWorkDrive server.
Begin by creating an Azure Storage Account and Azure File Share in Azure.
Once the Azure File Share and Storage account is created, simply add the azure storage account and file share to the MyWorkDrive Server admin panel under Integrations – Azure File Shares:

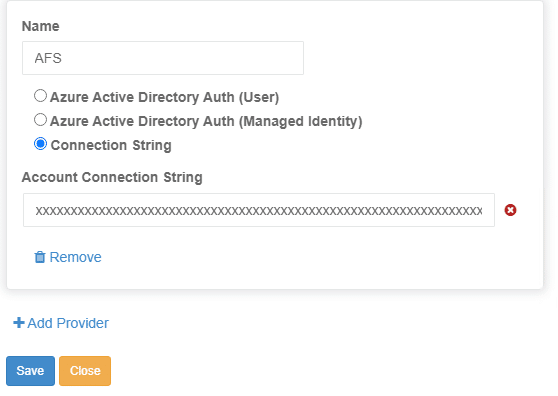
Finally, once the Azure Storage is added to integrations, add a share using that storage and grant Entra ID users or groups permissions to access it (if you prefer to grant all Entra ID users or All Azure AD/Entra Guests permissions to the share, you may use our default groups “All Azure AD Guests” or “All Azure AD Members” instead of assigning individual users or custom groups).

Azure Blob Storage /Rest API – Entra ID w/Datalake
Azure blob storage /Rest API with Datalake has the added advantage of supporting file and folder level permissions in addition to the Entra ID users/groups configured on the MyWorkDrive Server. Permissions must be set using Azure Storage Explorer and hierarchical namespace must be enabled. In addition, the managed identity of the Azure virtual machine must be granted “Storage Blob Data Contributor” rights to properly access files and folders if public file sharing is desired.
Files and folders on Azure Blob Storage are displayed based on the Entra ID user/group configured on the MyWorkDrive Server Share and are accessed under the context of the Entra ID User. This option provides an additional layer of security since it requires the Entra ID User have permission on the blob storage in addition to being granted access on the MyWorkDrive server.
Begin by creating an Azure Storage Account and Azure Blob Storage with Datalake, Gen2 and hierarchical namespace enabled, then grant the MyWorkDrive Azure Based Virtual Machine “Storage Blob Data Contributor” rights to properly access files and folders if public file sharing is desired. Finally, grant individual Entra ID Users/Groups permissions to Azure Blob storage using Azure Storage Explorer.
Once these prerequisites are set, simply add the azure storage account and blob to the MyWorkDrive Server admin panel under Integrations – Azure Blob Storage:
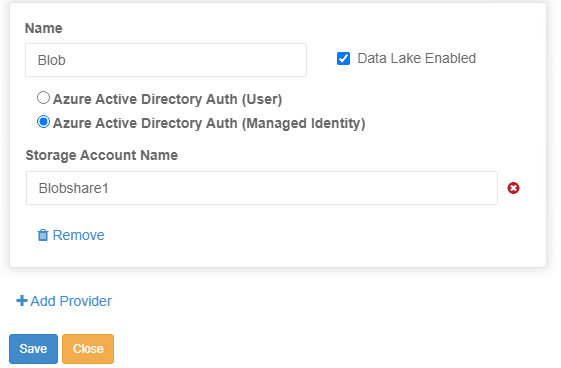
Finally, once the Azure Storage is added to integrations, add a share using that storage and grant Entra ID users permissions to access it (if you prefer to grant all Entra ID users or All Azure AD/Entra Guests permissions to the share, you may use our default groups “All Azure AD Guests” or “All Azure AD Members” instead of assigning individual users or custom groups.
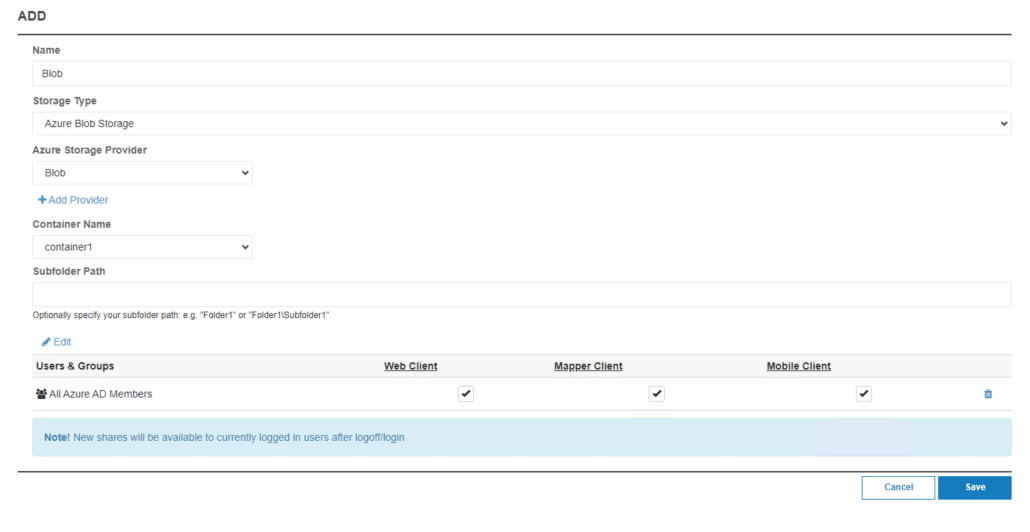
Azure Blob Storage /Rest API – Connection String
Azure blob storage accessed using the storage connection string provides a simpler way to add connectivity to a MyWorkDrive server to Azure Blob Storage over Rest API at the storage account level. When using the Azure Storage Connection String, the MyWorkDrive server is not required to be located in Azure (however performance will be impacted based on the network connectivity between Azure and the MyWorkDrive server). Additionally, an encrypted copy of the Azure Storage Account connection string is stored on the MyWorkDrive server unlike the managed identity option where nothing is stored on the MyWorkDrive server.
Begin by creating an Azure Storage Account and Azure Blob Container in Azure.
Once the Azure Blob Container and Storage account is created, simply add the azure storage account and container to the MyWorkDrive Server admin panel under Integrations – Azure Blob Storage with the storage account connection string:
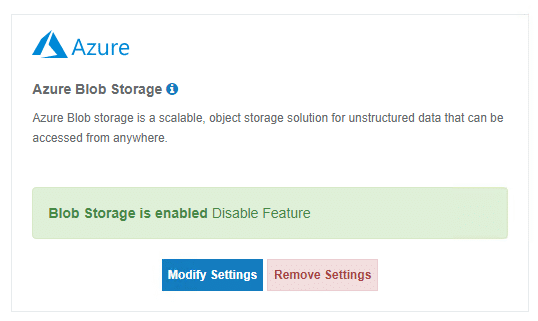
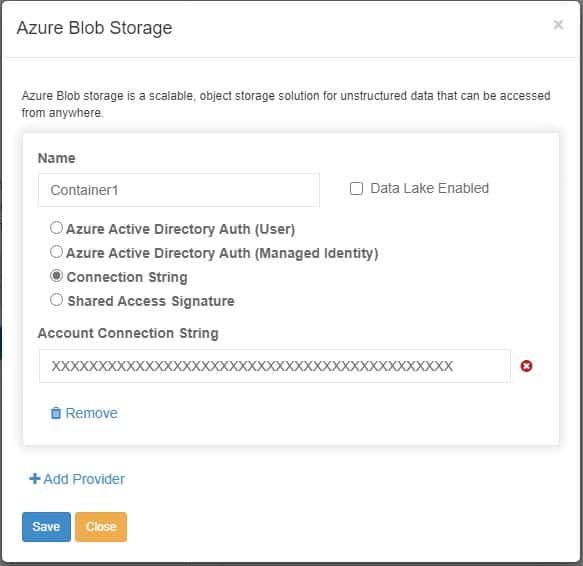
Finally, once the Azure Storage is added to integrations, add a share using that storage and grant Entra ID users or groups permissions to access it (if you prefer to grant all Entra ID users or All Azure AD/Entra Guests permissions to the share, you may use our default groups “All Azure AD Guests” or “All Azure AD Members” instead of assigning individual users or custom groups).
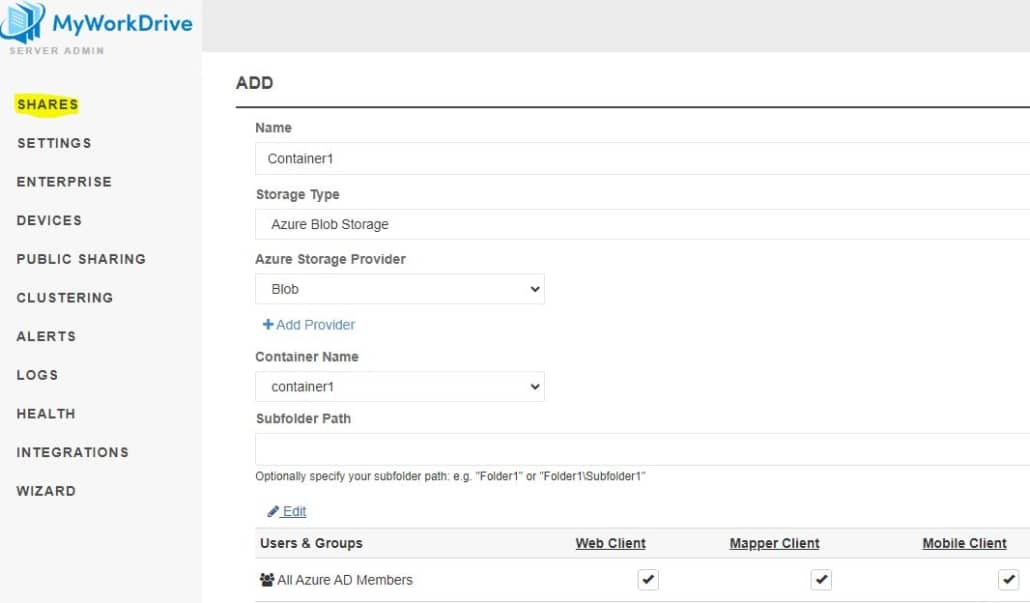
MyWorkDrive file shares over SMB protocol is also available as an option. This is typically used when the MyWorkDrive server is deployed with Active Directory. Deployment using Azure File Shares /SMB impacts performance and responsiveness and requires Azure File Shares Premium storage. Enabling this option also requires completing a set of complex steps in Azure and maintaining a traditional Active Directory domain infrastructure. Our Azure File Shares /Rest API may be better suited for Azure File Share storage when used with MyWorkDrive server in most cases.
Azure file shares support authentication using Active Directory or using Azure File Sync. John Savill provides an detailed overview of Azure Files Authentication using Active Directory here. In this article, we present the steps to connect Azure file shares with MyWorkDrive hosted in Azure, using Active Directory Authentication.
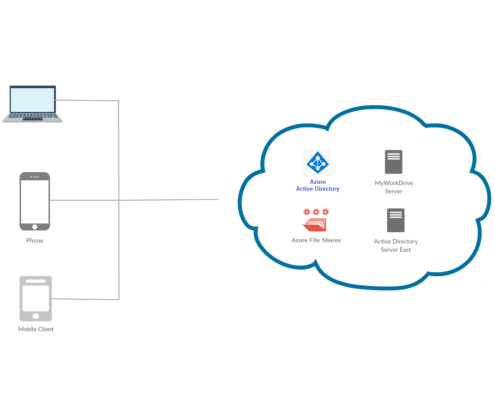
Active Directory Authentication
Azure Files Active Directory integration using your own Active Directory Domain’s managed by you, or using Azure AD Domain Services is fully supported in Azure. Read more about the benefits of Azure Files Active Directory Integration and follow this step by step guidance to get started with integrating Azure file shares with Azure AD Domain Services. To integrate Azure file shares authentication with on-premise Active Directory follow these steps.
With this method, users can login to Azure file shares using their existing AD DS username/passwords stored in Active Directory or synced from Azure AD to Azure AD Domain Services hosted by Azure. Users may also use their Azure AD credentials when synced from AD DS and coupled with MyWorkDrive’s Azure AD SAML/Single Sign-on integration.
For On-premise Active Directory, customers may run and manage their own Active Directory servers in Azure as a virtual machine, or connect an Azure network to on-premise using a VPN tunnel or Azure ExpressRoute. For fastest authentication, we recommend placing a Domain Controller in Azure on the same network as the MyWorkDrive server or using Azure AD Domain Services.
MyWorkDrive has updated our Azure MyWorkDrive Image in the marketplace to allow it to easily join an existing Windows Active Directory domain. This further accelerates the deployment process.
MyWorkDrive Azure File Shares Setup Video.
Prerequisites
- Active Directory must be synced to Azure AD (for setting share permissions).
- Network connectivity from Azure to an AD DC (either a DC running in Azure or ExpresseRoute/VPN connection to a DC on-prem) or utilizing Azure AD Domain Services.
- Azure hosted 2019 Server with RSAT Tools, Joined to Active Directory (use this server to manage Azure file shares and add them to your domain/set permissions).
- Accelerated Networking enabled on Azure Virtual Machine (not available with all machine sizes, typically requires a D series with 2 or more vCPUs)
- Proximity Placement Groups deployed to ensure compute resources are physically located together for optimal performance.
- SMB MultiChannel enabled on AzureFiles, if your performance tier supports it.
- Azure Storage Account Name must not exceed 15 characters (Active Directory Computer Name Requirement).
Create Storage Account
Create a storage account in a resource group in the same Azure Account that hosts your Azure AD. Select the required redundancy and performance options.
Add a file share to your storage account setting share name and quota.
Join Azure Storage Account to Active Directory
Before you start, Map a drive using storage account key: net use : “net use desired-drive-letter: \\storage-account-name.file.core.windows.net\share-name storage-account-key/user:Azure\storage-account-name” from your Windows 2019 server in Azure to ensure you have SMB File Share connectivity.
Enable Azure Files Active Directory Integration
For On-premise Active directory, Enable Azure Files Active Directory Authentication using the steps outlined here. Note: The scripts run best using PowerShell shipped with Server 2019 as they require specific components to be installed as part of the process. The Azure Storage account will be added as a computer account.
For Azure AD Domain Services follow these steps to Enable Azure Files Authentication with Active Directory Domain Services. In this case the Azure Storage Account will be added to Active Directory as a User Account.
If you are using Azure AD Domain services, please make sure that the user accounts created in Active Directory are set so that the password does not expire. If the password expires, users will no longer have access to the Azure Files shares via their AD Credentials and will receive errors on login to MyWorkDrive (see item 1 in the section Unable to mount Azure Files with AD credentials of Microsoft’s Azure Files Connection troubleshooting). You will need to reset the password and re-sync the Kerberos keys.
Even though we will be assigning and using Active Directory NTFS permissions, Azure file shares currently require that permissions must also be set at the Share level using user accounts or groups synced to Azure AD. Assign Identity Share Permissions – For example: “Storage File Data SMB Share Elevated Contributor” allows read, write, delete and modify.
There are three Azure built-in roles for granting share-level permissions to users:
- Storage File Data SMB Share Reader allows read access in Azure Storage file shares over SMB.
- Storage File Data SMB Share Contributor allows read, write, and delete access in Azure Storage file shares over SMB.
- Storage File Data SMB Share Elevated Contributor allows read, write, delete, and modify Windows ACLs in Azure Storage file shares over SMB.
One of these extra Azure AD Share permissions need to be set in addition to Active Directory NTFS permissions regardless of any other Azure AD Share Permissions already in place (e.g. owner). Please note that Active Directory Groups Synced from local domain can be used (Azure AD Connect excludes built-in security groups from directory synchronization).
Microsoft has enabled a way to assign permissions for all users instead of assigning on a user by user basis. Details are available in this updated Microsoft Documentation
Assign NTFS Permissions
Using the same drive mapped earlier with your storage account key, Add NTFS permissions for Active Directory Users Or groups to the mapped drive at the share or desired directory levels. Test the new share NTFS permissions by mapping a drive to the private endpoint address – e.g. \\azure-file-share.file.core.windows.net\share.
Install MyWorkDrive Server
Using a new server or the 2019 Server already joined to Active Directory in Azure, setup MyWorkDrive Server just like you would any MyWorkDrive Server. When adding your first share use your new Azure file share unc path as your file share path: e.g. \\azure-file-share.file.core.windows.net\share.
Optionally enable MyWorkDrive Azure AD Single Sign-On
If users are synced from Active Directory (AD DS) to Azure AD, Users can login using single sign on with their Azure AD credentials using our MyWorkDrive Azure AD SAML/Single Sign-on integration after allowing delegation of the Azure file share computer object in Active Directory (when Azure files shares are added to Active Directory a corresponding computer account object is created).
*MyWorkDrive is not affiliated, associated, authorized, endorsed by, or in any way officially connected with Microsoft Azure. All product and company names are trademarks™ or registered® trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
