Harden IIS SSL for Compliance and Security
IIS SSL by default leaves older versions of SSL2, SSL3 and TLS enabled for compatibility. MyWorkDrive has been engineered to support TLS 1.2. Disabling insecure and weak ciphers is necessary to comply with security best practices including PCI, HIPAA, FINRA and GDPR.
While registry entries can be set manually, a great free tool exists for this called IIS Crypto by Nartac Software.
To lock down your Server’s IIS SSL ciphers, download the tool and apply one of the templates – at a minimum we suggest the “Best Practices Template”.
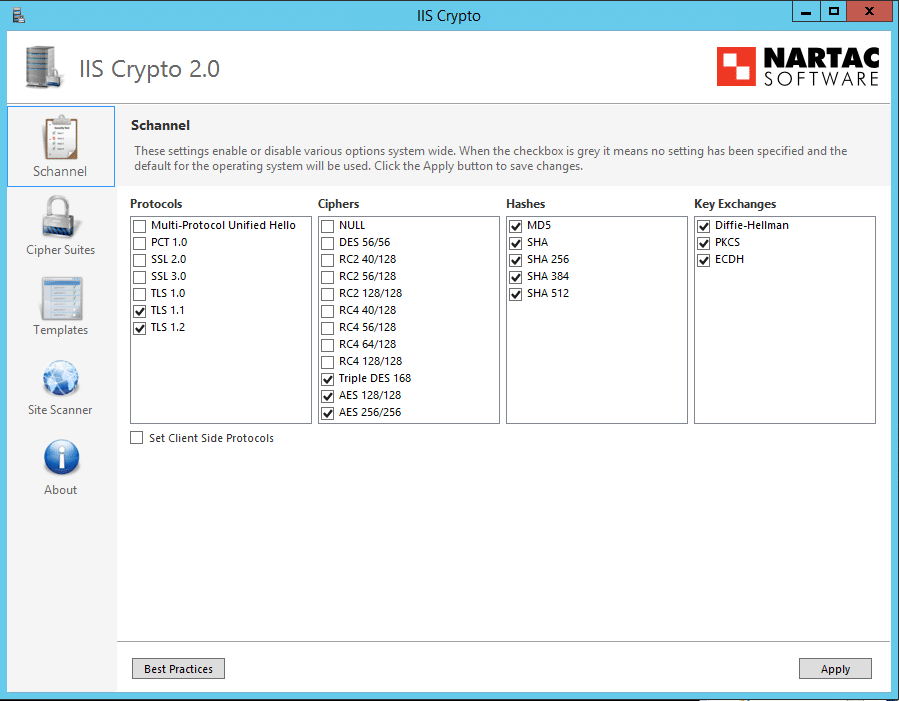
The PCI Template 3.1 provides the most complete protection however some software may still require TLS 1.0 communication (MyWorkDrive does not). One option is to apply the template settings to the Server only by unchecking “Set Client Side Protocols”. This ensures only the “Server” portions are locked down and any client software ( e.g. Backup Software) continues to run.
After you have run the IIS Crypto tool and applied a minimum of the best practice template and restarted your server, you may wish to verify that your server responds on only the more secure IIS SSL cyphers.
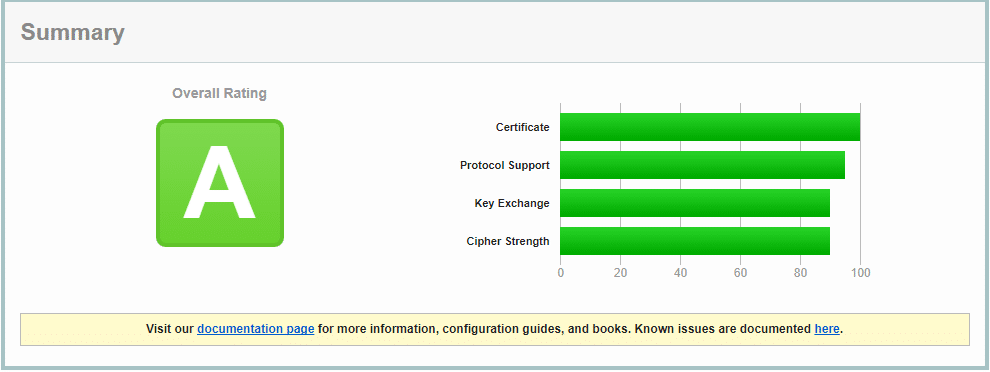
There is great free SSL scanning tool at https://www.ssllabs.com/ssltest/ that’s also built into the Nartac IIS Cryptol software that gives you a rating on how secure your SSL connections are. Simply input your https web address and run the test.
You should get a Summary like this: