Overview
MyWorkDrive provides secure web access to file shares and storage—without requiring private endpoints, VPN, RDS, or VDI. End users can access their files and folders in multiple ways:
-
Through a browser using the web file manager
-
Directly in File Explorer or Finder with mapped drive clients
-
On iOS/Android devices with our mobile apps or the mobile mini web browser
The MyWorkDrive server can be connected with either Active Directory or Entra ID (Azure AD) for the user database. Storage options supported include Windows File Shares, local storage, Azure File Shares, Azure Blobs, OneDrive, and SharePoint sites.
The public URL of the MyWorkDrive server is published with IIS. Setup will install the IIS services automatically, as well as all other necessary prerequisites.
In addition to making the file shares available over a web browser, the MyWorkDrive server enables our API for securely mapping drives using our mapped drive & mobile clients, as well as Office online editing in Office 365, Office Online Local Server, and ONLYOFFICE. For additional details, read the Technical Overview Support Doc and the MyWorkDrive security overview.
File storage access methods vary between servers using Entra ID identity and Active Directory identity. Details about the differences are available in this article
We have a list of features which significantly differ between servers using Entra ID identity and Active Directory identity, here
View the most recent setup video here, which includes a discussion of the differences in User Directory and Storage starting with the MyWorkDrive server version 7:
Planning your Installation
Before starting setup, you will want to know the answer to a couple of basic questions:
-
What user directory will I use?
- MyWorkDrive supports using Active Directory (on-prem or in the cloud) as well as Entra ID.
-
What storage will I use?
- MyWorkDrive supports local storage, SMB file shares (via NAS/SAN, Windows File Shares, and Azure File Shares), Azure File Shares natively (via Connection String or Entra ID), Azure Blob Storage, OneDrive, and SharePoint.
You will want to have the necessary security roles present to complete your install. Depending on your installation choices, those might include:
-
Domain Admin
-
Firewall/DNS Admin
-
File Storage Admin
-
Azure Storage Admin
-
Azure Global Admin
Additional Details about the roles and effort required for different features are available in this article.
The rest of this document will explain the various setup options and roles required so you can plan your installation.
If you have questions about the required roles or installation process, please reach out to your MyWorkDrive representative or contact Support via email support@myworkdrive.com or submit a ticket using our Help Desk Portal.
Server Setup
Before you begin, ensure you have regular and complete backups of your file server(s) and storage. In addition, we recommend volume shadow copy be enabled with hourly snapshots on all Windows file share drives.
Download MyWorkDrive
Login to your portal account and download the MyWorkDrive server on the server where you intend to complete the install.
Step 1: Server Prerequisites
-
Domain-joined (Active Directory Mode) or standalone (Entra ID mode), fully patched server running Production Windows 2016 – 2022 Server dedicated to MyWorkDrive. OS versions that are no longer in mainline support or are preview/pre-production/release candidate are not supported.
-
Ability to install/update/run specific versions of .NET, C++, and IIS (required versions will be installed or upgraded during install automatically, which may prompt a reboot).
-
Minimum 4 GB ram, 2 virtual CPUs if installed as a virtual machine – for larger enterprises, please review our Server Sizing Guide. If installing in Microsoft Azure, a D series is recommended as the minimum, with SSD (premium not required). If installing in AWS EC2, a T series is recommended.
-
A minimum of 60 GB of disk space is recommended to accommodate Windows, Windows updates, installation of MyWorkDrive, logs, and temp files. Higher log levels or longer log retention will require additional disk space.
-
Direct internet access on the server running MyWorkDrive (no proxy services) to activate and initialize the software with outgoing firewall access to ports 443, 7844. For additional details on outbound ports for locked-down environments, review our firewall settings guide.
-
Antivirus software products installed on the MWD server can interfere with MyWorkDrive processes. Review our Antivirus Settings Article.
-
Incoming port 443 (if you will be using your own domain name & SSL certificate).
-
The server must be part of a Windows Active Directory domain, ideally a member server, if using Active Directory.
-
Computer account and user accounts must have permission to query user attributes and group membership on Active Directory. If using Active Directory.
-
The server where MyWorkDrive is installed should be on the same LAN or same Azure tenant as the file storage for optimal performance.
-
We do not support installing MyWorkDrive on a server that is running Small Business Server/Windows Server Essentials, Microsoft Exchange, other IIS sites, or any software that includes IIS, .NET, or C++ components.
-
If shares are accessed through DFS, ADFS, or SAML for authentication, it is necessary to enable delegation so that the MWD Server trusts these servers for delegation. See the support article here.
-
Additional client requirements and limitations are located in our support article here.
Step 2: Verify & Run the MyWorkDrive Server Setup
-
Log onto the server as a user with admin rights on the server (Local Admin for stand-alone servers, Domain Admin for Active Directory).
-
Download the latest MyWorkDrive-Setup.exe from the Customer Portal and run it as administrator.
-
Select the appropriate user source during install, and answer prerequisite questions during setup.
-
Your server must be able to reach licensing.myworkdrive.net (formerly licensing.wanpath.net) on port 443 to complete the licensing process. Additional Firewall Settings
-
Setup will complete in a few minutes. When complete, it will be ready to log in to begin configuration. No other external preparation is necessary.
Step 3: Post Setup: Admin Portal Login and Setup Wizard
Starting with 6.4, MyWorkDrive’s control panel includes an option to open the admin panel in a built-in window, in addition to the traditional "Open in Browser" link that launches the default browser.
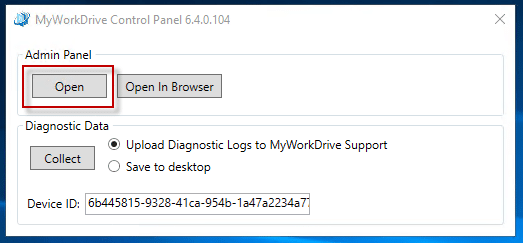
We leverage Microsoft’s WebView2, which launches an embedded instance of Microsoft Edge, removing the need to install a browser on your MyWorkDrive server to administer MyWorkDrive.
More information about WebView 2 is available here.
- Open the MyWorkDrive Admin page from the control panel, or via a browser at http://127.0.0.1:8358) on the MyWorkDrive server (administering MyWorkDrive is only supported from the server desktop).
- Login using an Active Directory Domain Account which is a member of domain admins and has local administrator rights on the MyWorkDrive server (Active directory mode), or a Local Administrator (Entra ID mode). When using Active Directory, the Domain Admin account will have permissions to read network file shares. For example, the domain admin credentials (mycompany\administrator or administrator@mycompany.local). Be careful to only log in using a domain account. _There are no default users in MyWorkDrive_. All user accounts are looked up from the user database, domain, or machine credentials – for user access and administrator access.
- Be prepared to sign in to Azure with an Azure Global Admin if you are setting up Entra ID mode, to create and approve apps and grant consent to API permissions.
- Be aware that Internet Explorer cannot be used in the admin panel. Use our link in our control panel app with the built-in Edge WebView 2, New Edge (Chromium-based), or install Chrome. The technologies used in the admin portal, notably JavaScript, are not well supported in Internet Explorer.
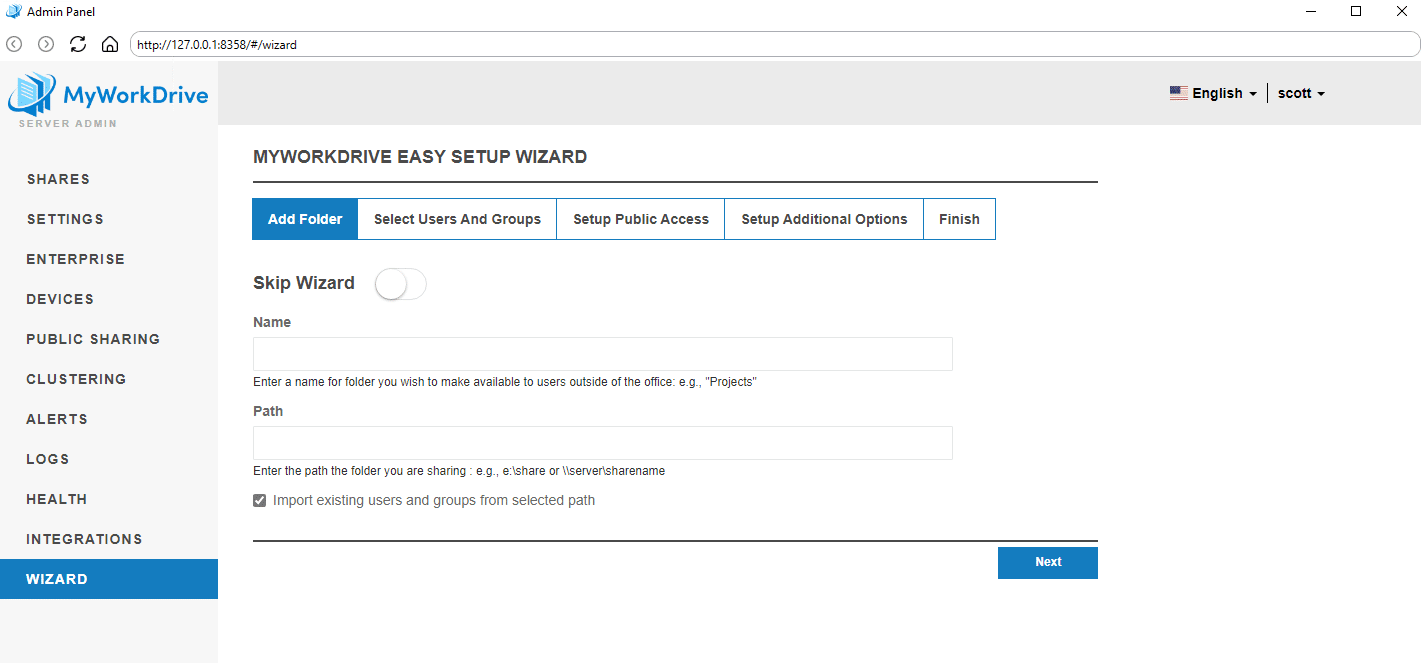
- The setup wizard will launch on first login or if Azure connection setup has not been completed (Entra ID mode). The wizard will walk through initial setup questions, including publishing via Cloud Web Connector, Azure connection setup (Entra ID mode), enabling Office 365 editing, share setup, and a few common optional features.
- Once the Azure connection is complete (Entra ID Mode), at least one share is set up, and the server is made public (using myworkdrive.net domain or your own host name - see below), you may begin using MyWorkDrive.
- You will receive an email when your site is ready if using a *.myworkdrive.net domain with our Cloud Web Connector – this may take up to 15 minutes. Your server must be able to reach Cloudflare via port 7844 outbound in order to use the Cloud Web Connector.
Step 4: Additional Share Setup
In most cases, administrators have more shares to set up than what is prompted in the wizard, or may wish to set up share types that are not included in the wizard. If no shares are already set up (new installs), the MyWorkDrive admin panel will start with the Add Shares section already open; otherwise, click Add to set up new shares.
The share connection methods that are available and the method of adding them vary slightly between Active Directory and Entra ID modes.
This article outlines the available storage options depending on the MyWorkDrive user source.
SMB
With NTFS on Active Directory
Note: existing file share permissions on your file server should be everyone full control, and only utilize NTFS to limit user file permissions (where users should only be given Modify and not Full NTFS permissions as to prevent file ownership issues). As a security precaution, MyWorkDrive passes through authentication and can limit permissions further, but not grant NTFS permissions to any shares. Users must already have NTFS and share permissions to the files before adding them to MyWorkDrive. To prevent users from seeing files they don’t have rights to, enable Access Based Enumeration on the share. For more information on cleaning up ownership and NTFS permissions, see our Windows File Sharing Article.
For very large organizations with 100s of shares, MyWorkDrive supports importing shares from a CSV file share list. Contact Support for additional details.
Via Service Account with Entra ID
Instructions for using Service Accounts to add SMB shares with Entra ID are available here.
Azure File Share via SMB
Azure File Share via SMB does not require specific product support as it is a native SMB implementation. It works with all versions of the product that use Active Directory Identity and SMB Storage.
It does require setup with Azure. Go here for AzureFile Share setup via SMB.
Azure File Share via SMB is only available when using a domain-joined server and Active Directory user mode.
Azure File Share, Azure Blob Storage via API
Azure File Shares and Azure Blob Storage via API are introduced in version 7.0. There are options to use Azure File Share via API with both Active Directory and Entra ID. Not all connection options are available in all configurations.
See here for a detailed discussion of storage options in Version 7.
OneDrive / SharePoint
Support for OneDrive/SharePoint was added in version 6.4.1. It is supported with Active Directory or Entra ID identity providers.
See here for OneDrive setup and SharePoint setup.
Note About Permissions
When using Active Directory, the import feature imports the NTFS permissions from the SMB shares, and you have the option to remove or make changes to the share access via granular permissions.
When using non-NTFS Storage, such as OneDrive, SharePoint, or Azure Storage via API, the import feature and granular permissions define who is shown the shares when logging in to MyWorkDrive. The underlying permissions are dependent either on the storage connection, OR the roles/permissions on the storage itself.
Please review the storage options and chart for version 7 using the storage API for additional details.
Step 5: Proceed to Accessing the Client File Web Access Site to Verify Functionality
- Access the local site for basic testing of the site at http://127.0.0.1:8357 on the MyWorkDrive server itself. No ports are open/bound on the server for remote access by default, or via the Cloud Web Connector address (*.myworkdrive.net) you configured in Server Admin.
- Remember, there are no user accounts created in MyWorkDrive. Your users will sign in using their Domain Credentials, SSO Login, or Microsoft Credentials, depending on your configuration.
- Log in using various users to test web file access, shares, and home drive access (if allowed) on the server.
Step 6: Publish to the Cloud
Publishing to end users might be in the form of a public website on the internet, or a private website available internally or when connected to existing network resources (VPN, RDS, VDI, etc). For a detailed discussion on publishing your server to the internet, including proxy/reverse proxy and load balancing options, visit our guide to publishing your MyWorkDrive server. When you have completed the setup, the two most common methods of publishing your server are:
Cloud Connector
https://YourCompany.MyWorkDrive.net
Our Cloud Web Connector is a great way to make your server available quickly and easily, leveraging the security protections of a reverse proxy - without the need to set up your own SSL certificate or open/map any inbound ports (an outbound connection to Cloudflare is required). An address will be created on your hostname - YourCompany.MyWorkDrive.net. In server settings, access the Cloud Web Connector settings section, enable the Cloud Web Connector, and enter your hostname on myworkdrive.net. Add an email for the server to notify when provisioning is complete. A tunnel will be created for you on Cloudflare. As noted above, your server must be able to make an outbound connection to Cloudflare's network via port 7844. It is not recommended to use outbound proxies or VPN with this connection.
In MyWorkDrive server 6.4 and later, there will be no file size limit. Previous versions will have an enforced file size limit (100 MB in versions 6.0 and earlier, 200 MB in versions 6.1 through 6.3).
Publishing with the Cloud Web Connector is a public endpoint; access is available to anyone on the internet.
Publish your own domain by adding an SSL certificate
To use your own hostname and remove the file size limit, set up your own direct connection to the MyWorkDrive server with your own SSL Certificate and open port 443 from your firewall.
Steps:
- Set up a hostname on your domain: e.g., share.mycompany.com
- Install and purchase an SSL certificate
- Bind the "WebClient" site in IIS to port 443
- Expose your site over port 443 through your firewall.
For security, we do not recommend opening up your site to port 80 (http) - See Require SSL setting.
For additional instructions, see our support guide on how to set up and install your own SSL certificate/hostname on your MyWorkDrive server.
Optimization Tip
We recommend using internal DNS to force any site traffic as local. For example, internally share.yourcompany.com should resolve to the internal IP address. This speeds up internal access and bypasses any firewall issues. This is standard practice for any internally hosted website - for example, Exchange, Outlook Web Access, and ADFS.
Security Tip
We recommend reviewing our guide on how to harden your IIS Server and disable unneeded IIS SSL Ciphers.
Read the SSL Lock Down Guide Here.
Publishing via your own hostname, using internal DNS, may be a private endpoint.
Standard Features & Settings
Office Online/Office Online Server File Editing
The MyWorkDrive server supports online editing of documents in the browser in Office online, ONLYOFFICE, and local Office online servers.
An Office 365 Business account is required to edit Office documents online (View does not require an Office 365 Business Account) using our default OneDrive option.
Enable or choose your Office Online Editing option using the settings tab in the MyWorkDrive server admin site on your MyWorkDrive server.
Webclient
Disabling the Web Client
Like all the clients, the web client may optionally be disabled. Note that this prevents Login and utilization of the web client by users, but some features hosted in conjunction with the web client, like login servicing and client APIs, will still be hosted by the web client. The web client is always enabled by default.
Setting Disabling Auto Load of First Share
By default, MyWorkDrive loads the first share in the web client when the user logs in. This is primarily to demonstrate the functionality of the web client. You may optionally turn this off, so no share is loaded at login.
Office Local Web Edit
When enabling this feature, users can choose to edit from the menu in the web browser client, and Office documents will open directly from the browser in local Office. For security, an additional security prompt will be presented. If DUO Two Factor Authentication is enabled, it will be requested as well. The administrator can optionally disable password saving for this additional pop-up, which means the user will be prompted for username and password every time a document is opened for edit from the browser in local Office. (default:enabled).
Office Double Click Action
This feature allows the administrator to control the action when an Office file is double-clicked in the web client – open online to edit, open online to view, open locally, or download (default:open online). Note that some options may not be present based on configuration.
Online Viewer Options
MyWorkDrive allows you to choose the viewer for Office documents. By default, MyWorkDrive uses the Office Web Apps viewer on Microsoft. If Microsoft’s public viewer is not available to you, or you wish to keep documents local for viewing, you may select the local viewer. The local viewer is used by default for most other file types. It typically performs slower than Microsoft’s public viewer and places a bit more load on your MyWorkDrive server.
Text Editor
Version 5.4.3 introduces a new inline light text editor option. This will allow users to edit .txt files in the web client, as well as other file types defined by the administrator – such as .log, .xml, etc.
The text editor can be enabled in Settings, and an entry area to specify the file extensions to permit editing will display when enabled.
Note that, when enabled, .txt files bypass DLP restrictions and can be edited with clipboard access.
Size Limits
A global site limit can be set, which limits the size of files users can interact with. Note that a separate limit may be applied to the mapped drive client.
File Lock Management
MyWorkDrive supports file locking/record locking. It will place and keep record locks for users of MyWorkDrive, and will also interoperate with SMB locking, respecting SMB locks on files from outside sources, and placing/releasing SMB locks.
MyWorkDrive will also permit co-editing in Office 365.
Open locks can be viewed from the File Locks menu item on the shares tab in the Server Admin.
Learn more about file locking in our file locking details article.
Data Leak Prevention(DLP):
Data Leak Prevention allows file shares to be configured in read-only mode, optionally by user or group. Data Leak Prevention works in web, mapped drive, and mobile clients.
Review the support article here for more information on DLP.
Data Loss/Leak Prevention requires an Enterprise or Partner License.
Branding, UI Customization, and Logo
Company Name
This can be set on the Settings page.
Default Language
For the web client, this can be set on the Settings page.
Enterprise licensees can customize the powered by, help page URL, background and toolbar colors, and user lock-out and password expired messages using the Branding section on the Enterprise tab.
For the logo, the maximum dimensions are 500x500px, and the accepted format is PNG.
A height of 75px to 100px tall fits best on mobile devices. The default MyWorkDrive logo is 325×75, for reference.
SAML SSO
SSO Setup is only available in Active Directory mode. With Entra ID, all logins use Microsoft native login.
ADFS integration allows users to access MyWorkDrive using ADFS for a Single Sign-On (SSO) experience without requiring re-entering of credentials.
See our ADFS Support Article.
Note: MyWorkDrive users can already sign in with their Active Directory accounts; ADFS or SAML adds additional integration options for enterprises.
MyWorkDrive supports SAML integration with easy integration for popular providers such as Microsoft Office 365/Azure AD, OKTA, and OneLogin.
See our SAML Support Article.
Optionally require users to access the MyWorkDrive web browser client using ADFS or SAML by enabling Require ADFS/SSO login in browsers. To enable logging out of ADFS or SAML when signing out of MyWorkDrive, you need to enable single logout.
Two Factor (Duo)
MyWorkDrive supports Duo Two Factor Authentication for enhanced security when customers are using Active Directory mode.
Configuration details are located in our Two Factor Authentication Support Article.
Multi-factor may also be managed as part of a “conditional access” policy in a SAML Provider. Two-factor is typically not enabled with SAML, and is not available with Entra ID and the native Microsoft Login. As of Version 7, MyWorkDrive is compatible with the new Duo Universal Prompt.
Sharing Features
Multiple methods can be enabled for MyWorkDrive users to share files, both internally and externally.
Public Link Sharing
MyWorkDrive provides the ability for administrator-approved users to generate links to files or folders from administrator-approved shares. Administrators control who can share, what shares they can share from, and what limits must be applied to the shared link.
Learn more in our Public Sharing Guide.
Public share links are public links and do not require a MyWorkDrive username to access them (passwords may be optionally required). This feature can be disabled from the Public Sharing tab in the Server Admin.
Azure AD B2B Guest User File/Folder Collaboration
Customers who utilize MyWorkDrive Azure AD integration for authentication can now easily invite external guest users to collaborate on Windows file shares. With this feature, external users are invited to Azure AD as guest users who can fully collaborate with internal users on files and folders without managing internal Active Directory accounts.
Review the setup article here for additional details.
This feature is disabled by default and requires setup before use. B2B guest is natively supported when using Entra ID for the user database.
Share Internally
MyWorkDrive users can share internal links with other MyWorkDrive users. The recipient must log in to MyWorkDrive with their user account to access the shared file or folder. They will only be able to view it if they have the appropriate permissions both within MyWorkDrive and on the underlying storage. This feature is enabled by default and does not have customizable settings.
Enable Outlook Sharing
This setting can be found in the Public Sharing menu. The 'Share via Outlook' feature, available in the web client, allows users to transfer files from storage directly into an Outlook message for easy email sharing. By disabling Outlook Sharing, users will not be able to share files externally using Outlook Online (default:enabled). The maximum attachment size can also be set – the default is 10 MB. If company policy requires MFA to authenticate users to Office 365, additional steps are required before enabling this feature.
See our Outlook Sharing Article.
This feature can be disabled from the Public Sharing tab in Server Admin.
Enable OneDrive Sharing
This setting is available in the Public Sharing menu. It is a connector between the web client and OneDrive via API that users may use to move files from storage to their OneDrive account and share via OneDrive. By disabling OneDrive sharing, users will not be able to share files externally using OneDrive (default:enabled). This feature can be disabled from the Public Sharing tab in the Server Admin.
Logs and Alerts
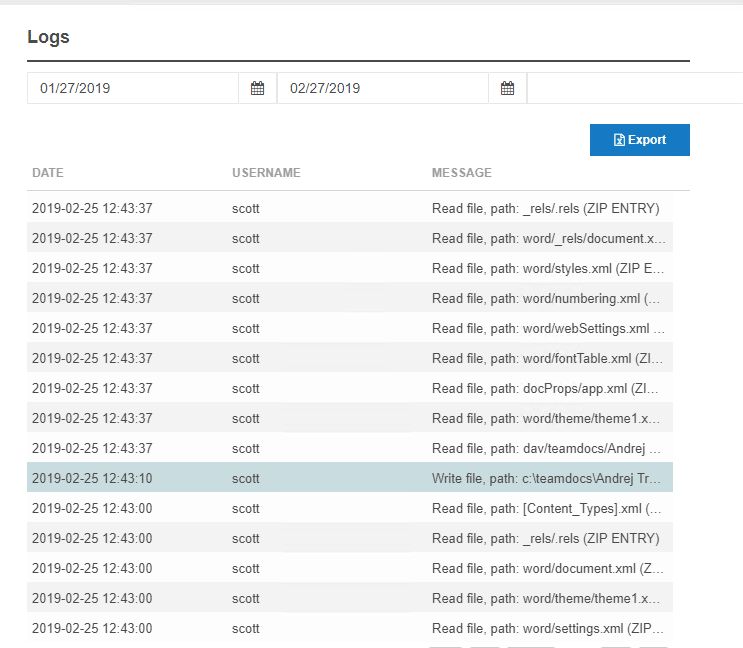
Logs
All user logins and file add/change/delete by users are recorded in the logs. By default, logs are retained for 30 days. The retention value can be adjusted on the Settings tab. Log files are stored as text files on the MyWorkDrive server. If you wish to copy the logs to cold storage for retention, contact MyWorkDrive support for location and guidance.
SysLog
MyWorkDrive logs can be forwarded to your SEIM via SysLog. This is a commonly used feature for customers who require long log retention or who want to integrate MyWorkDrive events in their existing monitoring and alert systems. Syslog Configuration Article.
Alerts
With MyWorkDrive server version 5.2, you are now able to configure alerts via email about user actions on the server – excess file downloads, deletes, etc. The settings are housed in a new menu item in the Server Admin titled Alerts.
Depending on the volume of activity at your organization, the alerts themselves, the count of events, and the timeframe are adjustable to match your organization. Enable the ones you need and set the count of events and timeframe as appropriate.
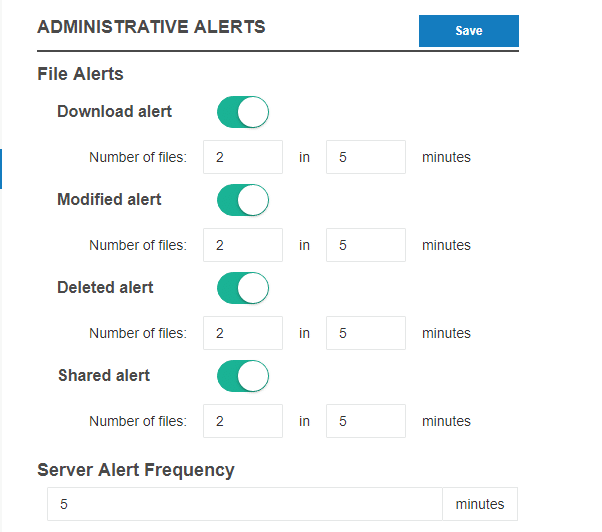
Note that you cannot have a Server Alert Frequency greater than the shortest minutes/activity interval. You also cannot set a frequency less than 5 minutes for any of the alerts.
The outbound email uses your SMTP settings.
You’ll receive an email notifying you that the threshold was exceeded.
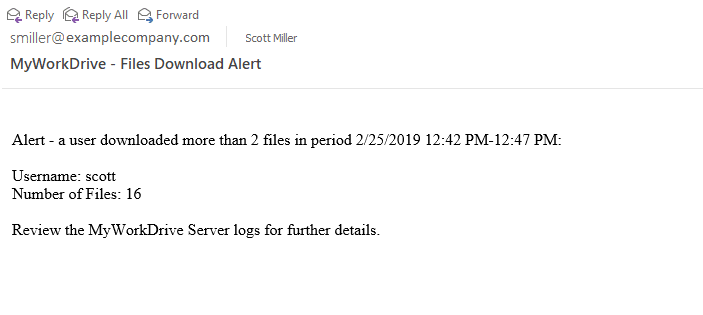
The details can be seen in the Logs menu item, including who took the action, what the action was, and what file(s) were impacted.
Device Approval
The Device Approval feature in MyWorkDrive permits administrators to limit access on the MyWorkDrive desktop and mobile clients to approved devices only. Device Approval is not available for web, web mobile, teams, or WebDAV (if enabled).
Implementation details can be found in our Device Approval Article.
Integrations
Integrations in the Server Admin show you all of the 3rd party connections you have made – for SSO, Office online, storage, etc. It provides the opportunity to view integrations that are not currently active, as well as set up and change connections.
Read more in our Integrations Article.
Clustering/Load Balancing
MyWorkDrive supports clustering multiple servers for failover and load balancing. See our support article for additional details. Clustering can be deployed for configuration files, sessions, and locks, or both. Note that clustering of configuration files currently requires SMB and is only available when using Active Directory for the user database.
Map Drive Client Management Features
The Mapped Drive Client Administrators Guide provides additional information about settings as well as deployment and configuration options, including scripted installation and launch commands with pre-set parameters.
Enable Mapper Client
By disabling this option, users will be unable to log in using the desktop mapped drive client (default:enabled). In addition, the administrator can restrict password saving or file types (requires version 5 of the mapped drive client).
Minimum versions
Set the Minimum Version of the client that is allowed to connect. This feature is often automatically set by MyWorkDrive as features are enabled, which require certain version levels. Users with clients below the Minimum Version will receive a notice their client must be upgraded before they will be able to log in.
Block/Allow List
The Block/Allow list is used to control what file types users are allowed to interact with. File types are set by file extension.
Replace Existing Network Drives
Replace Existing Network Drives determines whether MyWorkDrive should overwrite any currently mapped drive letters when shares are enabled. For example, if a user has drive Z: mapped to a network share, and Z: is also defined as a share in MyWorkDrive, the login process can replace it. This applies only to network drives; MyWorkDrive cannot replace local disks, such as SD cards
Password Saving
The password saving option controls whether a user should be locally allowed to save their password when using Active Directory mode with user/password login. When using native Microsoft login with Entra ID or a SAML SSO provider, this setting is managed by the identity provider.
Size Limits
A size limit can be set to limit how large a file users may interact with on the mapped drive client. Note there are separate settings for a global limit (all clients) and a map drive-specific limit.
Mobile Client Management Features
Enable Mobile Client
By disabling this option, users will be unable to log in using the desktop mobile client (default:enabled).
Password Saving
This setting notes where a user should be locally allowed to save their password when using Active Directory mode with user/password login. When using native Microsoft login with Entra ID or a SAML SSO provider, this setting is managed by the identity provider.
Minimum Version:
Set the Minimum Version of the client that is allowed to connect. This feature is often automatically set by MyWorkDrive as features are enabled, which require certain version levels. Users with clients below the Minimum Version will receive a notice that their client must be upgraded before they will be able to log in.
User Home Folders
User Home Folders are only available with Active Directory mode. By default, home drives are enabled and available to users when they log in. MyWorkDrive will display the UNC path as specified for that user in AD Users & Computers. The file server should be located ideally on the same LAN as the MyWorkDrive server (or on a very fast connection) and will need to be able to resolve the server by the hostname as entered in AD Users & Computers. Optionally, require users to have access to at least one MyWorkDrive share to restrict user logins to the MyWorkDrive server.
Windows Search
MyWorkDrive integrates with the Windows Search service. Due to Windows limitations, Windows Search integration is only appropriate for up to 2 TB maximum.
See our Windows File Server Search Guide.
For Enterprises with larger file server volumes or NAS devices, MyWorkDrive integrates with dTSearch.
See our dtSearch Setup Guide.
Search is only available with Active Directory mode, with Windows Search service for Windows file shares, and dTSearch for other SMB shares.
Import/Export
With MyWorkDrive server version 5.2, you are now able to export and import your MyWorkDrive settings. This makes it easier to save your settings, maintain a DR site, or migrate installations of MWD. At the bottom of the Settings section of the Server Admin, you will find buttons for Export and Import.
Export will create a zip settings file and initiate a download. The download will include your MyWorkDrive server configuration, user favorites, and SMTP configuration.
Import uses the zip file to configure your new server. To prevent license conflicts in Disaster Recovery or Clustering scenarios, certain unique settings—such as the Cloud Web Connector URL and license key—are not imported. You will need to provide your license key during setup.
Import also does not adjust any settings outside of the MyWorkDrive, such as the SSL settings of IIS, NTFS Permissions, NTFS Shares, Delegation, etc. Those settings will need to be made/adjusted as appropriate.
Health Dashboard
MyWorkDrive provides a central dashboard to monitor the status and history of critical components in the environment where MyWorkDrive is run.
Learn more in our Health Dashboard Article.
Additional Settings
Some settings may be unavailable due to configuration (which user director is selected or enabling an SSO provider).
Automatic Backup of Configuration and Error Reports
This allows your MyWorkDrive server to send configuration data to MyWorkDrive’s licensing server. This data is used for support purposes, to look up the configuration when replying to support requests. I can also be shared back with you if you need to recover your MyWorkDrive server. No user data, user logs, or user information is automatically backed up to MyWorkDrive. The only information is the server configuration data.
Previous Versions
MyWorkDrive connects to Windows Volume Shadow Copy Snapshots (VSS) services to enable previous versions restores from our web client.
Review the support article for Previous Versions.
This feature is only available when using Active Directory for the user database and with Windows file shares.
Enable WebDAV
By disabling this option user will be unable to use WebDAV with clients to log in to MyWorkDrive (note: disabling is recommended when Two Factor Authentication is used) (default:disabled). This feature is only available when using Active Directory for the user database.
Teams App
A MyWorkDrive teams app is available in the Teams store for servers using Active Directory identity. If you do not wish users to be able to use this app, disable it in Settings. This feature is only available when using Active Directory for the user database.
Enable Favorites
By enabling favorites, users will see a new option in the web file manager browser client to create and delete favorites for folder paths. By default, favorites are saved to the local MWD Server. In clustered environments, favorites may also be saved to a shared hidden share on the network (each MyWorkDrive server computer account will need NTFS permissions to create and modify favorites in this share).
Outbound Proxy
An outgoing proxy server may be specified for the MyWorkDrive server to communicate outbound to our licensing services in the format of http://hostname or IP Address and optional port number. For example, http://10.10.10.10 or http://10.10.10.10:8888.
Displaying Shortcuts as Folders
This feature returns shortcuts as folders when browsed by users in clients. If is feature is disabled, a shortcut is displayed, but it is blocked from use for security reasons.
Zip Size Limit
This permits you to limit the size of files a user may zip using the Zip feature in the web client. Zipping large files is resource-intensive, so you may wish to limit the size to prevent resource exhaustion on the MyWorkDrive server.
Email Domain Lookup
This is used in the mobile client to return the MyWorkDrive server when the user enters their email address in step one. It is a time-saving feature for users on mobile clients.
Session Timeout
In Settings, it is possible to edit the default settings for user session timeouts. As of version 5.4.1, user timeouts are absolute; in previous versions, they were idle timeouts.
When a timeout is reached, the user is prompted to log back in using the server’s configured login process – username, email, MFA, and SSO, etc. Any existing operations, such as document open, save, and copy, will complete prior to the login being required.
-
Private computers
- A user’s time logged in to the web client on a private computer (as marked on the login screen).
-
Public computers
- A user’s time logged in to the web client on a public computer (as marked on the login screen).
The default times are 8 hours for public computers and 5 days for private computers (these match Microsoft Office 365 defaults).
-
Mapped drive client
- A user’s time logged in to the PC and macOS Map Drive client.
-
Mobile client
- A user’s time logged in on the iOS or Android client.
-
Admin panel
- The administrator’s timeout session for the admin panel on the server desktop. Note that updating this will reset the existing login when changed.
-
Search query
- The timeout length of the search query when search is configured for the Web Client. A longer timeout will allow a query to consume server resources for a longer time, scanning a given directory. It may be desirable to keep a more modest timeout and encourage the users to search deeper in the directory tree.
-
Zip File Download
- The timeout length for the zipping process will run, preparing zip files in the web client. An increased timeout length will permit larger files or a larger count of files to be zipped, but will consume additional server resources. How many files or how large a file set may be will depend on environmental variables. It may be desirable to keep a modest timeout and encourage the users to create smaller zip files.
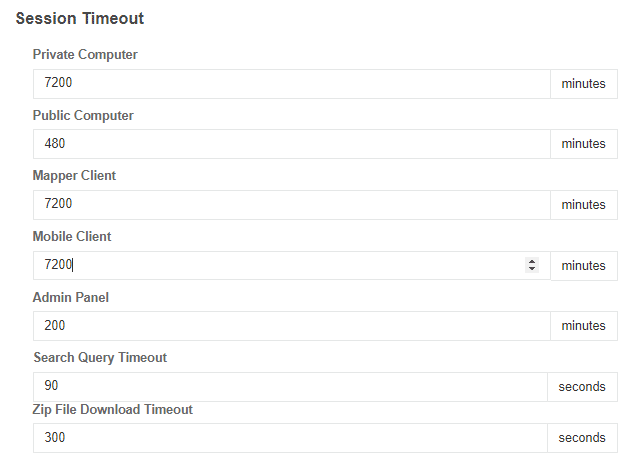
Adjust these timeouts to meet your company's security requirements. For additional security, enable Duo Two Factor Authentication.
Require SSL
Require SSL will automatically forward any port 80 requests to Port 443 (assuming both ports are bound to the web client site and published). Require SSL also sets cookie and session requirements for communications with other services such as Duo, Azure, and your SAML SSO Provider.
In some cases, you may be required to disable Require SSO based on your SAML SSO Setup. This setting is only available with Active Directory user mode. With Entra ID, all communications require SSL/TLS.
Require Email Username Format
Enabling this option will require users to log in using their email address. This is helpful in larger companies with multiple domains and also lessens the impact of entering a bad password lockout since only one username is checked (default:disabled). This setting is only available with Active Directory user mode without an SSL configured. SSO or Entra ID mode uses the IDP settings.
Domain Search Order
This is used to set the order Active Directory domains are searched when users enter a username on a server using Active Directory (not Entra ID) with user/password login (not SSO). When a user enters a name like “Samantha”, the MyWorkDrive server will test “Samantha” against all known domains until a login success is achieved. For example, domain1\samantha, domain2\samantha, domain3\samantha. You may choose to order the domains by clicking and dragging to cut down on login time, if you have certain domains that contain a majority of the active users (ie, you may have a test domain, or a second domain that is rarely used). Note that this feature is not used with Entra ID or SSO logins. It is also not relevant if the user specifies their domain as part of their login, either domain\username or user@domain. Enabling require email user format also eliminates the need to use this feature.
Backup MyWorkDrive Settings
The MyWorkDrive server files are located under c:\wanpath. Include this folder in any backup strategies to ensure MyWorkDrive settings can be restored in the event of a server failure. Note that no user data files are stored by MyWorkDrive – only settings, user favorites (version 5.2), and license information.
License conflict as a result of Cloning
A backup of c:\wanpath should only be used to restore an instance in case of recovery and cannot be used to migrate to a new server, create a disaster recovery standby, or create additional instances for clustering.
Attempting to use the files in c:\wanpath on multiple machines simultaneously will result in license conflicts, and attempting to restore to a different version of the MyWorkDrive server or new hardware is not recommended or supported.
Use the Import/Export feature to create a copy of the current settings to deploy on a new server.

