MyWorkDrive & Morro Data – NAS In-Cloud and On-Prem
/in News/by MyWorkDrive TeamMyWorkDrive and Morro Data announce that they will collaborate to provide businesses with the most complete Cloud NAS solutions for the hybrid workplace. Users anywhere can now securely access the complete file system at up to Gigabit speed.
With MyWorkDrive & Morro Data, it’s easy to Migrate File Servers to the Cloud without managing complex file share migrations, retraining users, or giving up local access.
With a typical “cloud only” type file service, file shares must be converted and locked-in to the cloud storage vendor requiring a complex migration, retraining of users, sync client deployment, and hefty monthly per user fees. These services also do not allow for fast local access when needed to support power users or designers who need local network speeds to work efficiently.
With MyWorkDrive and Morro Data, these problems are solved. Simply sync file shares to the Morro Data Cloud and connect to them using a MyWorkDrive Server for easy remote access without VPN. Power users and designers anywhere who need to access larger files or collaborate on design files with file locking can connect to a local CloudNAS CacheDrive appliance.
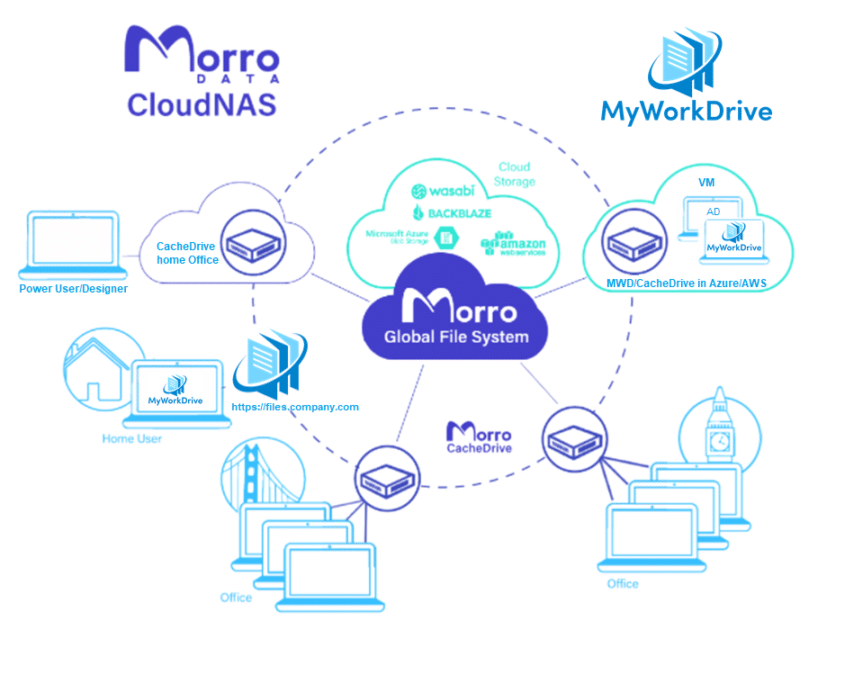
The Best of Both Worlds
When used together, MyWorkDrive and Morro Data provide 100% remote accessibility of files from any Web Browser, Mobile, Mapped Drive or local NAS with Gigabit performance.
MyWorkDrive & Morro Data combined Cloud File Server Benefits:
- Keep the same mapped drives with no training needed
- Simple, automated Migration
- No Servers to maintain on-premises
- Unlimited Capacity
- Reduce cost compared to cloud only services
- Maintain Data Privacy, Control of files and storage location
- Access files at Gigabit Speed with CacheDrive gateways
MyWorkDrive & Morro Data – For a complete solution to all your File Share Remote Access needs!
MyWorkDrive 6.1 Data Leak Prevention Mapped Drive Client Support Released to Preview
/in News/by MyWorkDrive TeamWe are excited to announce the availability of of our new Data Leak Prevention (DLP) view of files in the MyWorkDrive mapped drive clients. With this preview release, users will be able to view and edit files online directly from the mapped drive client – while still being restricted from downloading as configured on the […]
What is the future of Remote Work?
/in blog/by Dan GordonWhat is the future of Remote Work? With light at the end of the tunnel on the Covid Pandemic what does that mean for Remote Work? In our Remote Work article, we reviewed the latest trends and work styles for remote work pre-pandemic. During the Pandemic, remote work has become not only more common but […]
Upgrade Alert Notification
/in News/by MyWorkDrive TeamMyWorkDrive received notice from Cloudflare that Argo Tunnel agents older than 5.5.2020 will no longer be supported as of March 20th. This requires all MWD customers to be running a minimum of MWD Server 5.4.3.2 or higher. Cloudflare is required to Open MyWorkDrive documents in Office online and is also used by customers running […]
Version 6 Client Apps Now Available for Download
/in News/by MyWorkDrive TeamWe are excited to release Version 6 Mac & Mobile clients. Version 6 Server added major new features including; Granular Permissions on shares, Multiple Domains Support, Teams App Support and External Guest User folder sharing. The version 6 Windows Client remains in preview with a production release date expected in the next 2-4 weeks. MyWorkDrive Client […]