How can we help you today?
Getting started with MyWorkDrive Version 7 using Entra ID Identity and Azure Storage
Install MyWorkDrive Server version 7 on a new/clean server. Upgrading an existing MyWorkDrive server in order to migrate from Active Directory to Azure AD/Entra ID authentication is not supported. You are strongly encouraged to use new/test storage accounts to avoid risking existing data.
You will note that in some cases in our articles and the Version 7 software that we reference Azure AD, and in some cases Entra ID – we are in process of updating across the board to Entra ID, please treat them as synonymous in our documentation and in the software.
Contents
- What’s new in Version 7
- Advantages
- Requirements
- Downloads
- Significant changes
- Azure Storage Options – Feedback Wanted
- The storage provisioning process
- Supported Clients
- An important note about Network Architecture and Latency
- Upgrading existing MyWorkDrive servers
- Features not supported in Version 7 with Entra ID Auth
- Known Issues
What’s new in Version 7
- The option to use Using Entra ID (Azure AD) as identity instead of Active Directory on a Domain Joined server. See our article on using Entra ID for Identity.
- Using API connections to Azure Storage (Azure Files, Azure Blob) instead of SMB, when using Entra ID identity. See our detailed Azure storage article for comparisons and configuration options
- Using a named account (aka service account) for connections to SMB Storage when using Entra ID identity. See our detailed article on Local/SMB storage for details
- The option to use Azure Files via Connection String when using Active Directory for Identity.
Advantages
- MyWorkDrive version 7 offers the option to use Entra ID instead of Active Directory, for customers who have users in Entra ID.
- MyWorkDrive enables access to Azure Storage via API when using Entra ID for identity, removing the latency in SMB connections to Azure Files. This allows lower storage performance tiers with an improvement in performance.
Requirements
- A Windows server – can be a Physical or Virtual, on prem, or in the cloud. The key difference is that the server does not need to be domain joined (it may be, but being domain joined is not a requirement and Active Directory is not used when using Entra ID identity)
- User accounts in Entra ID (does not require P1 or P2 licenses)
- To use Azure Storage shares, you must have an Azure Storage account (you may have storage accounts you can creates shares in already to connect to, or a Storage account and an Azure File Share can be created as part of the setup process.)
MyWorkDrive version 7 supports Azure File Shares and Azure Blob Storage, with connections via Managed Identity with Entra ID Auth, Entra ID, or connection string. - Administrative access to Azure with the ability to Add App Registrations and edit API permissions (Or grant access to Apps to complete the process for you).
Downloads
Contact sales@myworkdrive.com if you need additional trial keys or existing license key activations for test environments. The Server download requires a login or trial account to download. Click the links below to get started.
Register or Login to Download
For enhancements and fixes, monitor our release notes: Server | Windows Client | macOS Client
Significant changes
The Installer
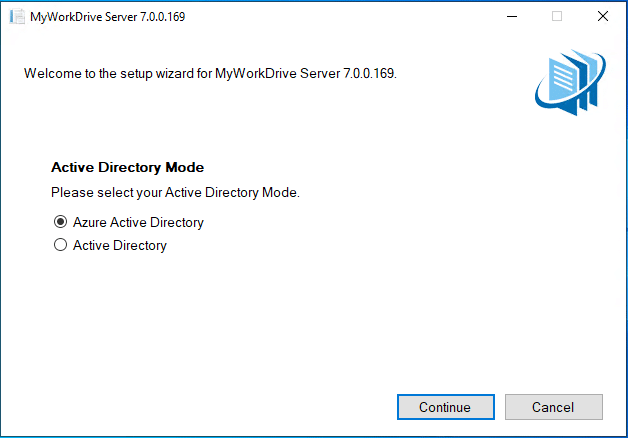
There are two new prompts in the installer. The first is to select between Entra Id (Azure AD) or Active Directory for identity. This is the only place you can make this choice, once installed you cannot switch identity providers.
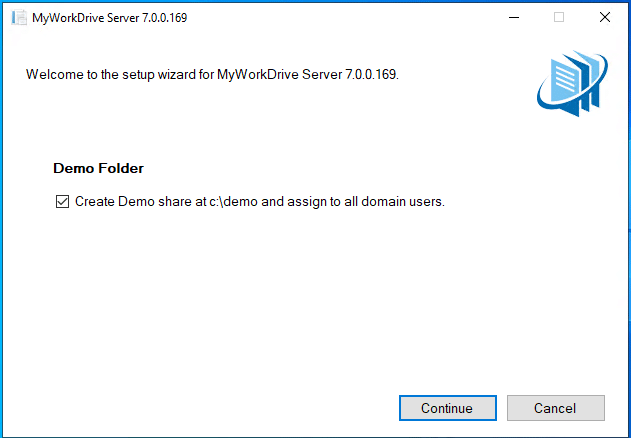
The second is to optionally install a Demo share. This is helpful to verify MyWorkDrive is functioning correctly without needing to also troubleshoot Azure Storage.
Once installed, login to Server Admin using a local system account.
Updates to the Server Setup Wizard
This section includes a walk through of the setup process.
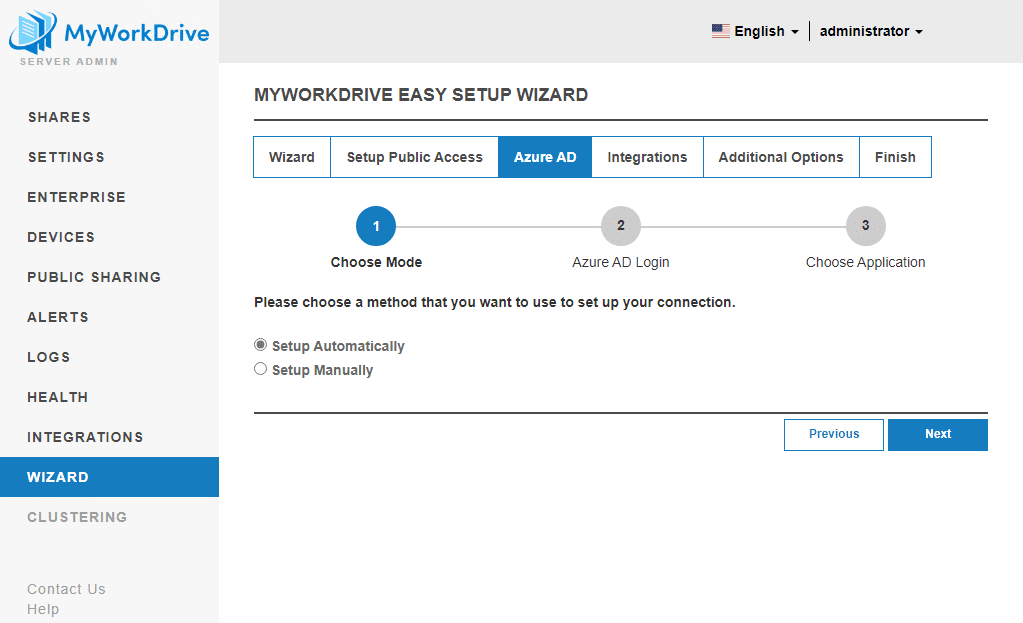
Our updated server setup wizard, which launches the first time you sign in on a clean server, will walk you through the required steps to provision a server using Entra ID auth and create a connection to Azure Storage.
It will connect to Azure and either use our hosted app, or create an app in your tenant to connect to Entra ID for identity. This eliminates the need for you to hand provision your own app in Azure to connect your MyWorkDrive server to Entra ID (manually creating your own app is supported – see our Entra ID Article).
It will offer to create a share in Azure Files for you. If you do not add one, you can create one, later.
If you choose to create your own app in your Azure tenant, the wizard will prompt you to use it for all three options in Azure
- Entra ID Identity
- Storage Access (Azure, OneDrive, SharePoint)
- Office Online Editing
After you setup the server’s internet connection (choose Cloudflare if you are just testing, to make it easy. Just note you need to allow port 7844 OUTBOUND (no inbound connection is required). You also need 443 outbound to licensing.wanpath.net to license and activate the server and 443 outbound to Azure.)
Then you’ll setup your connection to Azure for Entra ID. Manually requires you to setup an app in Azure and enter a Key/Secret. We suggest automatic, which uses a hosted app from MyWorkDrive.
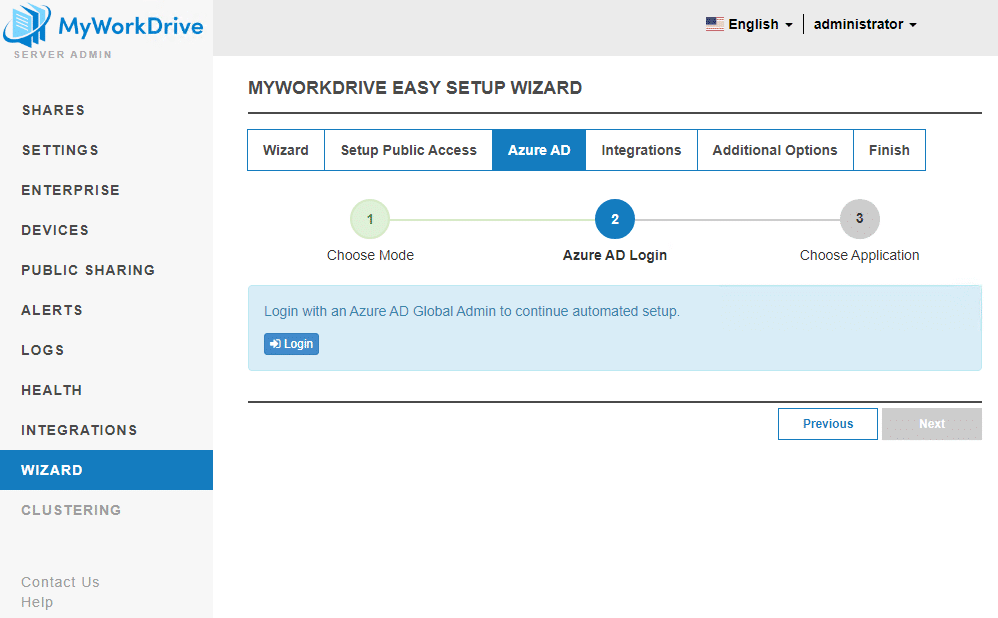
Next, you need to sign in to Azure as a tenant admin. Click the link and follow the instructions to authenticate to Azure and approve the MyWorkDrive app to perform setup for you.
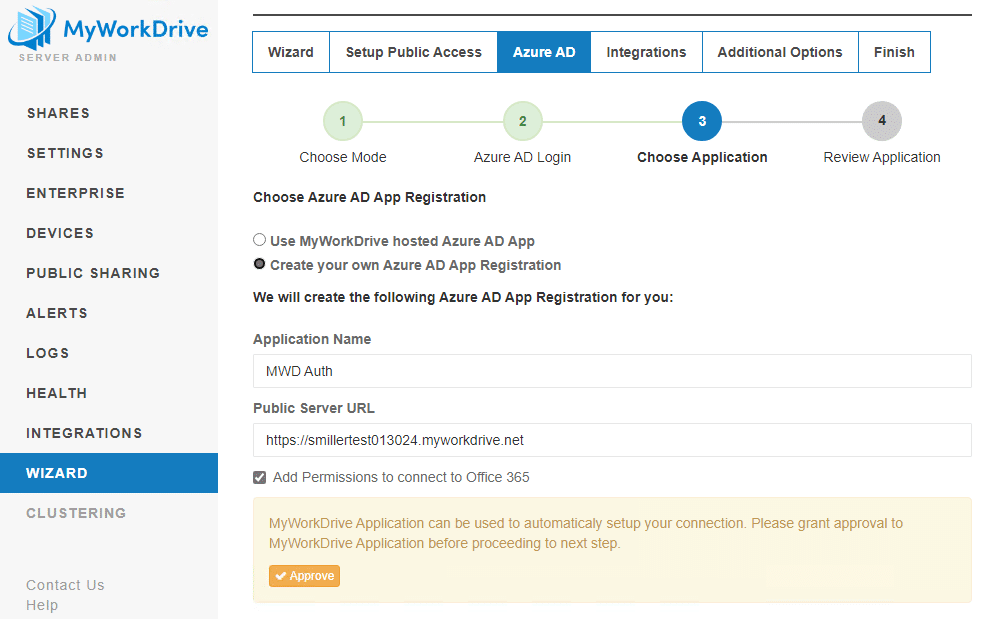
We suggest choosing the “Create your own App Registration” model. Name it something easy to identify in App Registrations in case you need to find it to make changes later (such as the URL, if you change it). Make sure you complete any prompts shown in the wizard, such as this one asking us to approve the application we’ve created.
When you complete the App Creation process for Entra ID, you’ll have an app in your Azure tenant that your MyWorkDrive server connects to. You won’t be using any resources hosted by MyWorkDrive if you use the “Create your own App Registration” option we recommend.
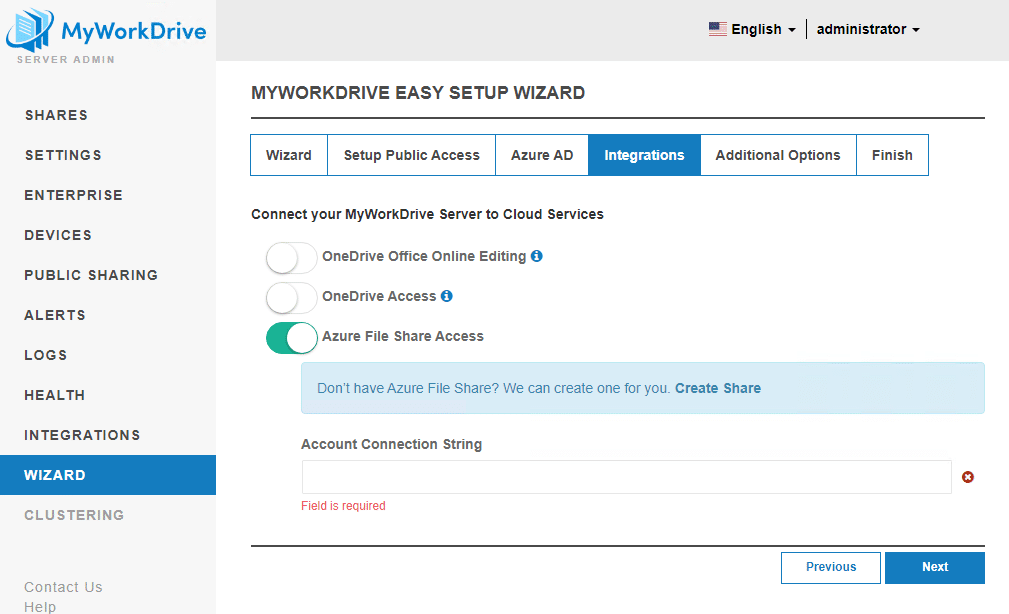
Next in the wizard is storage. The Wizard is going to prompt you to connect an Azure File Share. Use the create link to open a new window and create a share in your own storage.
Don’t worry that it only lets you create one share with the connection string method. If you want to setup other Azure Storage or other share types, you can do that after the wizard.
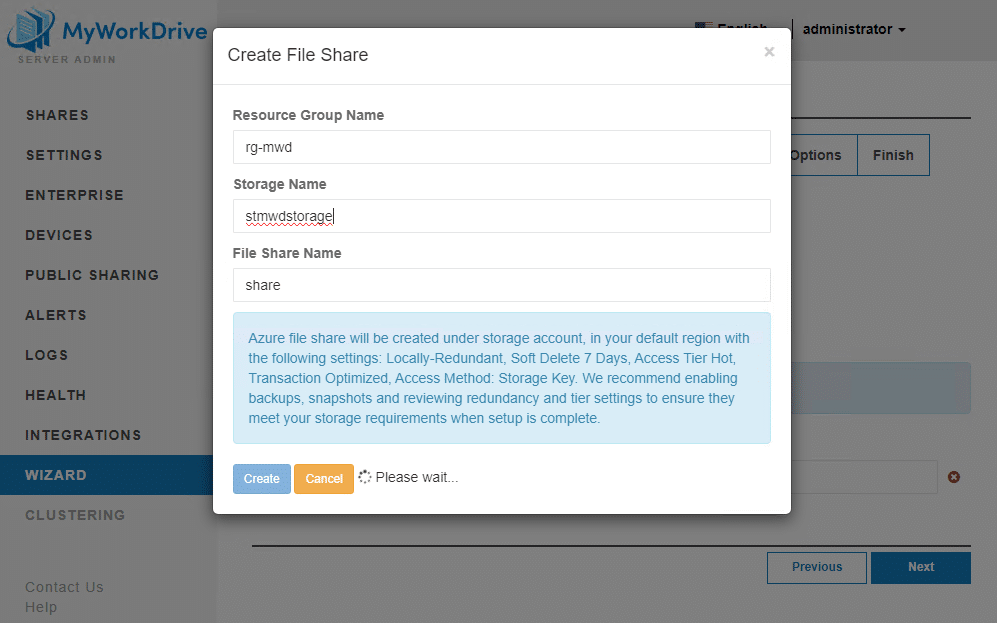
Enter values for the Resource Group, Storage Name and Share Name which you’ll be able to find later in Azure to make changes. the rg- and st prefixes are as-recommended by Microsoft.
Take note of the information in the blue block about the configuration values. These shares are created/configured with the minimum and are not setup with redundance or backup – so do not put them in production without making appropriate updates in Azure.
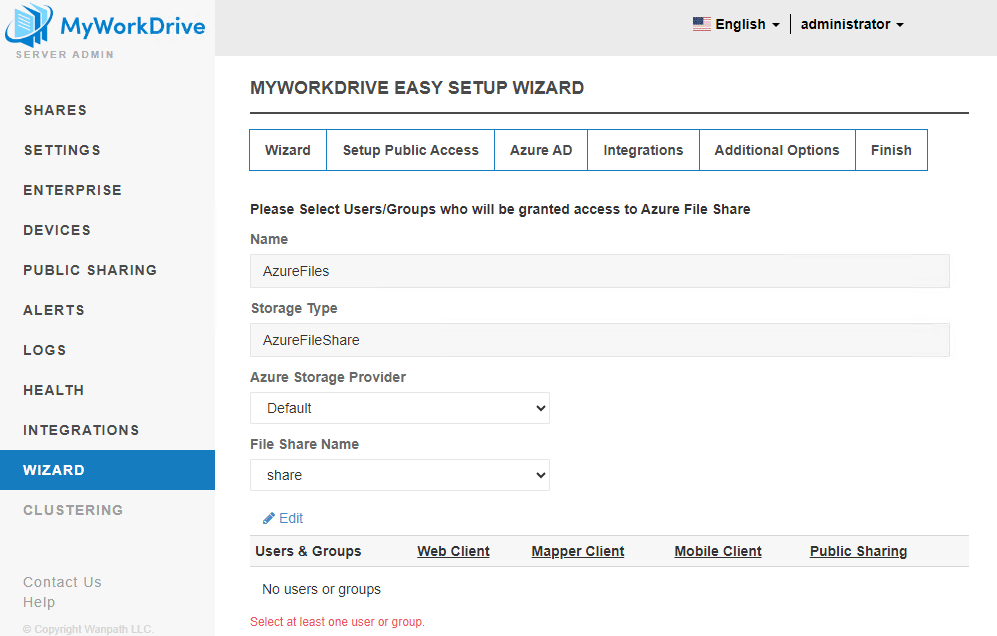
After you create the storage, it is critical that you use the Edit button to assign users and groups to the share (you won’t be able to save and continue until you do). Permissions work differently in MyWorkDrive version 7 when using Entra ID as discussed in this linked section.
That’s the last major step. There are a few additional options and then you’ll have completed the wizard!
At this point you should have –
- A MyWorkDrive Version 7 server installed on Windows
- Published on a Cloudflare URL (https://something.myworkdrive.net)
- Connected to Entra ID for user identity
- With a Local Demo and Azure file share
When you get the email confirming your site is provisioned, open up your favorite browser and login with a user who has permission to the shares.
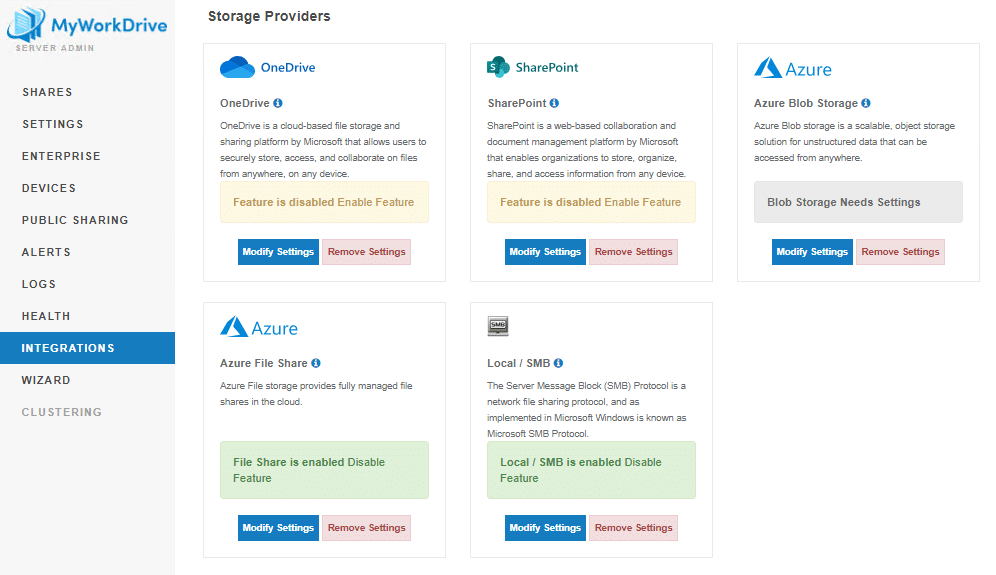
Storage in Integrations.
Three new storage types exist in Integrations
Local/SMB – for connecting to SMB storage using a named user / service account. Details are available in this article
Azure Files – for connecting to Azure File Shares. Details, here.
Azure Blob – for connecting to Azure Blob. Details, here.
Entra ID identity supports OneDrive and SharePoint storage as well.
Support for Managed Identity
Version 7 supports Managed Identity for servers hosted in Azure. This permits you to grant your server access to storage accounts without the need to store credentials, tokens or connection strings on the server itself.
Key Storage Differences
SMB with Entra ID
SMB is treated different when using Entra Id from a domain joined active directory server. When domain joined, MyWorkDrive accesses SMB shares under the context of the signed-in user. When using Entra ID, you define the user account which should be used to access the shares – so all access is done as the named user saved in MyWorkDrive, not the individual users who are accessing.
When using a domain joined server with active directory, the granular permissions on shares reflect the NTFS permissions imported from the SMB share. With Version 7, the granular permissions are defined by you on share creation using the users and groups in your Entra ID.
The permissions will define who is presented the share in the MyWorkDrive client (web, mobile, desktop). Their permissions will come from the permissions defined in Azure or on the storage account user (smb).
Our Granular Permissions article is updated regarding Version 7 changes
We’ve added two Groups to make granting access easier for “All company” type scenarios.
All Entra ID Members
This is everyone who has a member user account in Entra ID. Does not include Guests or other user types.
All Entra ID Guests
This is everyone who is an invited b2b guest of your tenant.
Just because they can see the share in the client does not necessarily mean they have access. Their underlying access may be restricted by their permissions in Entra ID, their role on the share/blob/container or the user account defined in SMB.
Public Sharing
Public Sharing uses different methods to generate share links from previous, as with Entra ID Identity, we no longer have NTFS permissions to rely on for access. Public sharing does not work with all share connection methods.
Public sharing works with
- SMB Share
- Local Share
- OneDrive
- SharePoint
- Azure File Share, using Connection String
- Azure File Share, using Entra ID/Managed Identity
- Azure Blob, using – Entra ID/Managed Identity
- Azure Blob, using Connection String
Public share links will not be available for
- Azure Blob using Entra ID without managed identity.
- Azure File Share using Entra ID without managed identity.
Azure Storage Options – Feedback Wanted
It is theoretically possible to support a number of connection options to Azure File Shares and Azure Blob storage
- Entra ID
- Managed Identity (with Entra ID)
- Connection String
The different storage methods provide different security options.
Connection String grants complete access to all users you permit to access the share (limited with Granular Permissions at the share level; there is no file/folder level permissioning). So they seem redundant. We’d love to know if you have a preference of one over the other (or for either of them, at all)
Entra ID moves the permission to the share itself (roles in Azure), so you wouldn’t have a connection to storage stored in MyWorkDrive (the key/token/string is encrypted, but still stored). With Entra ID, there’s just a storage account name and share name stored. We feel this is a preferred approach.
A measure safer is Managed Identity with Entra ID – this is where you grant the role to the VM, not users. However, this only works with VMs hosted in Azure. If you are keeping a VM on prem or in another cloud service, you wouldn’t be able to use Managed Identity.
We welcome your feedback on the connection options. Our goal will be to offer what customers want, balancing security and (hopefully) minimizing the options to cut down on QA, Development and Support.
We have trimmed the options some – you’ll note our Storage Guide only mentions Managed Identity for Blob and doesn’t mention SAS. These changes are based on preview customer feedback and product research.
The storage provisioning process
There are two steps to provision storage
- Add a storage connection in Integrations. You’ll make a connection to the storage account using the appropriate settings (Managed Identity, Connection String, Entra ID Auth)
- Add the Share in Shares. You’ll select the storage connection and then define the share/container. In some cases you may be required to type in the name of the share or container from Azure Storage (as we do not always have permission to look up the share/container). Make sure you type it in correctly.
– You can optionally set a specific subfolder of the share when provisioning the share
– Make sure you define permissions for the share, there is no import feature with Entra ID identity.
Learn more about provisioning Azure Storage shares, here
Supported Clients
The Release of MyWorkDrive version 7 is backwards compatible with earlier clients when using Active Directory for user identity. It requires version 7 clients for Entra ID identity. The use of version 7 clients with any version 7 server configuration is very strongly recommended.
We have worked hard to keep the user experience consistent between Active Directory and Entra ID identity, and SMB and Azure storage.
The key differences –
The initial login, after connection in the client, will present a prompt to Login with Microsoft. Once the user clicks, they will get an Entra ID login similar to what they had with SAML.
If your share uses Entra ID Auth for permissions, the user will see a secondary login window flash which uses their existing Entra ID session to authenticate the first time they access a share. This is the same as the Auth to OneDrive/SharePoint in version 6.4. In most cases, users will not need to interact with the secondary login window and may not even notice it.
An important note about Network Architecture and Latency
MyWorkDrive will provide the best user experience when the MyWorkDrive server is placed on the same network as the File Shares or Storage. Installing MyWorkDrive remote from the storage adds latency as the MyWorkDrive server has to fetch files and directories from storage before serving them to the client (and vice-versa when saving). Having the MyWorkDrive server on prem and using Storage in Azure or OneDrive/SharePoint will result in a slower connection than using local storage on-prem, or keeping the server in Azure as a VM.
It is important to note that if you are using Azure Storage, you will get the best performance when running MyWorkdrive on a VM in Azure, with a local connection to the storage (using Accelerated Networking on the VM and Proximity Placement groups).
MyWorkDrive will work reaching Azure Storage over the internet, but users will experience a delay in accessing files and directories due to the real-time-access nature of MyWorkDrive.
Upgrading existing MyWorkDrive servers
Its important to note that if you upgrade an existing server which is domain joined using Active Directory for identity, It will continue to work that way and the Entra ID identity option and most of the features mentioned above will not be available. There is no upgrade path between Active Directory on a Domain Joined server and Entra ID for identity, because of the way storage is provisioned and user access is granted.
To deploy a MyWorkDrive server using Entra ID in an environment currently using Active Directory, we advise deploying a new MyWorkDrive server and configuring from scratch.
Shares are provisioned differently. For SMB shares, NTFS Permissions are not used in the context of the user – they are used under the context of a named account (service account) you configure with access. The permissions cannot be migrated.
The new options for permission access use elements in Azure – Connection String, native Entra ID, Managed identity – which are not options for legacy SMB Shares.
SAML is not supported, authentication via Entra ID is done natively. As such, Duo is not supported as a separate configuration (you would configure multi-factor as part of conditional Access in Entra ID).
Features not supported in Version 7 with Entra ID Auth
Duo MFA (configure with conditional access in Entra ID)
ADFS (can be configured in Entra ID as the IDP)
SAML connections (other IDPs can be configured in Entra ID)
Guest User Access on Shares (Invite B2B guests natively in Entra ID)
Search (Windows Search is not available via SMB, dTSearch does not index Azure Storage)
WebDav
Previous Versions
User Home Folders from AD Profiles
Known Issues
MyWorkDrive Version 7 is in Production. Please report any bugs you find to us via our helpdesk.
Updated as of Production release 7.0.1.4
- Large Uploads, greater than 1000 files or 1gb in size may partially error during upload
(this is more commonly noted when MyWorkDrive is installed remote from Azure Storage – on Prem or in a non-Azure cloud) - Azure Roles that generate a JWT token with more than the acceptable limit to groups may cause user logins to failAzure AD does impose limits on the number of groups that can be included in a token due to size constraints. For JWT tokens, the limit is 200 groups, and for SAML tokens, it’s 150 groups. If a user’s group memberships exceed these limits, an overage claim indicates that the application must query Microsoft Graph to retrieve the user’s group memberships.We’ve noticed this in our own lab using Azure AD (Entra ID) to sign into network resources – hybrid domain joined RDP, for example.
- Health Dashboard has not been updated with Entra ID identity or Azure storage options
- MS App Proxy is not supported with Entra ID identity
Please monitor release notes for resolution to these and other reported bugs/issues. Server | Windows Client