¿Cómo podemos ayudarle hoy?
Publicación de MyWorkDrive con Nginx Proxy/Proxy inverso
Contenido
Instalación
ventanas
Una instalación de nginx en Windows tiene limitaciones que no nos sentimos cómodos soportando. Aquí hay una lista de esas limitaciones:
Problemas conocidos
- Aunque se pueden iniciar varios trabajadores, sólo uno de ellos realiza realmente algún trabajo.
- La funcionalidad de proxy UDP no es compatible.
Posibles mejoras futuras
- Ejecutando como servicio.
- Usar los puertos de finalización de E/S como método de procesamiento de conexión.
- Usar múltiples subprocesos de trabajo dentro de un solo proceso de trabajo.
linux
Instalaremos nginx en Linux. Aquí hay un enlace con instrucciones para realizar una instalación básica de nginx dependiendo de su versión de Linux: https://docs.nginx.com/nginx/admin-guide/installing-nginx/installing-nginx-open-source/
Configuración
Proxy inverso
En lugar de utilizar nuestro Conector web en la nube para un proxy inverso, se podría aprovechar un servidor Nginx en su entorno. Aquí hay un ejemplo de configuración de Nginx que podría usarse:
servidor
#Configura el servidor para escuchar 443/SSL tanto en ipv6 como en ipv4
escuchar [::]:443 ssl ipv6only=on;
escuchar 443 ssl;
#Configura la ubicación del certificado SSL. Este ejemplo utiliza un certificado existente en lugar de aprovechar Let's Encrypt.
ssl_certificate /etc/nginx/certificates/cert.cer;
ssl_certificate_key /etc/nginx/certificates/key.key;
raíz /var/www/html;
nombre del servidor _;
#Configura su dirección DNS nginx para que apunte al nombre de su clúster (configurado en la parte superior) y pase el tráfico a ellos junto con los encabezados asociados.
ubicación / {
proxy_pass https://MWD-Server1.domain.tld:443;
proxy_http_versión 1.1;
proxy_set_header Actualizar $http_upgrade;
proxy_set_header Conexión 'actualización';
proxy_set_header Anfitrión $host;
proxy_cache_bypass $http_upgrade;
}
}
#El siguiente bloque reenvía todo el tráfico http a https
servidor {
escuchar 80;
escuchar [::]:80;
nombre del servidor _;
devolver 301 https://$host$request_uri;
}
Equilibrador de carga
Si aprovecha un Nginx para un proxy inverso, configurar MyWorkDrive para que esté en un clúster activo-activo con la siguiente configuración de Nginx le permitiría equilibrar la carga entre los dos:
#Configura el nombre de su clúster (en este ejemplo, "clúster"), establece el método para identificar sesiones únicas (en este ejemplo, convierte la IP remota en binaria), establece las direcciones del servidor y los puertos en su clúster.
clúster ascendente {
hash $binary_remote_addr;
servidor MWD-Servidor1.dominio.tld:443;
servidor MWD-Servidor2.dominio.tld:443;
}
servidor {
#Configura el servidor para escuchar 443/SSL en ipv6 e ipv4
escuchar [::]:443 ssl ipv6only=on;
escuchar 443 ssl;
#Configura la ubicación del certificado SSL. Este ejemplo utiliza un certificado existente en lugar de aprovechar Let's Encrypt.
ssl_certificate /etc/nginx/certificates/cert.cer;
ssl_certificate_key /etc/nginx/certificates/key.key;
raíz /var/www/html;
nombre del servidor _;
#Configura su dirección DNS nginx para que apunte al nombre de su clúster (configurado en la parte superior) y pase el tráfico a ellos junto con los encabezados asociados.
ubicación / {
proxy_pass https://clúster;
proxy_http_versión 1.1;
proxy_set_header Actualizar $http_upgrade;
proxy_set_header Conexión 'actualización';
proxy_set_header Anfitrión $host;
proxy_cache_bypass $http_upgrade;
}
}
#El siguiente bloque reenvía todo el tráfico http a https
servidor {
escuchar 80;
escuchar [::]:80;
devolver 301 https://$host$request_uri;
}
SSL
Certificado público
Nginx tiene instrucciones sobre cómo instalar su propio certificado. Las instrucciones están disponibles aquí: https://nginx.org/en/docs/http/configuring_https_servers.html
Ciframos el certificado
Nginx tiene instrucciones sobre cómo instalar Let's Encrypt Client para obtener un certificado SAN gratuito para su dominio. Las instrucciones están disponibles aquí: https://www.nginx.com/blog/using-free-ssltls-certificates-from-lets-encrypt-with-nginx/
Certificado autofirmado de MyWorkDrive
El uso de un certificado Let's Encrypt o su propio certificado público para su proxy inverso le permite al administrador de MyWorkDrive usar un certificado autofirmado y aprovechar el cifrado de extremo a extremo entre nginx y MyWorkDrive. Para habilitar un certificado autofirmado en MyWorkDrive:
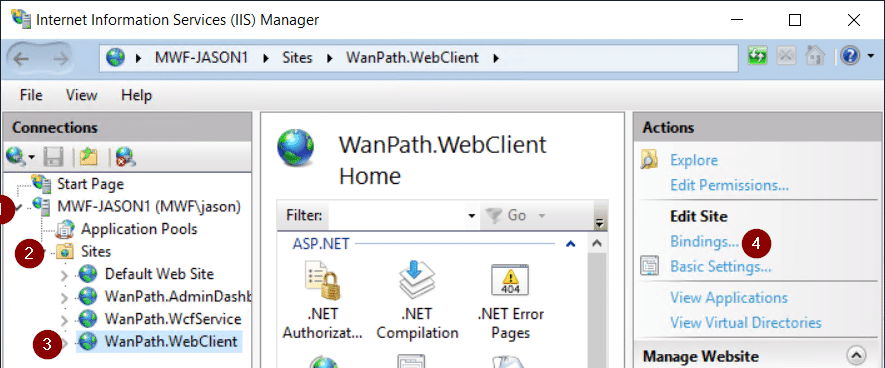
- Abra IIS y expanda los sitios de su servidor
- Expandir sitios
- Seleccione WanPath.WebClient
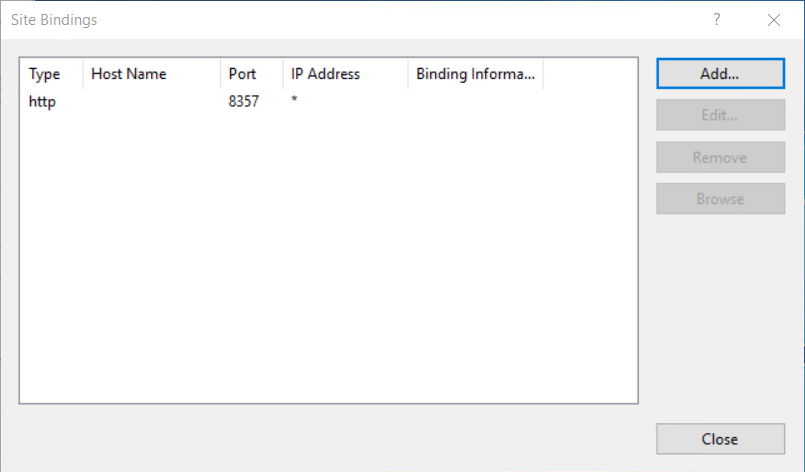
- Haga clic en Enlaces en el panel derecho
5. En la página de enlaces, haga clic en Agregar...
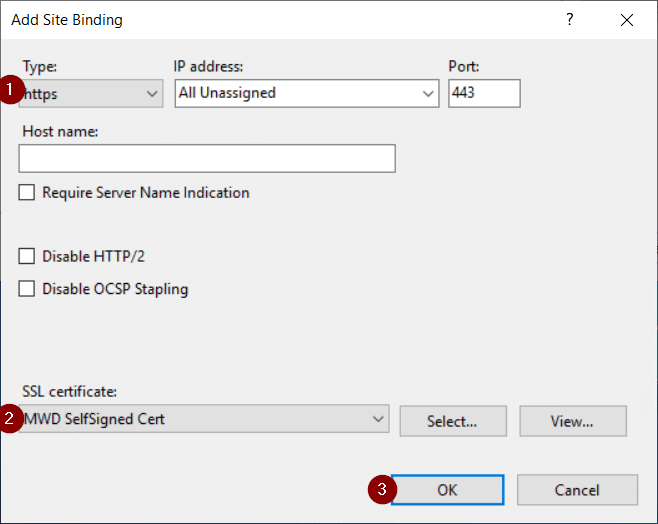
6. En la página Agregar enlace de sitio, cambie Tipo a https. Deje la dirección IP y el puerto como predeterminados.
7. En Certificado SSL, seleccione Certificado autofirmado MWD.
8. Seleccione Aceptar.
9. Edite su configuración de Nginx para que apunte a su servidor MyWorkDrive y especifique manualmente el puerto 443.
Como referencia, consulte
https://docs.nginx.com/nginx/admin-guide/web-server/reverse-proxy/