How can we help you today?
User’s Domain accounts locked due to failed login attempts
User logins to MyWorkDrive, when your MyWorkDrive server permits login via traditional Username and Password login (not SSO), are login events on Active Directory.
Failed login attempts to MyWorkDrive will count as “attempts” in Active Directory towards an Account Lockout Policy, and may, in some scenarios, cause an account lockout with a low number of login attempts.
MyWorkDrive’s simplified user login will make multiple attempts by assembling usernames based on the domain(s) and upn suffixes in the Active Directory, combined with testing multiple available methods, trying those until it achieves success. The combination of multiple domains, username syntax and software methods will result in multiple attempts on AD from a single login event (depending on what the user enters initially)
For example, if the user logs in with “Scott”, MyWorkDrive will try
scott via wcf
scott via .net
domain1\scott via .net
domain1\scott via wcf
domain2\scott via wcf
domain2\scott via .net
scott@upnsuffix1 via .net
scott@upnsuffix1 via wcf
scott@upnsuffix2 via .net
scott@upnsuffix2 via wcf
Which is ten failed attempts for one login attempt. If the user enters a bad password, and the Account Lockout Policy was set to 3, it would already have achieved a lockout for the user.
There are several ways to improve the user experience and mitigate potential lockouts when users enter bad passwords:
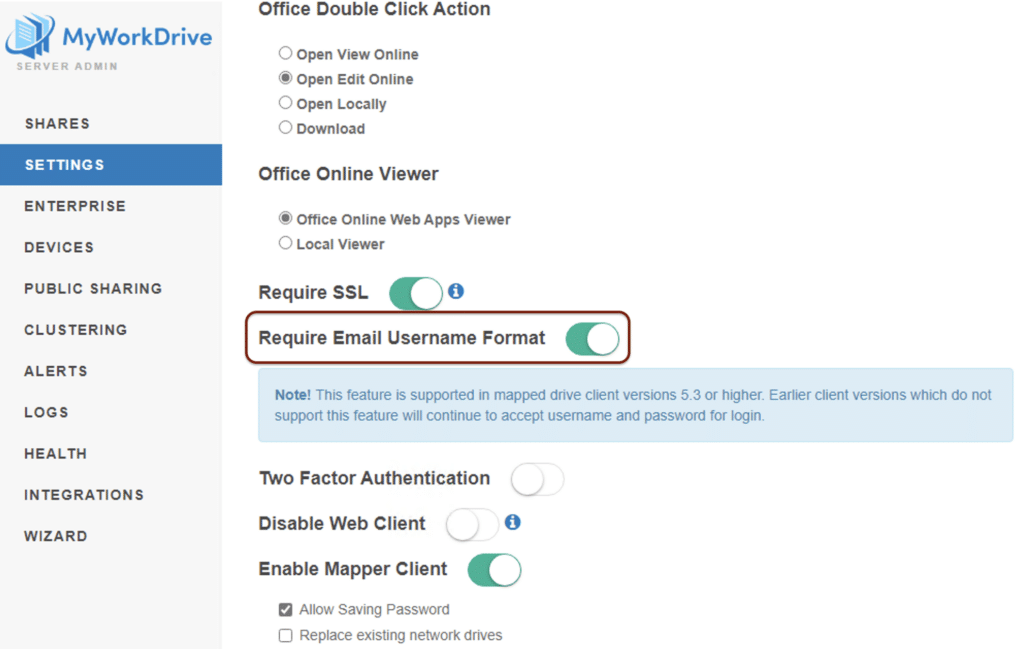
- Require Email username for login. In that case, there will only be three to four login attempts recorded (once to check the account status and once to attempt the login with wcf and .NET – 3 via the web client, 4 via other clients ). This is a setting on the Settings page of MyWorkDrive administration.
- Train your users to login specifying a domain, such as domain\user, which will also result in only three to four login attempt per login.
- Deploy an SSO, where the attempts are moved to the SSO (and typically also require an email cutting out multiple attempts). We have simplified setup for ADFS, AzureAD, OneLogin and Okta and have configuration files which permit you to manually setup any SAML SSO.
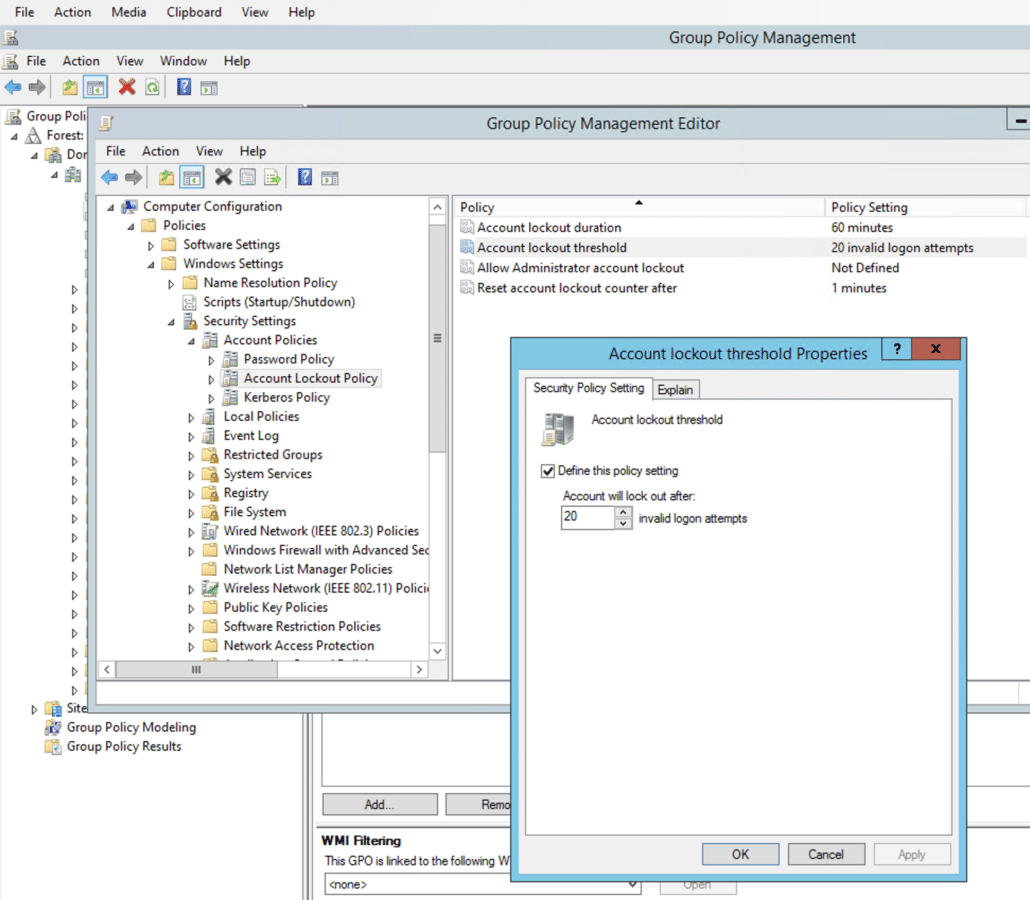
- Set an Account Lockout Policy which permits multiple login attempts without creating a lockout. 10 is a reasonable number for a domain without multiple UPNs or multiple domains where the user can make 2-3 attempts without locking themselves out.
Editing the setting to require email for username in MyWorkDrive:
Editing the allowed password attempts in Group Policy