Azure AD/Entra ID for MyWorkDrive Setup Guide
MyWorkDrive 7 Server Version or Higher Required:
The MyWorkDrive server supports native Entra ID (formerly Azure AD) for user authentication as an alternative to Active Directory. Authentication works by utilizing an Entra ID App Registration with permissions to view users and groups in Active Directory.
There are three options for the Entra ID App Registration with MyWorkDrive.
-
Option 1
-
MyWorkDrive server may be configured to trust and use our shared MyWorkDrive Auth app registration. This uses an App Registration hosted by MyWorkDrive and requires you to permit cross tenant apps in your tenant.
-
Or, use a custom tenant-only app registration in your Azure tenant. There are two options to set up a tenant-only app registration.
-
-
Option 2
- Use the setup wizard to create a custom Azure App Registration in your tenant. This will create an Azure App Registration in your tenant that your MyWorkDrive server will use. It does not use a hosted app like Option 1.
-
Option 3
- Manually create your own app in your Azure tenant for your MyWorkDrive server to use. This produces the same outcome as Option 2, an app in your own tenant (nothing cross tenant), it is simply done manually.
Our server post-setup wizard allows you to choose your preferred option.
Ensure that you plan to publish MyWorkDrive using your own hostname, and that the hostname is fully configured before proceeding with the setup wizard.
If you are not prepared to configure your own hostname, you can use our built-in Cloud Web Connector to publish your server. You can always move to your own hostname later. See Publishing your MyWorkDrive Server for additional options and details.
API Permissions
The permissions recommended for your app in Azure, in the chart below, support the common functions MyWorkDrive accesses in Azure.
-Entra ID Identity for Authentication
-Data Storage for OneDrive/SharePoint
-Office Online Editing with Office 365 and OneDrive/SharePoint for Temporary Storage
-Azure Storage (Azure File Shares, Azure Blob)
They are what is used in the MyWorkDrive managed App, what is set up in the automated setup option, and what we recommend you set up if choosing the manual setup option.
| API | Permission | Type | Description |
|---|---|---|---|
| Azure Storage | |||
| user_impersonation | Delegated | Access Azure Storage | |
| Microsoft Graph | |||
| Delegated | View users' email address | ||
| Files.ReadWrite | Delegated | Have full access to user files | |
| Files.ReadWrite.All | Delegated | Have full access to all files user can access | |
| Group.Read.All | Application | Read all groups | |
| GroupMember.Read.All | Application | Read all group memberships | |
| GroupMember.Read.All | Delegated | Read group memberships | |
| offline_access | Delegated | Maintain access to data you have given it access to | |
| openid | Delegated | Sign users in | |
| profile | Delegated | View users' basic profile | |
| Sites.Read.All | Delegated | Read items in all site collections | |
| User.Read | Delegated | Sign in and read user profile | |
| User.Read.All | Application | Read all users' full profiles | |
| SharePoint | |||
| MyFiles.Write | Delegated | Read and write user files |
Reply URIs
Several reply URIs are required for the proper functioning of your app registration. If you use the wizard to create an app in your tenant (Option 2) or choose to manually create your own app (Option 3), please make sure these 5 URIs are present on the authentication page of your app. The base domain of the URI will be the public URL of your MyWorkDrive server.
| URI | Usage |
|---|---|
| https://your-server.example.com/ | Logins from the home page |
| https://your-server.example.com/GraphApiTokenPage.aspx | Logins generated dynamically by the application for token renewals, access to storage |
| https://your-server.example.com/OfOnShPo/Home/SignInRedirect | Logins used in the Web client or when editing with office online |
| https://www.myworkdrive.com/success-azure-app-registration-approval | Approval URL for Adding and modifying Entra ID / Graph API access configuration in MyWorkDrive server admin. |
Option 1: MyWorkDrive Auth App Registration
When utilizing the MyWorkDrive Cloudflare Web Connector (*.myworkdrive.net web address), the MyWorkDrive managed app registration will be presented as an option.
With this option, you will be prompted by the wizard to sign in as an Azure AD/Entra ID Global admin account.
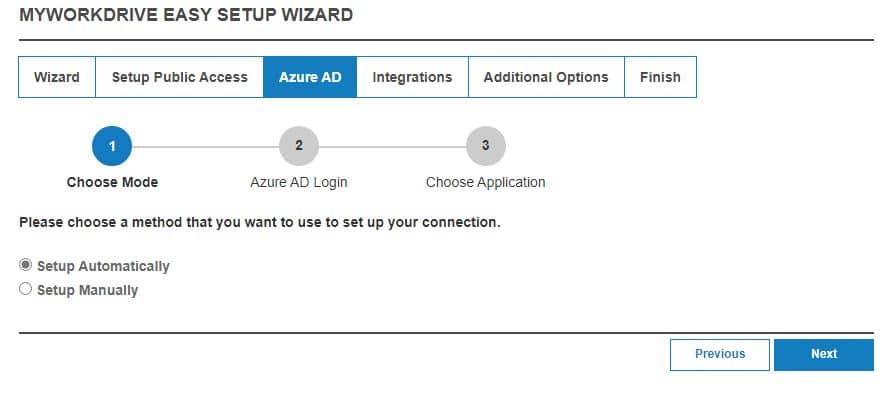
In the next step, log in with an Azure AD Global Admin to continue automated setup.
To sign in, follow the prompts to sign in using the Microsoft device login method and enter the code (you may copy the code to the clipboard for ease of entry) as presented during setup.
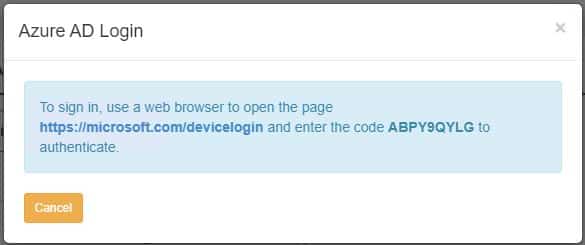
Authenticate with your Azure AD/Entra ID Global admin account when prompted, then click continue to sign in to the Microsoft Azure CLI and close the page when requested to continue to the next step.

After a few moments, the MyWorkDrive admin panel will recognize that you are logged in with an Azure AD Global Admin:
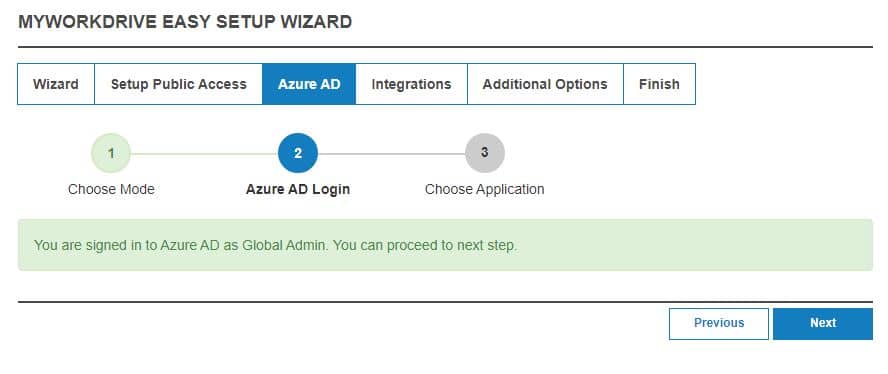
You with then be provided with the option of using the MyWorkDrive hosted Azure AD App.
Leaving that option selected, approve the MyWorkDrive hosted app registration.
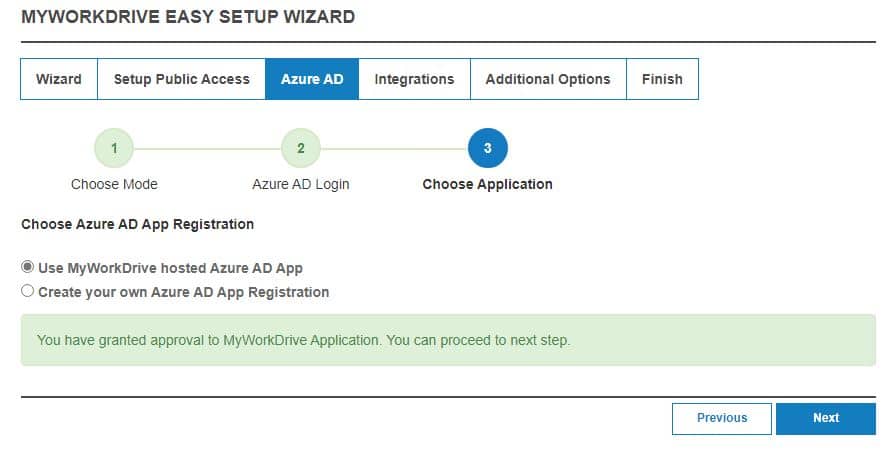
Option 2: Custom Azure App Registration (Automated Setup)
With this option, you will be prompted by the wizard to sign in as an Azure AD/Entra ID Global Admin account.
You will be approving the "MyWorkDrive App" Azure AD, which has Microsoft Graph API permission to create/read/write Azure AD Apps on your behalf.
Note: The temporary "MyWorkDrive App" may be removed from Entra AD once setup is complete (Located in Entra ID Enterprise Applications).
Begin by following the wizard to log in to Azure AD and set it up automatically.

In the next step, log in with an Azure AD Global Admin to continue automated setup.
To sign in, follow the prompts to sign in using the Microsoft device login method and enter the code (you may copy the code to the clipboard for ease of entry) as presented during setup:

Authenticate with your Azure AD/Entra ID Global Admin account when prompted, then click continue to sign in to the Microsoft Azure CLI and close the page when requested to continue to the next step:


After a few moments, the MyWorkDrive admin panel will recognize that you are logged in with an Azure AD Global Admin.

You with then be provided with the option of creating your own Azure AD app.
Deselect the Office 365 and Azure Storage options (not shown in this image) if you do not intend to use those features. If you select those features but they are not available in your tenant, or you do not have permission to grant consent for them, you may not be able to complete the wizard.
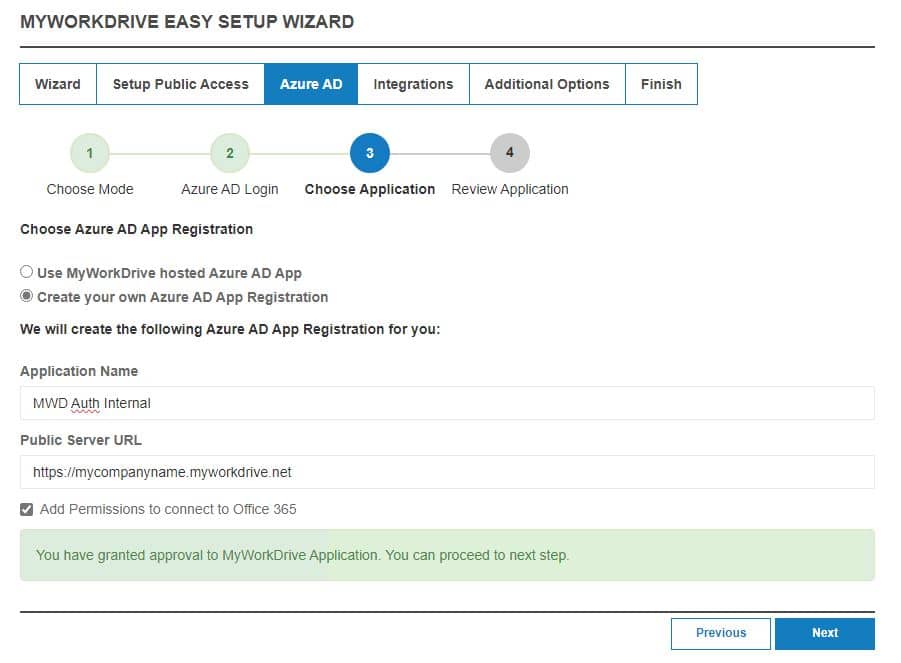
Leaving that option selected, once created, back up, then approve the MyWorkDrive hosted app registration that we created for you in your tenant.
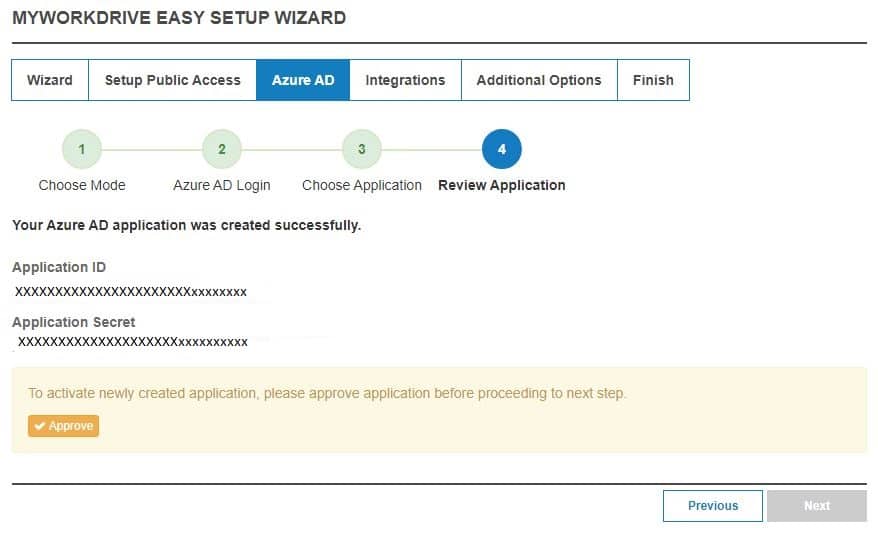
Make note of the Application ID and securely store your Application Secret for future reference.
Option 3: Custom Azure App Registration (manual setup)
Your organization will need its Azure AD Global Admin to create an Azure AD App Registration with the necessary permissions noted at the beginning of this article.
Create a new Azure AD App Registration in the same Azure AD as your user’s Office 365 Subscription.
On portal.azure.com, log in using the Global Admin Account. Bring up Azure Active Directory/Entra ID https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade, then click App Registrations.
Create New Registration
Provide a Name, Selected Account Types, and insert your public MyWorkDrive URL.
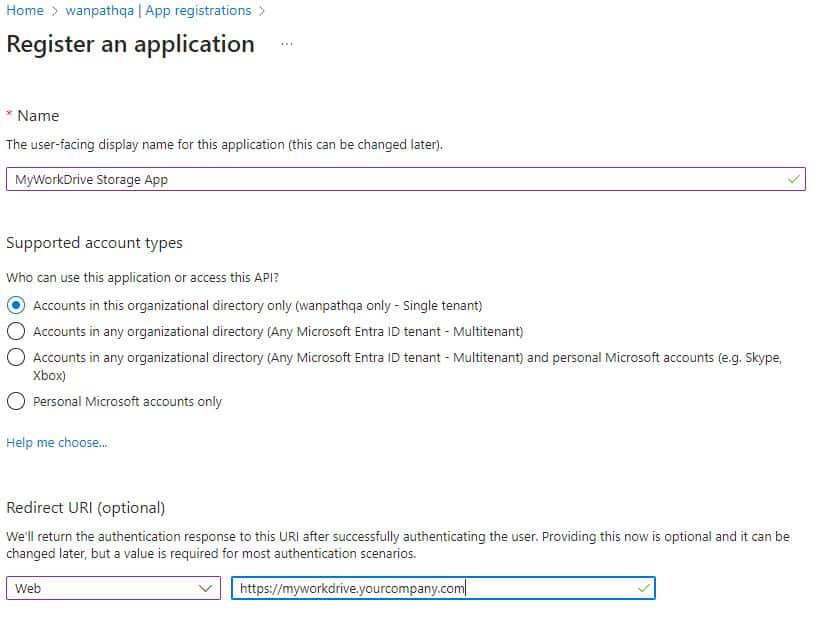
Click Register
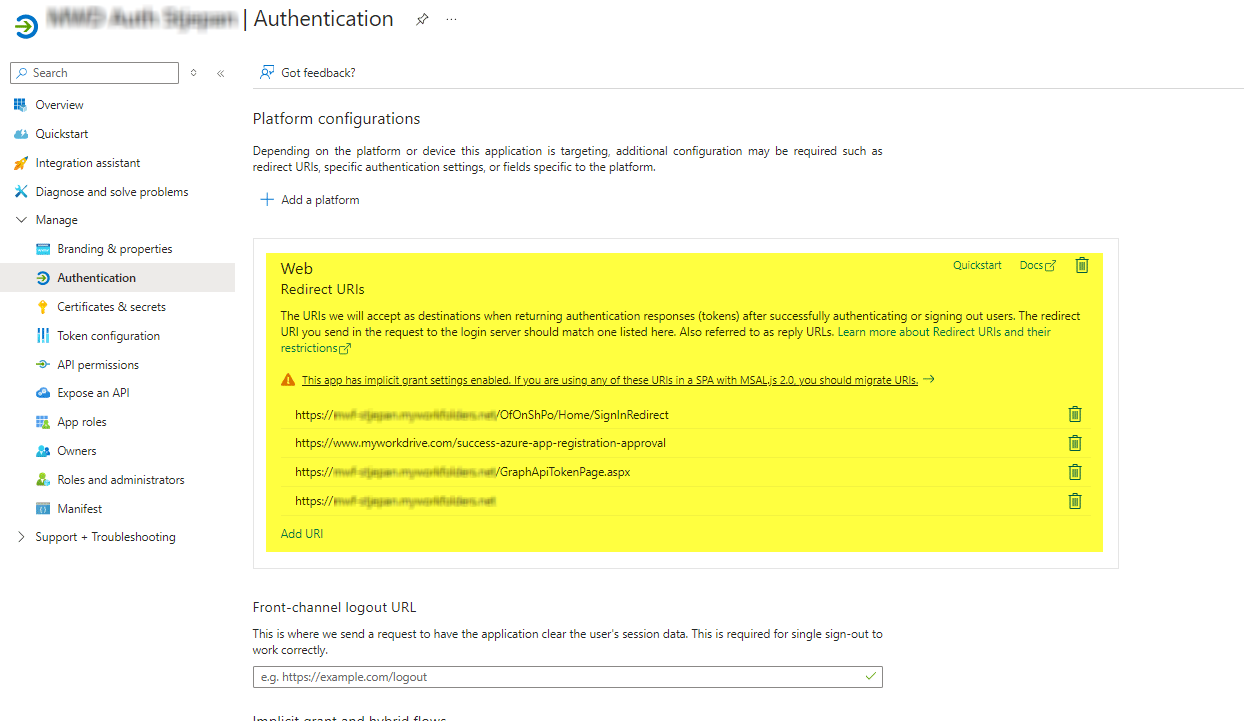
Web Redirect URIs
Set the four Web Redirect URIs, as described in the section above, on the Manage | Authentication page of your new app.
https://your-server.example.com/OfOnShPo/Home/SignInRedirect
https://your-server.example.com/GraphApiTokenPage.aspx
https://your-server.example.com/
https://www.myworkdrive.com/success-azure-app-registration-approval
API Permissions
Click API permissions.
If you are using all the features of MyWorkDrive, add the permission below.
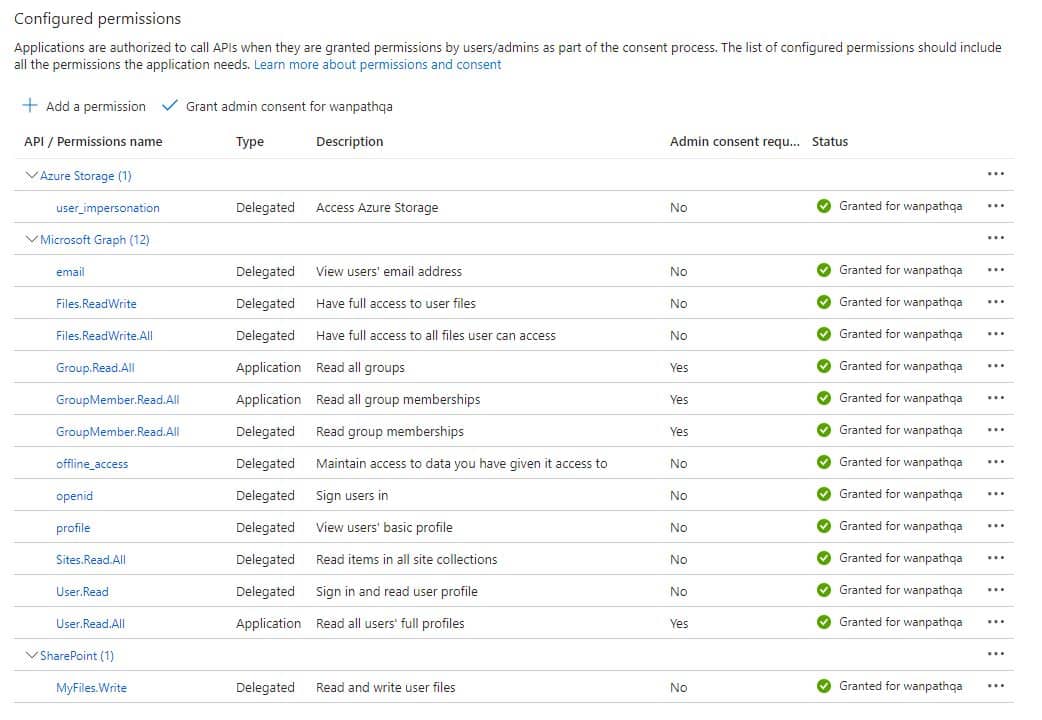
You may omit Azure Storage |user_impersonation if you do not intend to use Azure Storage with EID Auth, and will either not be using Azure Storage, or will be using it with Connection String.
You may omit SharePoint | MyFiles.Write if you will not be using Office 365 Online editing.
If you only want to use MyWorkDrive for identity purposes, without any additional features in Azure (such as SharePoint/OneDrive storage, Office Online editing, or Azure Storage), then only these five permissions are needed.
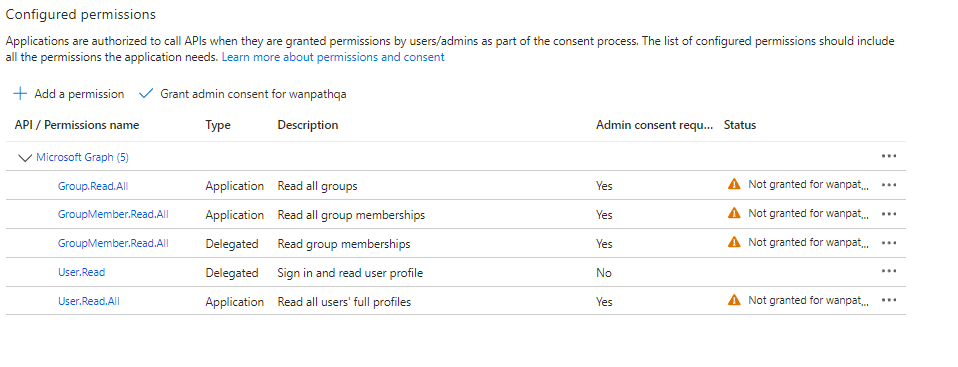
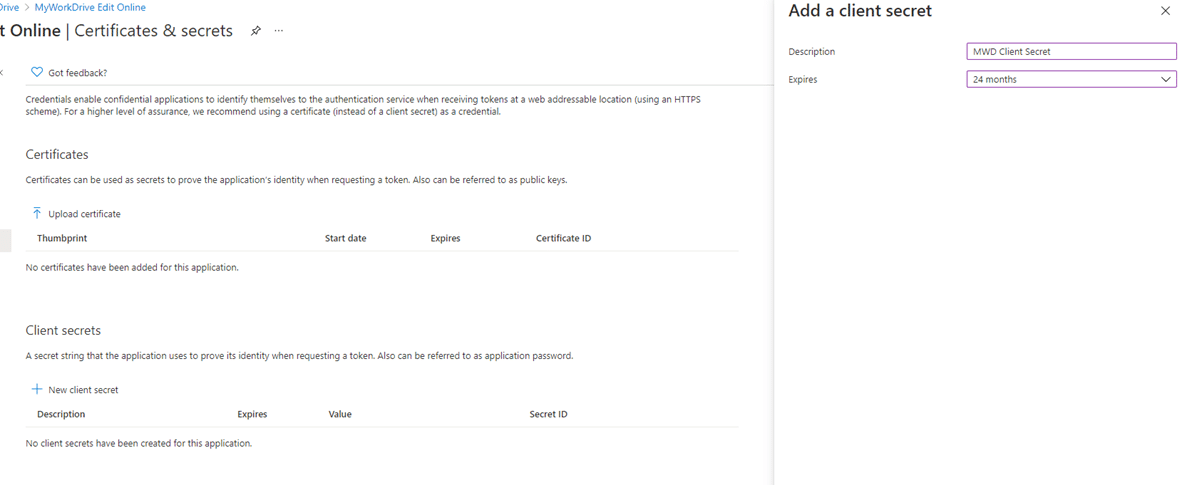
Go to: Create Client Secret > Certificates & Secrets > New client secret
Take note of the Calendar Secret Expiration Date, as it will need to be regenerated at that time and updated on all MyWorkDrive Servers.
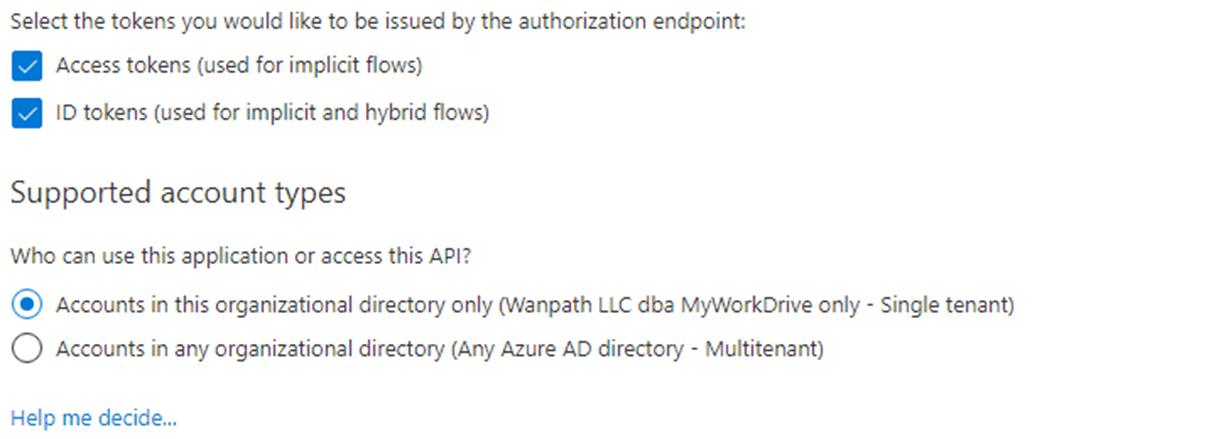
Click Authentication and enable Access Tokens and ID tokens.
Copy the Client Secret Value (not the secret ID). Keep this backed up and secured, as it will only display briefly.
Click Overview: Copy the Application (client) ID. Retain this value for use in the MyWorkDrive admin panel.
Copy the Directory (tenant) ID. Retain this value for use in the MyWorkDrive admin panel.
Note the Client Secret Expiration – this will need to be renewed before it expires and updated on each MyWorkDrive Server in the future.
Update branding on your custom Azure AD App Registration to verify the app or add a company logo as desired.
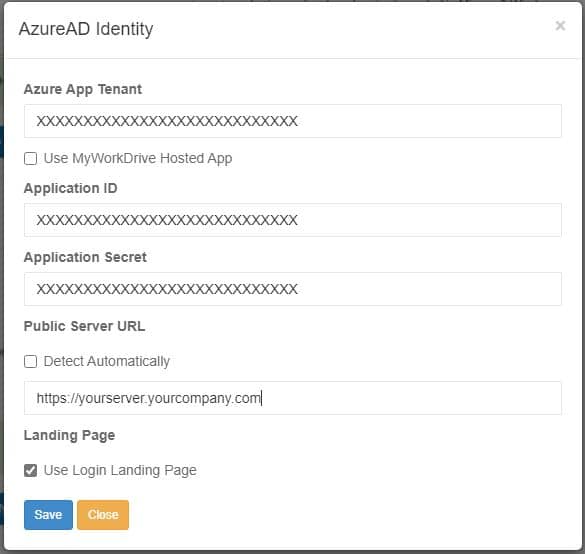
MyWorkDrive Server Configuration
Under Integrations or during the wizard when prompted, paste the values of your Tenant ID, Application ID, Application Secret, and your Server URL into Azure AD Integration.