The instructions in this article are only applicable to MyWorkDrive installations using Active Directory for user identity. SAML SSO configuration is only required/supported when using Active Directory. Entra ID Installations use a native Microsoft login.
MyWorkDrive with Entra ID
Note: Entra ID is formerly known as Azure AD.
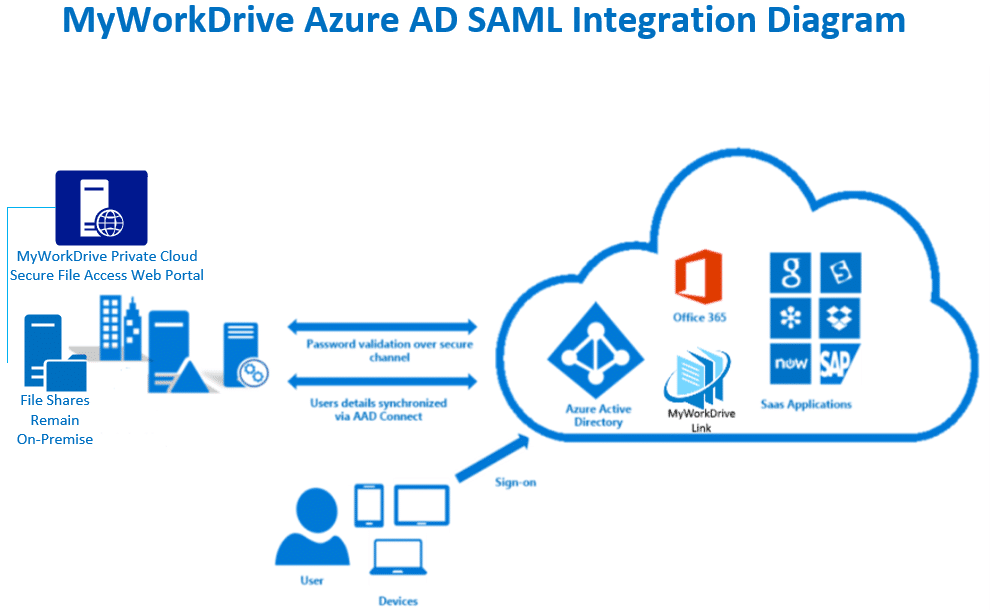
MyWorkDrive supports SAML-based web file manager Single Sign-On (SSO) to Entra ID instead of traditional Active Directory authentication for all necessary logins.
This article covers setting up Entra ID SSO with a public URL. If you wish to use an internal URL, you would want to deploy an Azure Application Gateway.
For SAML, MyWorkDrive acts as a Service Provider (SP) while the Entra ID acts as the identity provider (IDP). In a typical scenario, customers sync their Active Directory credentials to Entra ID. User logins are set to use the same UPN suffix to log in to Active Directory as they do in Entra ID (in most cases, this is the company's Office 365 Subscription).
Configuration using these instructions will permit you to enable/apply conditional access policies for features in Entra, such as Pre-Auth and MFA, to this Enterprise Application.
