December MyWorkDrive Newsletter 2022
/in News/by MyWorkDrive TeamSecure your file sharing over HTTPS
In the wake of ransomware attacks and other threats, businesses, governments and schools are under the constant threat. Legacy remote access mechanisms such as VPN are no longer sufficient to protect files from encryption, theft, data leaks and ransomware.
Unfortunately, migrating files to cloud services as alternative has not proven to be the magic bullet for improving security and controlling costs. Cloud – like any other source of compute and storage resources – tends to sprawl, can be mismanaged and requires vendor lock-in by cloud sync and share vendors that store files in proprietary cloud storage.
The alternative, utilizing VPN software to connect to work resources, is that end users are creating an open tunnel between their home and corporate networks. This provides malware lateral access to numerous network ports across the network. Many companies are looking for a way to lock down their networks to prevent SMB file share access.
According to Gartner, by 2025, 70% of Enterprises will phase out most of their remote access VPN solutions in favor of Zero Trust Network Access (ZTNA).
This is where MyWorkDrive can help. MyWorkDrive provides secure remote access to files and file shares without having to use VPNs, manage SQL databases, or migrating files to proprietary cloud storage.
MyWorkDrive multiplexes control and data over a single https connection from client to server which is simple for firewalls to manage and scan for security vulnerabilities.
In addition to Zero Trust Security MyWorkDrive adds these additional Security Features:
- File Type Blocking
- File Size Limiting
- Two factor Authentication
- SAML/Single-Sign-On
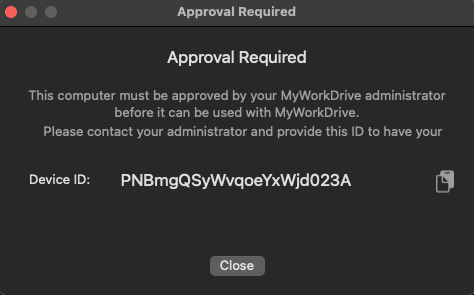
- Device Approval
- Data Leak Prevention view of files with download/copy/print restrictions.
- Alerting
MyWorkDrive Webinar and Demo
Register to join our resident experts on Thursday, December 8th, 2022 9:00 AM PST where we will demonstrate new features and enhancements in MyWorkDrive version 6.3 and a preview of features currently under development in 6.4.
- External Public Link Sharing
- OneDrive Storage Drive Mounting
- SharePoint Site Drive Mounting
Register using this link:
Can’t make that time? Register anyway and we’ll send you the recording.
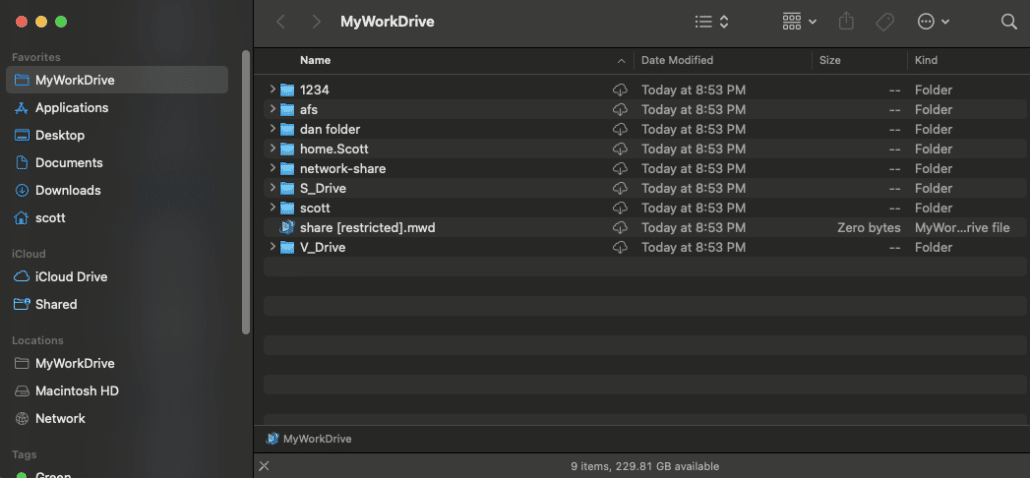
Map a network drive on macOS remotely using MyWorkDrive
Did you know MyWorkDrive has a native mapped network drive client for macOS?
macOS users can enjoy the same easy-to-use, full featured experience as Windows users with the MyWorkDrive mapped network drive client for macOS. Complete remote file share access natively in Finder without needing to install a complicated VPN, or being stuck using a web client while connecting over a secure https connection.
The MyWorkDrive macOS network drive client runs as an application on macOS and maps network drives on macs directly in Finder, as if the computer were locally on the network. Once installed, Users can browse/copy/drag/drop/edit/delete and create files on their available network shares as if they were in the office! Learn More & Download.
Map a network drive on macOS remotely using MyWorkDrive
/in blog/by MyWorkDrive TeamDid you know MyWorkDrive has a native mapped network drive client for macOS?
macOS users can enjoy the same easy-to-use, full featured experience as Windows users with the MyWorkDrive mapped network drive client for macOS. Complete remote file share access natively in Finder without needing to install a complicated VPN, or being stuck using a web client while connecting over a secure https connection.
The MyWorkDrive macOS network drive client runs as an application on macOS and maps network drives on macs directly in Finder, as if the computer were locally on the network. Once installed, Users can browse/copy/drag/drop/edit/delete and create files on their available network shares as if they were in the office!
Key Features include
- Simple installation
- No 3rd party drivers needed (Fuse)
- Native finder interface
- Map at Startup
- Support for SSO Login
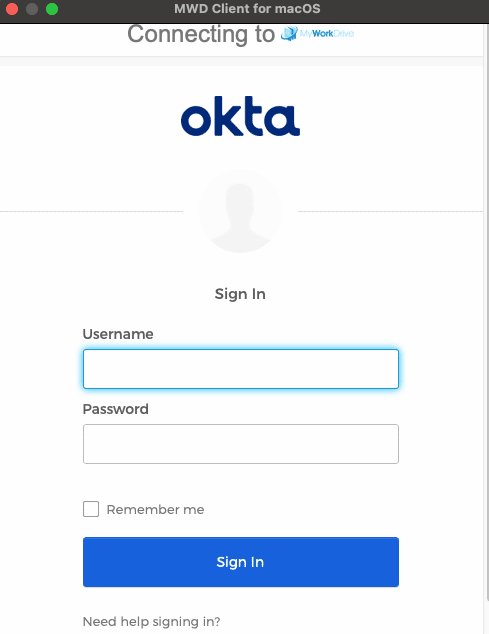
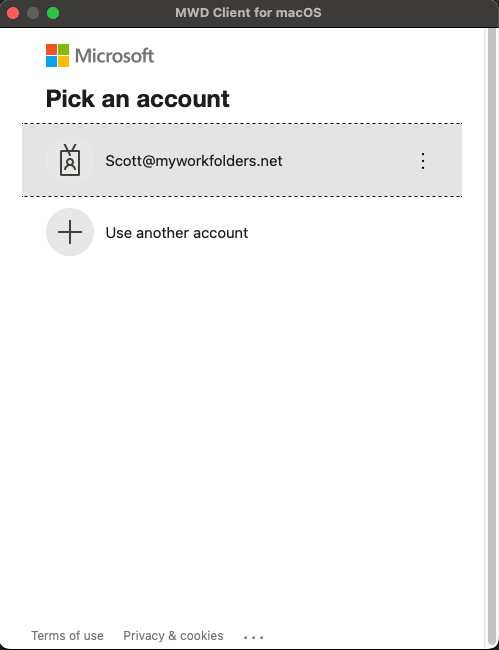
- Duo and Authenticator MultiFactor Authentication support



- Office Online Editing integration
- Bulk Uploader
- User activity logging
Along with all our security features like:
- Data leak protected shares
- File size limits
- File type limits
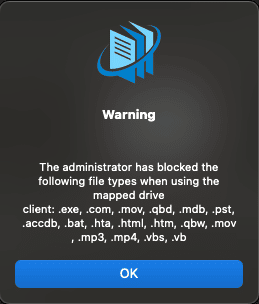
- Device Approval
- Timeout threshold
- And more.
Like our other clients, the macOS client is easy to install – users can download, install and map a network drive on macOS without an IT assistance. Administrators can push out an install from their favorite MDM to enrolled devices, and we support a configuration file for preconfiguring common settings (server url, map at startup, etc)
But what about the new Apple Silicon processors? Does it work with those?
We introduced support for the M1 processor before macBooks and Minis were officially released. We are Apple developers and were part of the Apple Silicon preview, ready to go from day 1.
While the macOS client works best on Big Sur 11.6 and later, we offer installers compatible with El Capitan and later. And with our limited function MWD Window, the client will work as far back as Mountain Lion
With the latest 6.3 release, the macOS client uses native macOS File Provider, and no longer requires 3rd party file system drivers like macFuse. Gone are the days of installing and maintaining a separate file system driver, or the complication of the recovery mode and kernel driver enabling the M1 processors introduced. 6.3 and later macOS clients don’t require any of that, simply install and go to work!
Ok, but does it really work?
We built the map network drive for macOS client knowing we needed a fast, stable, reliable File Share Remote Access solution for our team. We have a liberal work-from-home policy, with staff from every discipline regularly working remotely.
The client wasn’t written by Windows developers who don’t understand macOS, or some 3rd party who doesn’t even use the software. We’re Apple developers. Our macOS and iOS clients are made by developers on our team, who work in and on Apple products. But it doesn’t stop there, we have macOS users throughout the organization, from QA/Support to the executive leadership team.
Limitations like maximum file size, compatibility with select file types, poor performance, or poor reliability simply wouldn’t work for us. Our team needs fast, reliable, collaborative access to Office documents and spreadsheets, Marketing Presentations, PDFs, Images, etc, in order to be able to conduct business. Just like our customers.
If you’re already a MyWorkDrive customer, your macOS users can get started today by downloading the client from our clients page. and mapping network drives on their mac.
If you’re not yet a MyWorkDrive customer and want to try out MyWorkDrive for your macOS users, you can get started with a 15 day free trial on a VM on prem, or in the cloud with our images in the Azure or AWS image stores (its free!)
For questions about the macOS client, reach out to us on our help desk or email support@myworkdrive.com
Join MyWorkDrive at The Western Australian Technical Support in Schools Association (WATSSA)
/in News/by MyWorkDrive TeamWe are excited to be a sponsor of the The West Australian Technical Support in Schools Association (WATSSA) ICT in Education Conference being held on November 23rd and 24th. This event will consist of Technical, ICT Leadership discussions and will feature software solution sponsors. MyWorkDrive will be presenting our solution along with other presenters on topics such as Software Development, Wireless and Networking, Remote Access and Office 365
Join our team in person at this important event at Crown Perth, Great Eastern Hwy, Burswood WA 6100, Australia. We are excited to sponsor a powerful series of sessions that provide inspiration, participation, education, and thought-provocation in education technology!

We look forward to showcasing our MyWorkDrive file share remote access software in use by educational institutions worldwide.
CIO Review Magazine Awards MyWorkDrive Most Promising Compliance Technology Solution Provider
/in News/by MyWorkDrive TeamWhat is Remote Work?
/in blog, Remote Work/by Dan GordonRemote Work Trends With the increase in remote work where people and businesses need to work remotely, how do they do it? Remote employees work either from home or outside of the traditional working environment, such as at an office or on a specific job site. It increases morale and encourages successful completion of tasks […]
Join MyWorkDrive at Bay Area Government Digital Summit
/in News/by MyWorkDrive TeamWe are excited to be a sponsor of the Bay Area Government Digital Summit by Govtech on Aug 25, 2022. Join our team in person at this important event on Government Technology’s passion in promoting best practices and spurring innovation in the public sector – more important than ever in challenging times like these. We are excited to sponsor a powerful series of sessions that provide inspiration, participation, education, and thought-provocation in government technology!

We look forward to showcasing our MyWorkDrive file share remote access software in use by governments worldwide.
August MyWorkDrive Newsletter 2022
/in News/by MyWorkDrive TeamWith Summer shifting into August vacations, it’s a great time to review Software and Server upgrades and take a look at some of the training videos that we have may have been putting off. We assembled resources that we hope you find valuable as you prepare for the busy fall season and that you can share with your users to empower them during their summer travels.
Have members of the IT Admin team that could use a walk through of MyWorkDrive? Been a while since you’ve set it up and want a refresher or personal demo of new features? Book a time & we’ll be happy to answer questions or provide an overview with one of our engineers.
Kind Regards,
MyWorkDrive Team
Server Setup & Optimization
A complete Server Setup guide and latest Video is here: Server Configuration Guide.
Quickly update your MyWorkDrive server to the latest version at any time (Upgrades are free!), our guide steps you through the process.
Deploying and Upgrading installed clients is easy with our scripted deployment options.
Most Popular Features
Edit and Collaborate in Office Online while keeping files local article and video clip.
Device Approval (newest feature since version 6.2)
Native Single Sign On. Setup and learn about Single Sign On options with ADFS or SAML providers.
User Video Resources to Share
Web File Manager: short demo video on how to use MyWorkDrive in the browser
Client Demo: watch here how to access MyWorkDrive from the Windows Client
Mac OS: how to use the native Client for MyWorkDrive on Mac systems
Mobile: Short presentation of the mobile app User Interface
July MyWorkDrive Newsletter 2022
/in News/by MyWorkDrive TeamCloud File Storage
With the shift to hybrid work schedules, we are seeing a lot of customers looking to migrate file shares to cloud based storage. Unfortunately cloud storage providers have one goal in mind – to lock the customer into proprietary file systems – you can check files in but checking them out is a complex and costly endeavor. Unlike standards-based internet protocols; Cloud File Storage is proprietary and has no open database standard.
MyWorkDrive was founded around the core value that organizations should have the option to retain ownership and control of their files, whether they are stored online or locally, in standard NTFS file formats. We believe organizations should not be forced to migrate, convert or store them in proprietary cloud storage file formats requiring vendor lock-in just to experience the benefits of secure online collaboration and file sharing.
While Small Business might be just fine with Cloud Storage/Sync N Share vendors, Larger Enterprises, Governments, Education and Health Care providers are rightfully concerned about security, data sovereignty and vendor lock-in.
MyWorkDrive’s secure remote access to cloud file storage utilizes standards-based SMB file shares for its storage. This is made possible by our server software, which provides a secure tunnel for access to local and cloud storage remotely and in Office Online while continuously saving any changes back to the customers own new or existing file shares. Customers can store files on any SMB File Share including our vendor partners – Azure File Shares, AWS FSX, MorroData, NetApp or Nasuni – while retaining control and flexibility.

Coming soon in version 6.3
The team at MyWorkDrive is working hard to complete our latest new features and updates. We expect version 6.3 to be release to preview by mid-July. Features include:
Native file system driver for the macOS Client
We are working on comprehensive rewrite of the macOS mapped drive client that utilizes macOS file provider instead of the 3rd party Fuse file system driver. File provider installation will remove the requirement for Fuse and the need to use recovery mode during setup on Apple Silicon (M1/M2) based macs.
Health Dashboard
Our new health dashboard will provide feedback on critical services, memory and server readiness with repair recommendations and automated fix tools.
Delegated Guest User Sharing
With this enhancement we will provide the ability to delegate management and creation of external guest user invitations on guest shares from the Web Browser Client to non-it staff.
Publishing Logs to Syslog servers
Our log files have always been published to be machine readable, and many clients have used log aggregators to pull the logfiles into their SEIM, but with 6.3 we’re making it easier by publishing the logs using standard protocols via TCP or UDP.
Clustering of Office Locks
Enterprises running MyWorkDrive in clusters will have the option of allowing coediting of Office files across multiple MyWorkDrive Servers.
Sessions Management
Enhanced management of user sessions with reporting and termination options.
June MyWorkDrive Newsletter 2022
/in News/by MyWorkDrive TeamSecure File Share Remote Access
With the shift to full time “Work from home” strategies leading employees to work from home, public coffee shops and insecure tourist destinations, the need for secure mapped network drive access to Windows File Shares has increased ten fold.
Where IT used to provide remote access as a convenience to a few executives while traveling, or key staff while on vacation – its now become a huge burden for staff to manage corporate PC’s remotely, secure internal networks and train users on how to use VPN.
MyWorkDrive alleviates these security and support concerns with our flexible client options that mean options like no remote installs, allowing users to Map Network Drives, and even working from their phone.
 The MyWorkDrive map network drive client allows employees to have the same user experience that they previously only had when working in the office or connecting from to VPN from a Corporate PC. With local drive letters that natively present files and folders in Windows explorer and operate as if the data was all on the workstation, users can drag and drop, double click to open, or save as to a MyWorkDrive share. Files are securely stored on company file share, without the worry about files being out of sync or orphaned on remote machines.
The MyWorkDrive map network drive client allows employees to have the same user experience that they previously only had when working in the office or connecting from to VPN from a Corporate PC. With local drive letters that natively present files and folders in Windows explorer and operate as if the data was all on the workstation, users can drag and drop, double click to open, or save as to a MyWorkDrive share. Files are securely stored on company file share, without the worry about files being out of sync or orphaned on remote machines.
In addition to alleviating the IT help desk from supporting VPN and end user PC’s, the MyWorkDrive map network drive client improves security – Only port 443/HTTPS is opened to your MyWorkDrive Server with no direct VPN or lateral access to your internal network or file shares. Additionally, you can layer on additional security features and compliance enhancements including:
Device Approval
In MyWorkDrive 6.2, we introduced device approval where administrators can control what devices are allowed to connect to MyWorkDrive Servers. Features include the ability to monitor usage, last login, and operating system details for all connecting clients.
Data Leak Prevention
Prevent data theft, loss of company data and ensure compliance – while still allowing viewing and editing of files and shares online. Now with added support in mapped drive clients and mobile clients.
All user file sharing access is secure, logged and searchable with watermarking and time stamps. File shares can also be locked down to prevent clipboard copying or printing within our encrypted viewer.
Alerting
Administrators can configure MyWorkDrive to provide alerts on suspicious activity. Get alerts on questionable activity like users uploading or downloading large numbers of files unnecessarily, malware acting on shares, or misconfigured backup/sync products.
Coming soon in version 6.3
The team at MyWorkDrive is looking forward to our latest new features to be released to 6.3 preview soon including:
Native file system driver for the macOS Client
We are working on comprehensive rewrite of the macOS mapped drive client that utilizes macOS file provider instead of the 3rd party Fuse file system driver. File provider installation will remove the requirement for Fuse and the need to use recovery mode during setup on Apple Silicon (M1/M2) based macs.
Health Dashboard
Our new health dashboard will provide feedback on critical services, memory and server readiness with repair recommendations and automated fix tools.
Delegated Guest User Sharing
With this enhancement we will provide the ability to delegate management and creation of external guest user invitations on guest shares from the Web Browser Client to non-it staff.
Publishing Logs to Syslog servers
Our log files have always been published to be machine readable, and many clients have used log aggregators to pull the logfiles into their SEIM, but with 6.3 we’re making it easier by publishing the logs using standard protocols via TCP or UDP.
Clustering of Office Locks
Enhanced management of user sessions and file locks will permit Enterprises running MyWorkDrive in clusters to enable coediting of Office files across multiple MyWorkDrive Servers.
MyWorkDrive & Morro Data – NAS In-Cloud and On-Prem
/in News/by MyWorkDrive TeamMyWorkDrive and Morro Data announce that they will collaborate to provide businesses with the most complete Cloud NAS solutions for the hybrid workplace. Users anywhere can now securely access the complete file system at up to Gigabit speed.
With MyWorkDrive & Morro Data, it’s easy to Migrate File Servers to the Cloud without managing complex file share migrations, retraining users, or giving up local access.
With a typical “cloud only” type file service, file shares must be converted and locked-in to the cloud storage vendor requiring a complex migration, retraining of users, sync client deployment, and hefty monthly per user fees. These services also do not allow for fast local access when needed to support power users or designers who need local network speeds to work efficiently.
With MyWorkDrive and Morro Data, these problems are solved. Simply sync file shares to the Morro Data Cloud and connect to them using a MyWorkDrive Server for easy remote access without VPN. Power users and designers anywhere who need to access larger files or collaborate on design files with file locking can connect to a local CloudNAS CacheDrive appliance.
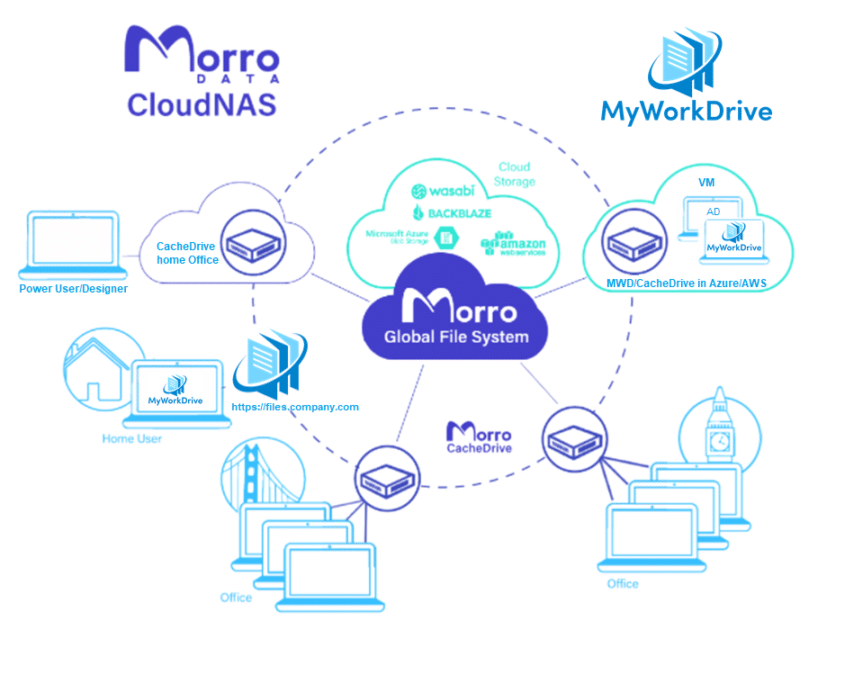
The Best of Both Worlds
When used together, MyWorkDrive and Morro Data provide 100% remote accessibility of files from any Web Browser, Mobile, Mapped Drive or local NAS with Gigabit performance.
MyWorkDrive & Morro Data combined Cloud File Server Benefits:
- Keep the same mapped drives with no training needed
- Simple, automated Migration
- No Servers to maintain on-premises
- Unlimited Capacity
- Reduce cost compared to cloud only services
- Maintain Data Privacy, Control of files and storage location
- Access files at Gigabit Speed with CacheDrive gateways
MyWorkDrive & Morro Data – For a complete solution to all your File Share Remote Access needs!



